TL;DR
A full technical note explaining the analysis of a Flash file part of the Neutrino Exploit kit has been uploaded to our Cyber Defence Github repository.
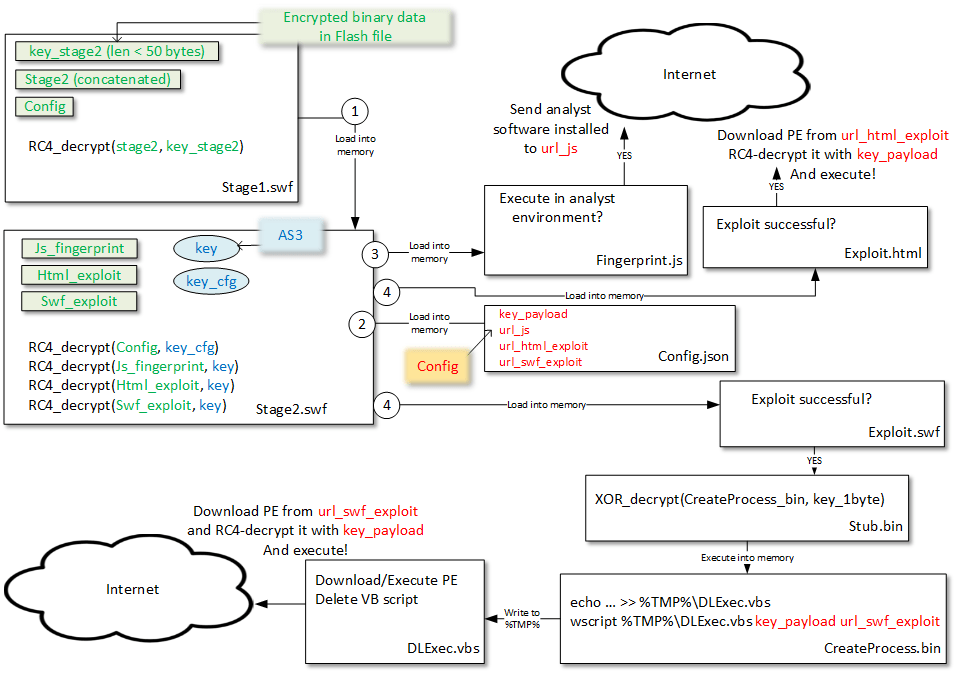
This document details a methodology to analyse all components of the original Flash file. It details how we manually deobfuscate most of its components and refers to many Python scripts developed to assist our analysis.
A Glimpse of Our Latest Adventure
The original Flash file (stage1.swf) was delivered after the browser specified its Flash version and there was traffic after the Flash file, indicating some degree of execution / success.
The original Flash file is obfuscated which makes static analysis difficult. It contains encrypted blobs stored in Flash binary data. The decryption algorithm is identified as RC4 and the RC4 key can be identified easily as they are strings in the Action Script decompiled code. Therefore, the encrypted blobs are decrypted:
- “
loadBytes;removeEventListener;stage;contentLoaderInfo;addChild;addEventListener” is part of the obfuscation and is a list of strings – decrypted at runtime. stage2.swfis the result of decrypting the concatenation of several blobs.cfg.txtis the configuration file containing the URLs to be executed after the final exploits. This file is actually passed encrypted to stage2.swf which uses another RC4 key to decrypt it.
The intermediate Flash file (stage2.swf) is also obfuscated. It also contains RC4 encrypted blobs. The following encrypted blobs are decrypted:
4_res_js_rc4.js: fingerprinting JavaScript to detect if it executes in an analyst environment. It detects if one of the following software is installed: Bitdefender, ESET NOD32, Wireshark, VirtualBox, FFDec, VMware, Fiddler2.1_nw22_swf_rc4.swf: CVE-2015-8651 Flash Integer overflow exploit.2_nw23_swf_rc4.swf: CVE-2016-1019 Flash type confusion exploit.3_nw24_swf_rc4.swf: CVE-2016-4117 Flash exploit.6_nw7_swf_rc4.html: CVE-2014-6332 IE OLE Automation Array RCE.7_nw8_swf_rc4.html: CVE-2016-0189 IE Scripting Engine Memory Corruption.5_nw2_html_rc4.html: Other IE exploit.
The payload is a shellcode that XOR-decrypts a second shellcode. The second shellcode accesses the PEB and parses the list of modules to resolve the CreateProcessA address. Finally it writes a temporary file containing a Visual Basic (VB) script and executes it. The VB script is obfuscated and is a simple Download/Execute PE file payload. Each exploit uses a different URL as stated in the cfg.txt configuration. All the exploits RC4-decrypt the remote PE file using a single RC4 key also stored in the configuration. The RC4 key is specific to the original Flash file. Another Flash file would have another key.
A neutrino.py script based on pyswf allows us to automatically extract all listed files for further analysis.
The fingerprinting JavaScript can be tested after enabling a hidden debug feature that allows every test to be logged in the JavaScript console. All the exploits (Flash and IE) can be tested independently after having setup the URL and RC4 key in the respective files.
All the components of the Flash file are summarized in the following figure:
Written by Cedric Halbronn
First published on 22/08/16
