Introduction
With the festive season currently in full swing, it is easy to get lost in people’s generosity and giving spirit. Many cyber criminals are currently taking advantage of this fact, and so is NCC Group’s red team, but with a difference – we are providing simulations of an attack which could result in a not so Merry Christmas for some organisations and individuals.
Jingle Shells
One of the main aims of a cyber criminal is to gain the ability to execute commands on a victim’s computer. The ability to execute commands remotely on a compromised machine is often referred to by hackers as a “shell”.
This is useful for an attacker, because it gives them the ability to steal sensitive or confidential information from the compromised computer, install malicious software such as ransomware (aimed at extorting money out of the victim by demanding a ransom for safe return of their files), or use the compromised machines as part of a botnet of multiple (sometimes hundreds or thousands) compromised machines, which can then be used to launch further attacks, such as distributed denial of service attacks.
This blog post describes a number of Christmas-related campaigns carried out by NCC Group’s red team as part of a recent engagement.
These were all extremely successful, and resulted in the compromise of a large number of machines within the client’s corporate network. In a real-life scenario this could be devastating for an organisation, and could have a huge impact at arguably the busiest time of year for most of our clients.
Season’s Greetings – Malicious Media
NCC Group carried out a physical malicious-media campaign, in which booby-trapped DVDs were created which, when inserted within a victim’s computer, would abuse the autoplay feature of Windows in order to play a Christmas-related video, while unbeknown to the victim their computer was compromised remotely and connected back to NCC Group’s command and control infrastructure, Hive. At this point, the consultants would have full remote access to the victim’s machine, and thus remote access into the client’s corporate network. If this had been a real-life attack, it would be game over.
Due to the high success rates of email-based spear-phishing, these physical malicious-media campaigns are not as common as their email-based counterparts, and would usually only be used by cybercriminals as a last resort (for example, if the target is air-gapped, or not easily accessible via email); however, the test was carried out in order to show the effectiveness of such a campaign, and staff’s willingness to voluntarily insert untrusted media in their computers.
A Christmas Gift With a Hidden Surprise…
In order to have the DVDs inserted, and have their payload run, the consultants would need an excuse for the users to be receiving DVDs in the first place. What better excuse than Christmas?
The malicious DVDs were branded with some client-related logos, and placed inside Christmas cards, which were then posted out to the users with a simple Christmas message inside. This could have been something else, such as a DVD with the words “Christmas party pics” or “Staff Christmas bonuses” displayed on the front; but in the season of goodwill, we thought a Christmas card would be a nice touch.
Below is an example of a little Christmas gift, packaged by our miniature NCC Group elves:

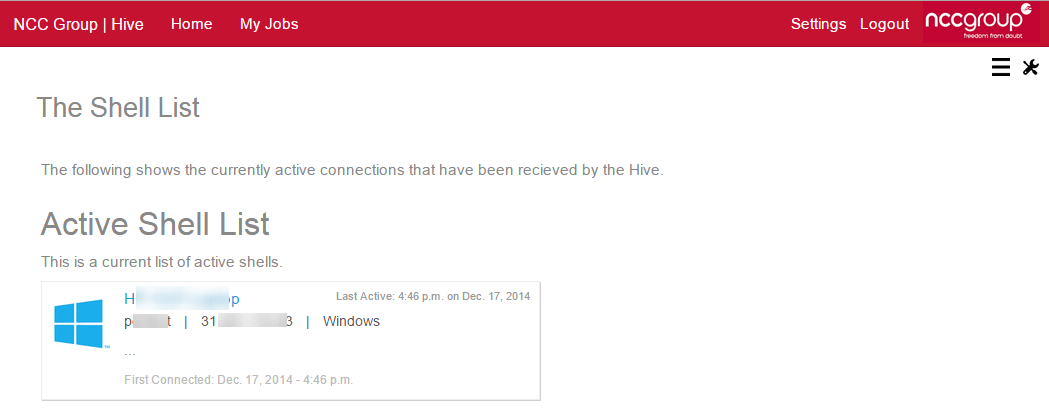
The screenshot below shows an example victim connecting back to Hive, providing our specialist consultant access to an organisation’s network simply by the victim inserting the malicious DVD and clicking on its icon.
Depending on the scope of the assessment, this connection could then be used to simulate a real life attack, compromising the organisation’s domain and exfiltrating sensitive information and files.
A Time for Giving – Christmas Employee Benefits Campaign
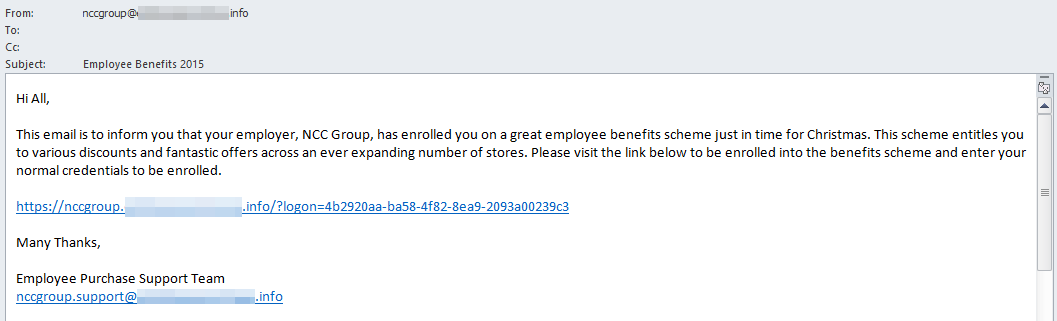
This time of year everyone wants to save some money, so NCC Group created a fake employee benefits website in order to entice victims. The phishing email sent out to the users requested that they enter their normal credentials in return for some Christmas discounts.
