Threat mitigation is an important part of the security development lifecycle (SDL) and at NCC Group we have been performing a number of threat modeling workshops focused specifically on the automotive sector.
Considering the increasing research and media attention in relation to connected cars, it is fundamental to understand the threats affecting these new emerging systems and technologies.
In order to assist with the need to secure automotive vehicles, we developed a customised template for automotive threat modeling activities, tailored to the threats affecting the cyber security posture of connected vehicles.
The Automotive Threat Modeling (TM) Template was created using the Microsoft (MS) Threat Modeling Tool 2016 and therefore threat models are created using this product.
Background Motivations: Why the template?
The STRIDE [1] approach has proved to be an effective way to highlight and categorise threats. With the goal to assist with this approach, the MS Threat Modeling Tool 2016 provides a way to use Data Flow Diagrams (DFDs) to identify threats in the design phase of any software/hardware and understand potential attacks based on the identified threats.
A threat modeling workshop for automotive-related technologies requires DFDs with custom elements, tailored threats and specific recommendations. The lack of a specific template for automotive threat modeling brought about the development of the Automotive TM Template, which takes advantage of a new feature in the MS Threat Modeling Tool 2016 that allows the creation of entirely new customised templates.
The Solution and its Features
The template permits the creation of specific automotive threat models with:
- Processes and Data Stores related to the components of connected cars.
- External Interactors tailored to an automotive system.
- Data Flows that correspond to the messages exchanged over the air or inside the vehicle itself.
- Trust Boundaries that take into consideration the environment and the vehicle-to-vehicle (V2V) networks.
- Threat Types and Categories that follow the STRIDE classification, based on known and potential threats to the connected cars’ components.
