As a security consultant at NCC Group, sometimes our clients hire us to perform red team engagements. Essentially, the goal is to sneak into one or more of their office locations however possible (think tailgating, social engineering, even delivering delicious pizzas). Once inside, we use this privileged access to conduct nefarious activities, such as looking for sensitive information (e.g., passwords on sticky notes, IP on printed documents) and gaining persistent access to the internal network.
The word persistent is key here—at some point we’ll need to leave the network, and having to re-enter gives us another chance of being caught. While we’ve used some one-off drop boxes in the past to maintain persistence, we decided we needed to invest in building a high-quality, robust device that can bypass common network protections (e.g., 802.1X).
To that end, we’re excited to announce PhanTap, an easy to set-up, stealthy Network TAP that gives the user a remote foothold in the network they are testing. The source code was publicly released on GitHub July, 31st, 2019 and presented on August 9th, 2019 at the DEF CON 27 Demo Labs.
Read the rest of this post to:
- Gain a high level overview of PhanTap
- Learn about PhanTap’s features, including how it can live stealthily on a network without being detected
- Understand PhanTap’s current limitations and future feature plans
What is PhanTap?
PhanTap (Phantom Tap) is a Network TAP (Test Access Point) that gives its user a remote foothold inside of a network (via the corporate Internet access or a Wireless access point) for further analysis and pivoting. It analyzes traffic on the network and masks its traffic as the victim device, doing so without any other user interaction. The tool is silent in the network and does not affect the victim’s traffic, even in networks having NAC (Network Access Control 802.1X – 2004).
PhanTap can be installed inline between a network device and the corporate network with just limited access to a physical location (e.g., an office building). It has a short, one-time setup—no manual setup is needed after connecting to the network being tested. Available in the OpenWrt repositories, PhanTap can be easily installed on any device running OpenWrt.
PhanTap Features
Learn the victim and the gateway