Once a victim clicked on the link, they would be taken to a login page, as shown in the screenshot below. This page included the target organisation’s logo, modified to emphasise it being Christmas.
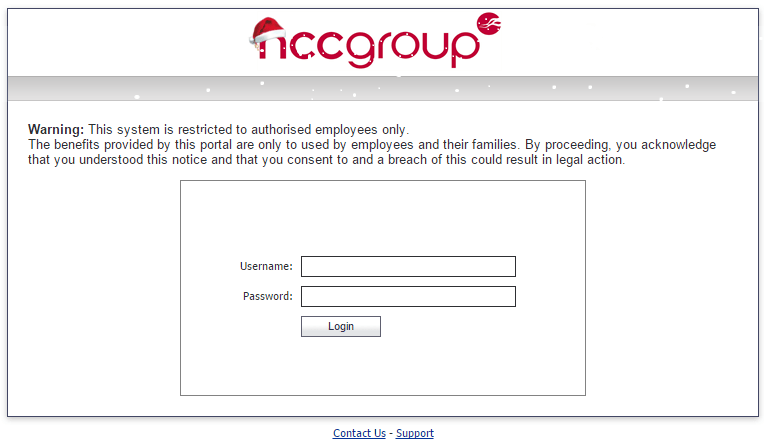
Using this technique, NCC Group was able to capture a number of users’ credentials – an average of approximately 64%.
A number of the organisations against which this technique has been used were found to have external login portals accessible to the Internet. A majority of these portals did not employ a form of multi-factor authentication enabling us, the attacker, in the worst case to gain access to the internal network through a VPN, and in a majority of cases, gain access to users’ mailboxes.
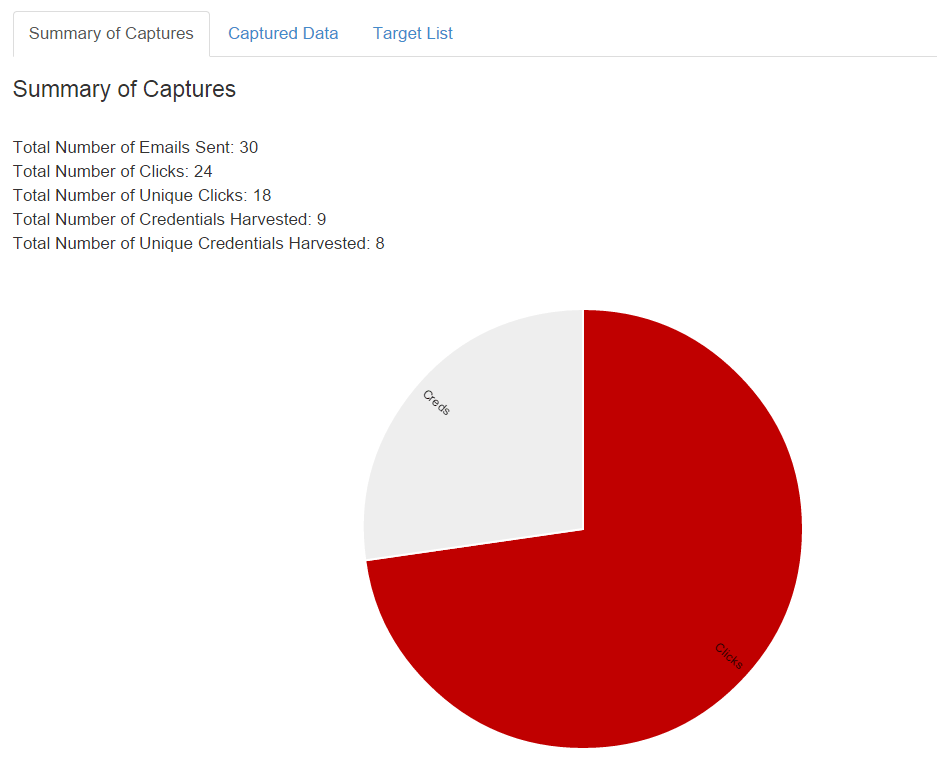
This process was automated using NCC Group’s in-house phishing platform, Piranha. This meant it was possible to create a new phishing site, along with a customised domain and SSL certificate, and launch an email-based spear-phishing campaign within a matter of hours. The NCC Group consultants could then use Piranha’s reporting dashboard to track individual clicks and credentials as they were entered in real time. The screenshot below shows the summary of the results from a phishing campaign.
Have a Safe Christmas
NCC Group hope that this post helps you understand the risks that these targeted attacks can pose in a real-life scenario, especially at Christmas when we all let our guard down. We would like to wish you a Merry Christmas and remind you to stay safe.
Published date: 17 December 2014
Written by: Richard Warren and Shaun Jones