Tailored Threat Properties including:
- Priority, based on the risk of every threat applied in its context.
- Attack Methods to potentially exploit the identified threats and to help further with the creation of Attack Trees.
- Recommendations that suggest how to mitigate the threats.
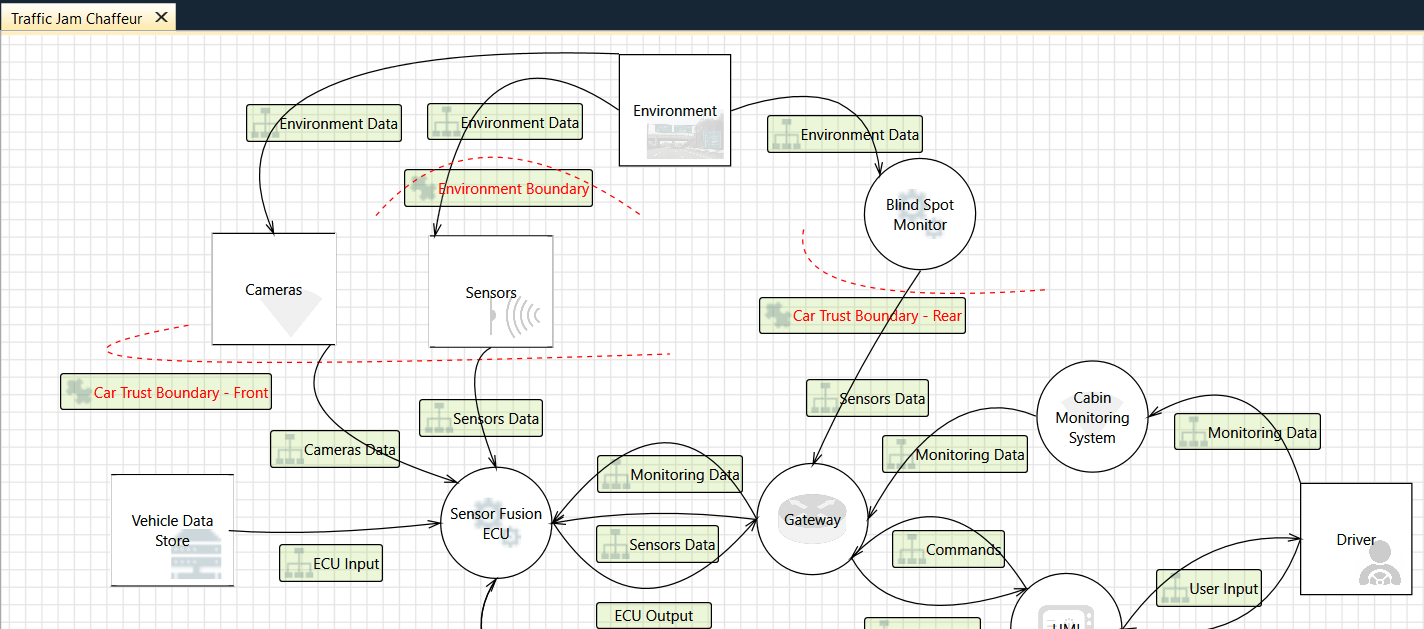
The following screenshot provides a view of a sample threat model created using the template:
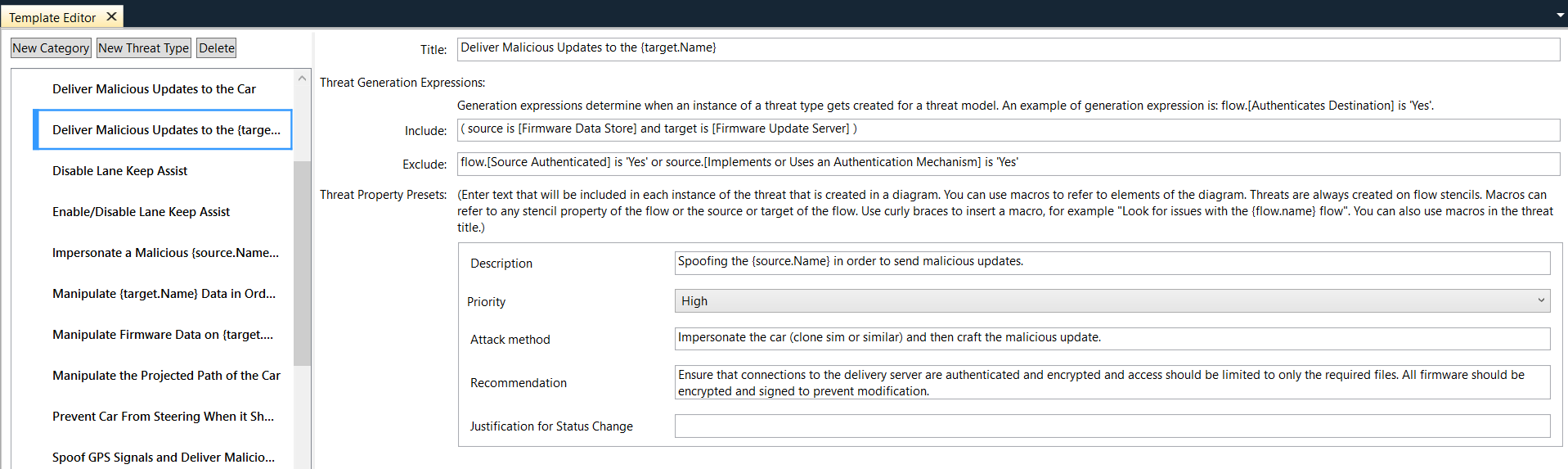
The following screenshot shows the template itself and a specific threat type that was added:
The Results
During a number of automotive threat modeling workshops, the template has been used to provide our clients with a view of the threats and attacks to their automotive systems.
We have created various threat models for different technologies and connected car platforms from SAE [2] Level 1 of Driving Automation (non-autonomous car with some assisted driving modes), up to SAE [2] Level 5 of Driving Automation (full automation with the “system” that monitors the driving environment).
The threat modeling, in conjunction with our security assessment activities (for both software and hardware), have proven an effective way to increase the security assurance of automotive technologies, architectures and products.
Download the Template
The Automotive Threat Modeling Template can be downloaded from:
https://github.com/nccgroup/The_Automotive_Threat_Modeling_Template
Further Developments
The benefits we have gained from creating automotive threat models using our customised template have highlighted the need for new templates such as one for Internet of Things (IoT) products and technologies, which we are currently developing.
Engaging with NCC Group
For more information about threat modeling and our automotive cyber security services, please visit: https://www.nccgroup.trust/automotive/.
To contact us directly, please use: AutomotiveSecurity@nccgroup.trust
References
[1] https://msdn.microsoft.com/en-us/library/ee823878(v=cs.20).aspx
[2] http://www.sae.org/misc/pdfs/automated_driving.pdf
Written by Christiano Corradini
First published on 20/07/16