In order to configure itself, the PhanTap package looks at NTP, DNS, DHCP, and Internet traffic to and from the victim. The most reliable detection option is DHCP. If the device is using a static network configuration, we can assume that, based on the traffic that we see, the victim is the DNS client, the NTP client, or the device with an RFC 1918 IP. The RFC1918 standard defines the network addresses reserved for private networks.
The following example illustrates a network packet PhanTap would introspect in order to learn the victim MAC and IP addresses and the gateway MAC address. PhanTap will analyze the traffic until it sees a packet with a non-RFC 1918 source IP address and an RFC 1918 destination IP address. This traffic corresponds to response packets coming from a public IP address (Internet) and having a private IP address (local network) as the destination. Due to our physical position in the network, the destination will be the victim and, from this packet, we know the victim MAC and victim IP.
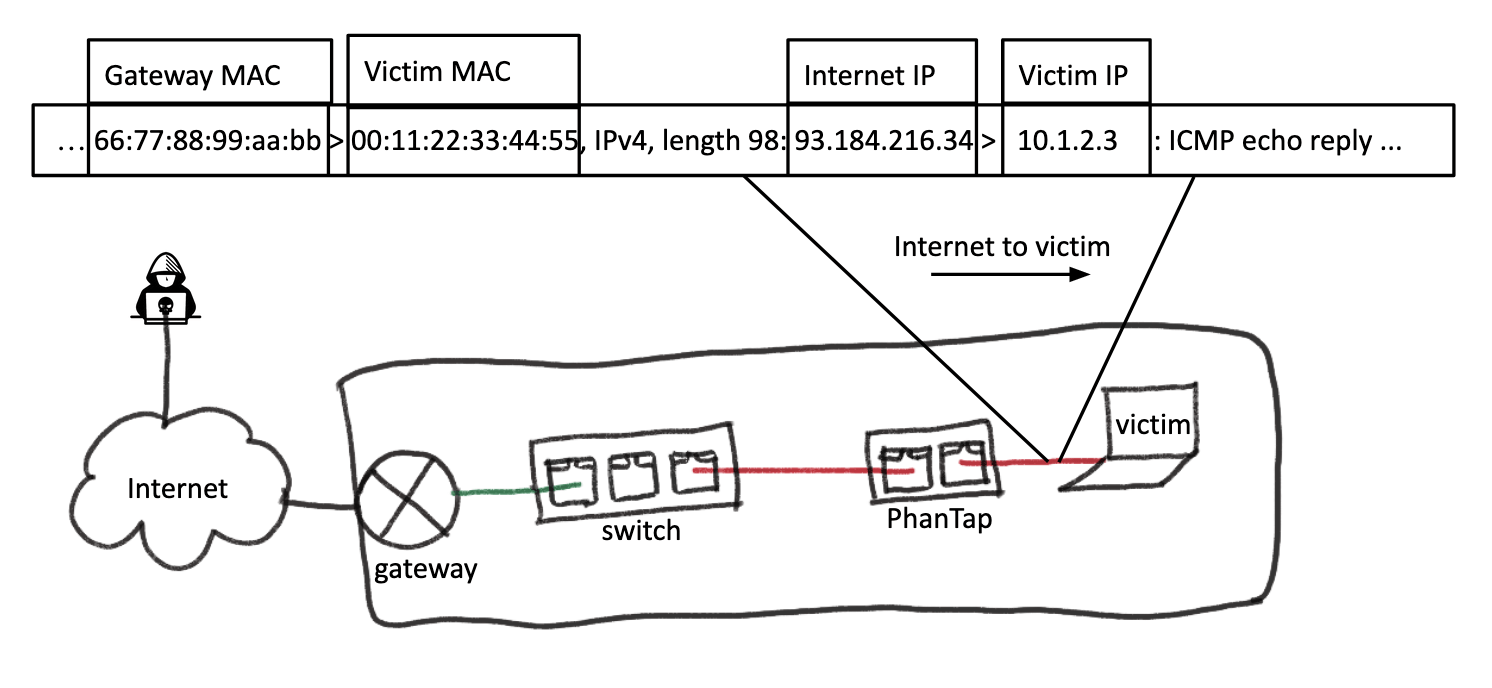
Mask as the victim, talk to the Internet
PhanTap will use the information gathered in the previous step to mask its network footprint as
the victim. It will then make its outgoing traffic appear as if it’s coming from the victim by using the victim MAC and IP addresses. Until the network configuration is done, PhanTap blocks all exit traffic to prevent leaks.
Internally, PhanTap uses “fake” IPs, 169.254.66.100/31 for the Linux bridge and 169.254.66.101 for the default gateway. Setting up the network works as follows:
- Add an iptables SNAT rule to replace 169.254.66.100 with the victim IP
- Add an ebtables SNAT rule to replace the local bridge MAC with the victim MAC
- Add an entry in the neighbour table stating that our default gateway (169.254.66.101) is at the detected gateway MAC
After that, PhanTap can reach the Internet.
In the following images, we illustrate what the contents of a simple ping packet request and response look like from PhanTap after the auto-configuration step. Observe that the PhanTap IP address is the same as the victim IP address detected at the previous step in the request and response packets. Moreover, the response packet is received only by PhanTap and not by the victim, thanks to Linux connection tracking (conntrack). For information on conntrack, see the Netfilter packet flow.
