Category: Reduction/Prevention
Overview
Document macros have gone in and out of style since 1995 as a deployment method for malware. Netskope’s latest ‘Cloud and Threat Report: July 2021 Edition’ points out that in Q2 of 2021, Microsoft Office macros accounted for 43% of malicious Office document downloads, compared to just 20% at the beginning of 2020. Malicious Office documents, aka maldocs, have continued to be an issue for organizations. Emotet, a successful malware family taken down in 2020, heavily used Office macros to infect Microsoft Windows systems. Other malware groups seemed to have taken a page from the Emotet playbook and increased the use of macros in their recent campaigns of 2021. Today let us take a look at the various methods of detection and prevention of malicious macros.
Enabled Macros by Default
Microsoft Office by default allows a user to enable content and allow macros to run when opening Office documents like Word, Excel, and even PowerPoint. Macros or enabled content is rarely used by most users, and typically just a handful of users needing or using Excel financial calculations. Most organizations are scared or uncertain about what will break if macros are disabled. Creating a communication plan informing the organization about the upcoming change and providing a way for users to request and justify the need for macros, get any needed approvals, and required training can help avoid significant adverse impacts to the organization once implemented.
Detection
Detecting the use of macros within Office programs is not easy as there are no logging events associated with macro usage. The only option is to look for programs executed after the launch of Office programs. Often malware will use the macro to launch a scripting engine such as cscript, wscript, or other scripting languages. Additionally, PowerShell, WMI, or other administrative Windows utilities have also been used in this context. Endpoint Detection and Response solutions (EDR) usually monitor these parent-child relationships and trigger when Office documents attempt to execute nonstandard programs. Similarly, an organization with robust and proper logging of endpoint behavior can build detections within their log management or SIEM solution to highlight odd Office document executions.
Reduction/Prevention
The best and easiest option to reduce the likelihood of malicious Office documents crippling an organization with malware or ransomware is to disable Office macros and create an allow list for users that absolutely need macros or enabled content. Users with exceptions to run macros or enabled content should be a priority to monitor for maldoc behavior through suspicious parent-child Office executions.
Blocking all Office documents from coming into the organization is not feasible due to the widespread usage of Microsoft Office products. However, some email scanning gateways offer maldoc scanning at an additional cost and can effectively reduce the sheer quantity of malicious Office documents an organization receives. Alternatively, implementing an EDR solution is also a viable option.
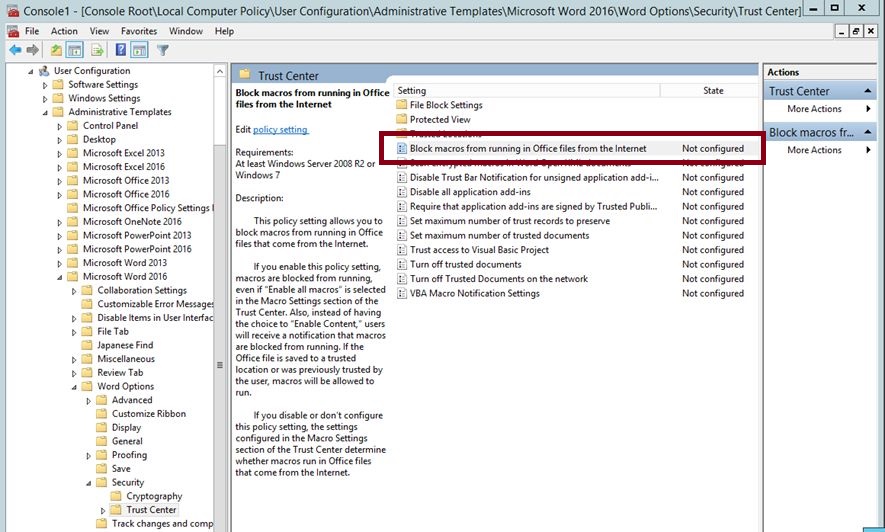
Disabling Office macros is the easiest as it is FREE and already built into Microsoft Active Directory as a Group Policy object. The image below depicts the setting to disable Office macros.
Organizations can utilize user groups for those exceptions that still require macro functionality. However, keep in mind that those specific users should be provided additional awareness training on the ramifications of opening malicious Office documents and enabling content.
Use the Registry to block macros
For those that do not have Active Directory, blocking macros can also be achieved by adding a registry setting to each system to disable macro usage. Set the following keys to achieve macro blocking and be sure to adjust the appropriate Office version, e.g., “15.0, 16.0, etc.”:
- HKEY_CURRENT_USERSOFTWAREPoliciesMicrosoftoffice<16.0>wordsecurity
- HKEY_CURRENT_USERSOFTWAREPoliciesMicrosoftoffice<16.0>excelsecurity
- HKEY_CURRENT_USERSOFTWAREPoliciesMicrosoftoffice<16.0>powerpointsecurity
In each key listed above, create the following value:
- DWORD: blockcontentexecutionfrominternet
- Value = 1
Conclusion
We hope this blog entry helps provide an option to reduce the risk of infection from ever-increasing malicious Office documents and some things to consider when implementing the change. With some preparation, communication, and education, an organization can reduce the likelihood of getting infected by maldocs with an existing FREE option available to all Windows users.
References and Additional Reading
- Netskope’s ‘Cloud and Threat Report July 2021 Edition’ – https://go.netskope.com/rs/665-KFP-612/images/2021-07-Cloud%20and%20Threat%20Report-RR-474-1.pdf
- Emotet Takedown – https://www.fbi.gov/news/stories/emotet-malware-disrupted-020121
- Disable Macros – Center for Internet Security – https://www.cisecurity.org/white-papers/intel-insight-how-to-disable-macros/
- Disable Macros using the registry – https://gist.github.com/PSJoshi/749cf1733217d8791cf956574a3583a2
- Enable or disable macros in Office files – https://support.microsoft.com/en-us/office/enable-or-disable-macros-in-office-files-12b036fd-d140-4e74-b45e-16fed1a7e5c6
