tl;dr
One true constant (until someone schools me and ROP etc. not withstanding) is that threat actors need executable memory of some kind for their endpoint implant even if fleeting. Given this we’ve released an open source Microsoft Windows Service that aims to facilitate detection of anomalous executable memory via:
- Scanning all processes every 30 seconds
- Noting the differences in executable memory pages
- Reporting the differences via Windows Event Logging to allow forwarding to analytics platforms
Hypothesis
Collect enough telemetry from a Windows host or an entire estate on which processes create or change memory so its executable along with their size and you’ll be able to spot the anomalies. These anomalies may be malicious activity.
Inspired by Sysmon – Telemetry
We have a number of data science driven initiatives both in applied research and Managed Detection Response operations related to threat detection. To support these initiatives we need raw telemetry about system behaviors when developing new models. We wanted a way to performantly collect telemetry around changes in executable memory posture to see if we can detect process injection/hollowing among others. The quickest way to prototype this functionality was via a userland process that snapshotted, diffed and wrote the findings to Windows event logging.
Performance overhead
The performance overhead on a Intel Core i7-7660U running at 2.5Ghz is a 25% CPU spike for about 8 seconds. Initial feedback from researchers within NCC Group who have deployed it appears to be there is no discernible performance impact even on somewhat constrained virtual machines. But as they say – your millage may vary.
In terms of log size 1MB of log will give you about a 10 minute window of deltas. So you can extrapolate from that about 6MB per hour per host.
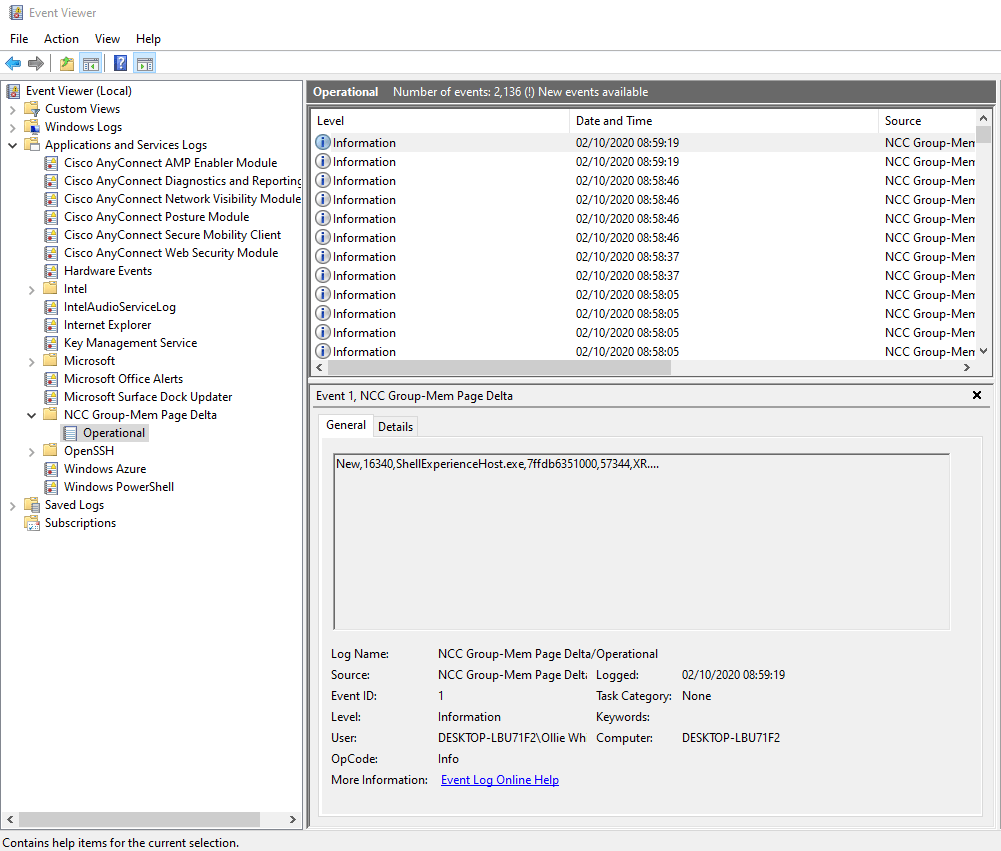
In action
The below shows the service in action and the resulting event log. The entries are intended to be machine readable and thus are CSV formatted (refer to the Github repo for the breakdown in fields).
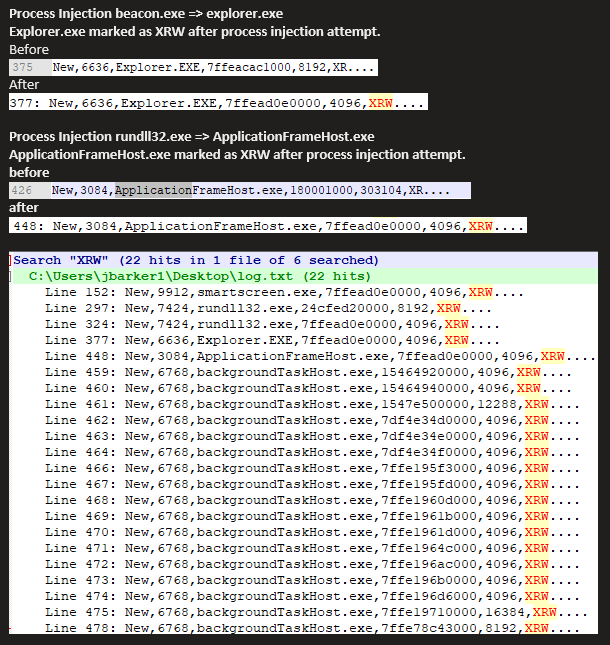
Proof of value
Earlier this week I worked with NCC Group’s Full Spectrum Attack Simulation team to test an early version to see in practice with a known signal would we see the related raw events. They ran a number of experiments – the below being an example of where we caught the change.
Exercise for the reader
We appreciate in of itself the raw telemetry provides little value so the following are left as an exercise for the reader.
- Forwarding the relevant Event Log to your analytics infrastructure
- Analyzing said stream for anomalies
- Putting on your super hero outfit as you find a latent implant
Source and binary
You can download it here:
- Github Repo https://github.com/nccgroup/WindowsMemPageDelta
- Github Release https://github.com/nccgroup/WindowsMemPageDelta/releases
Feedback
As always we value feedback – you can get me via the following:
- Twitter: @ollieatnccgroup
- E-Mail: ollie dot whitehouse [at] nccgroup . com
- Bug reports / feature requests via Github issues: https://github.com/nccgroup/WindowsMemPageDelta/issues
Thanks
Thanks goes to the following individuals inside of NCC Group:
- Woody in the Full Spectrum Attack Simulation team for testing and experimentation
- Axel in the Research Intelligence Fusion Team for collaborating on making threat actors lives a little more complicated through various memory scanning and analysis shenanigans
History
Part of this project is based on code I originally wrote in 2014 for the detection of patches to the .text section in memory compared to that on storage. You can find the original code here – https://github.com/olliencc/WindowsPatchDetector