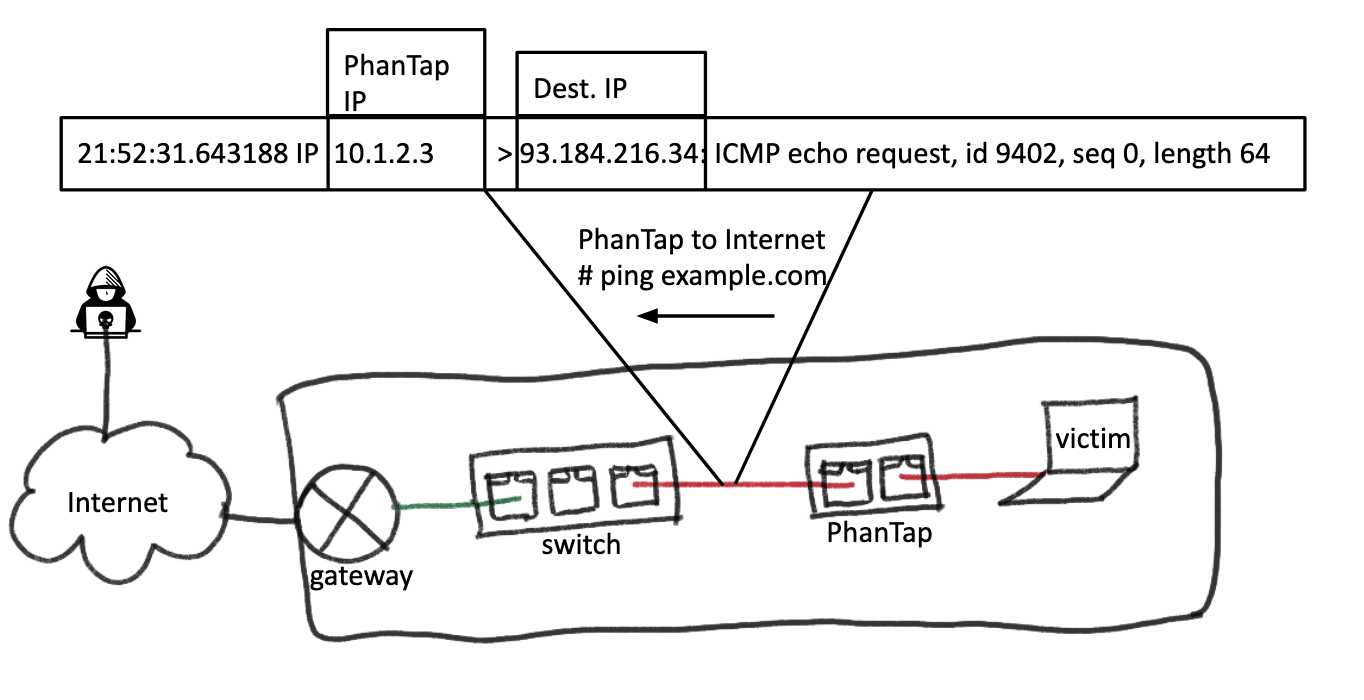
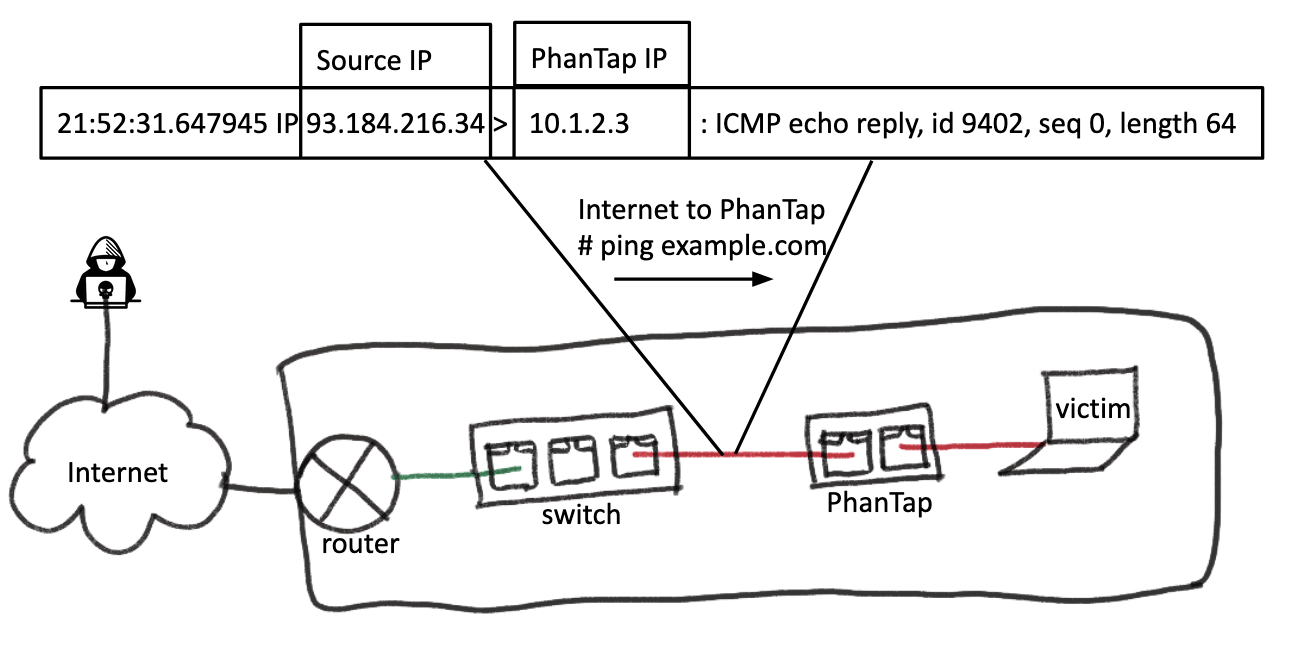
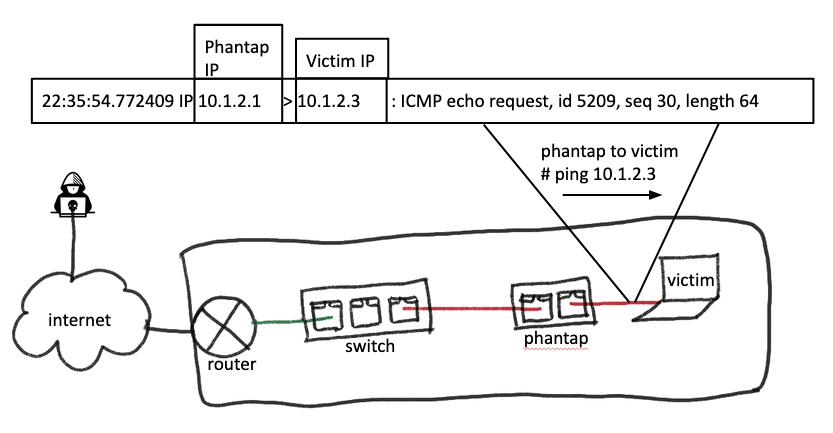
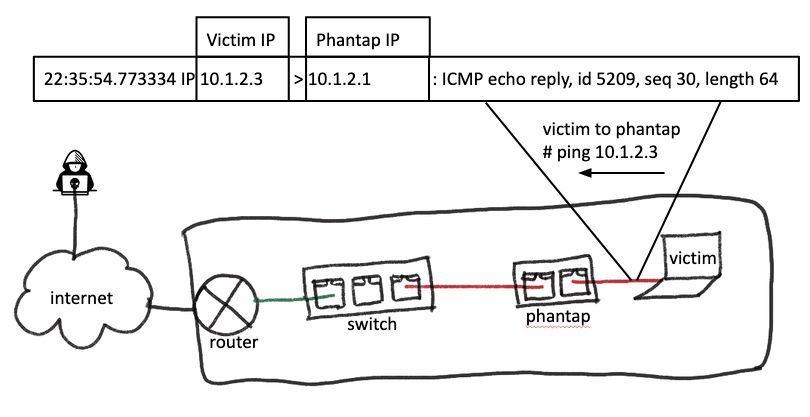
Mask as the gateway, talk to the victim
Similar to masking PhanTap’s traffic as the victim for Internet traffic, the device will mask its traffic when talking to the victim as the gateway. This feature can be observed in the following examples of a ping request and response from PhanTap to the victim.
Learn machines in the network
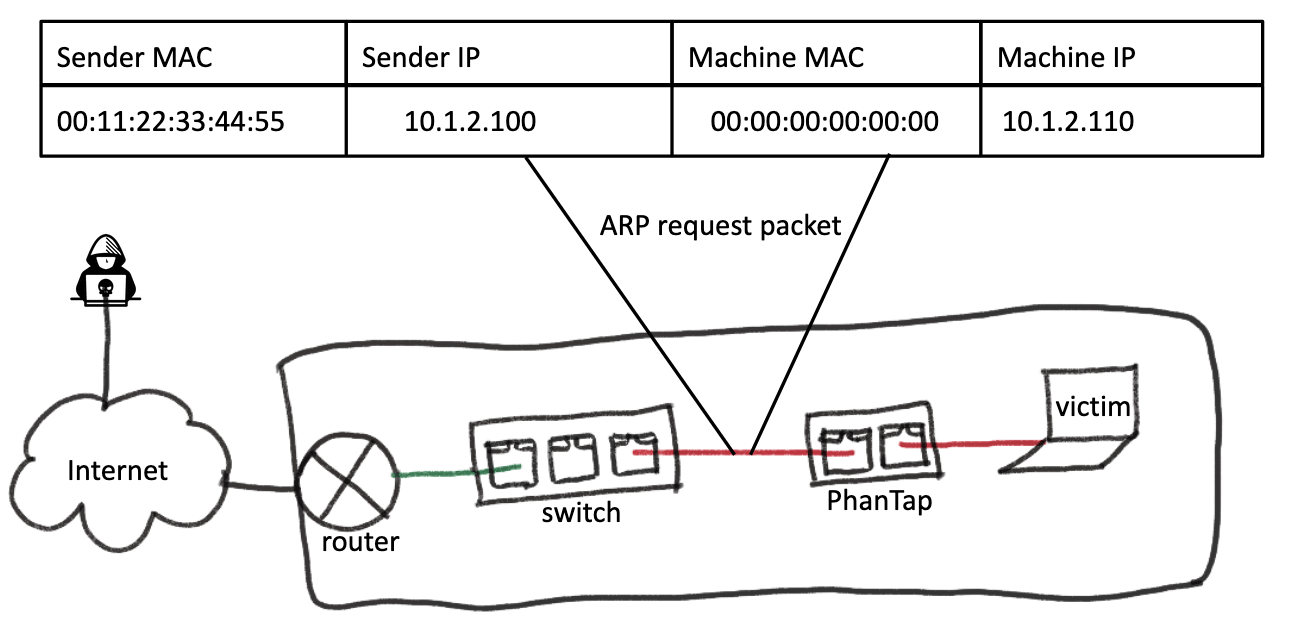
Another important feature of PhanTap is learning the local network machines from multicast and broadcast traffic, hence being able to talk to all the machines in the local network.
In the following example, PhanTap learns from an ARP request packet. With the information in the packet, PhanTap will add a route to the machine IP address and adds the machine MAC address to the neighbour list.
Stealthy
The PhanTap package configures OpenWrt so that no traffic is seen with the PhanTap device’s MAC address. The network interfaces are configured as a transparent bridge and the device will let most traffic through, even 802.1x traffic. ARP, multicast, and broadcast are disabled and the device will also learn the local DNS and NTP and configure itself to use them. As a result, the traffic will not seem suspicious to network monitoring services.
Can run commands
PhanTap can be configured to run specific commands when a new IP or DNS is configured; for example, to restart the VPN service (/etc/init.d/openvpn restart).
Setup
PhanTap is an OpenWrt package that can be installed on any device running OpenWrt. Detailed information on the initial setup can be found in the GitHub repository README.
Limitations, or how PhanTap can be detected
The following two limitations could be detected by a network administrator or network detection tools that have been configured to detect these types of events:
- The GL.iNet GL-AR150 and most inexpensive devices only support 100Mbps, while modern network traffic will be 1Gbps. Thus, PhanTap could potentially be discovered due to the network traffic slowdown or if packets are dropped.
- The network port will stay up, switch side, even when the victim device is disconnected/shutdown.
Also, some traffic is blocked by the Linux bridge (STP/Pause frames/LACP).
Lastly, we make no attempt to change the fingerprint of the traffic we generate; it will be detected as coming from a Linux machine even if the victim machine is running Windows or mac OS for example.
Roadmap
While PhanTap already has a number of useful features and has been used successfully on real red team engagements, there are several improvements we plan to make.
The current version of PhanTap does not support learning network parameters from IPv6 traffic, a feature we plan to add in the short term.
We also plan to:
- Add logic to restart the detection when the links go up/down.
- Test flow offload (software or hardware) optimizations and add appropriate functionality.
In the long term, we’d like to test more hardware devices with features like swconfig vs DSA switches (two different drivers for network switch hardware components).
Conclusion
PhanTap is an easy to set-up, stealthy Network TAP that configures itself and dynamically reconfigures in order to give the user a remote foothold in the network they are testing.
We plan to support this tool and continue to add features like the ones listed in the Roadmap. PhanTap is open source and available to download from the OpenWrt repositories. The source code is available in the NCC Group GitHub repository.
Written by: Diana Dragusin and Etienne Champetier
