For people who regularly conduct internal penetration tests on Windows domains, typically you will see common issues arise such as common passwords. If you are able to obtain a local administrator hash, in most instances you can normally compromise the entire domain. Typically the hash will be common with other devices and you will find a domain administrator logged in that can be impersonated, compromising the domain.
This can sometimes be quite a manual process if you are dealing with a large number of hosts that have common local administrator passwords. If for instance you have compromised a device and obtain the local administrator hashes and find that these match with over 2,000 other devices, how do you then quickly find if a domain administrator is logged in on one of them?
A typical approach which works very well is the following:
- Obtain a hash file.
- Pass the hash using a tool called Keimpx or use the Metasploit SMB Login module.
- Find where the hash matches.
- List the tokens logged into each system that match the found hashes using tools such as Incognito.
Incognito is a great tool that is also built into Metasploit, which allows you to impersonate tokens. The binary version of Incognito also includes a tool called find_token.exe which allows you to find tokens around the network with valid local administrator credentials, but does not accept a hash value. If you can’t crack the hash value (which you will find more and more in Windows 2008 networks) and can’t obtain the clear text password, a way around this is to impersonate the hash locally using WCE (Windows Credential Editor), then use find_token.exe to look for tokens. The main issue being that there are quite a few steps and if you have lots of different hashes you have to carry out the process for each hash. The find_token tool will list all users logged in, including local users, so a lot of manual checking needs to take place on a large network with many matches to compare and work out who is the domain administrator.
I wanted a quicker and more automated way to pass a single hash, a list of hashes, or even give clear text credentials; give it a list of IP addresses or a range, and look for common credentials. If the tool finds common credentials on devices, then list where the domain administrator account is logged in. Typically it is not as straight forward, as the domain administrator account is always DOMAINAdministrator – there typically are many domain administrators, all with unique naming conventions.
Introducing the EasyDA Windows Domain script. A simple bash script that accepts a hash, list of hashes or credentials and will search for common credentials and then list who is logged in. It can compare the users to a list of domain admins you may have obtained, or a particular user you are interested in and tell you if and where they are logged in. It is then as simple as connecting to that system and impersonating the token, steal the process or dump the domain administrator’s password in clear text.
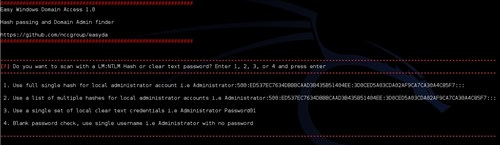
It is menu driven, so it is very easy to use. The only dependency is to have Metasploit installed (http://www.metasploit.com).
The format of the hashes it accepts are the standard type you will obtain using Metasploit Hashdump, FGdump, Gsecdump, WCE, PWdump etc. You can supply the script a single hash, or a list of hashes as below:
admin1:1003:624AAC413795CDC1FF17365FAF1FFE89:3B1B47E42E0463276E3DED6CEF349F93:::
Administrator:500:ED537EC7634DBBBCAAD3B435B51404EE:3D0CED5A03CDA02AF9CA7CA30A4C85F7:::
testadm1:500:ED537EC7634DBBBCAAD3B435B51404EE:3D0CED5A03CDA02AF9CA7CA30A4C85F7:::
testadm2:500:ED537EC7634DBBBCAAD3B435B51404EE:3D0CED5A03CDA02AF9CA7CA30A4C85F7:::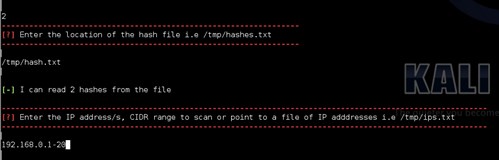
You then supply the script a list of IP addresses, ranges or CIDR ranges just as you can with tools such as Nmap and Metasploit.
The script will then scan all the supplied IP addresses using the hashes or credentials and look for common matches.
As can be seen below common credentials were found on multiple devices.
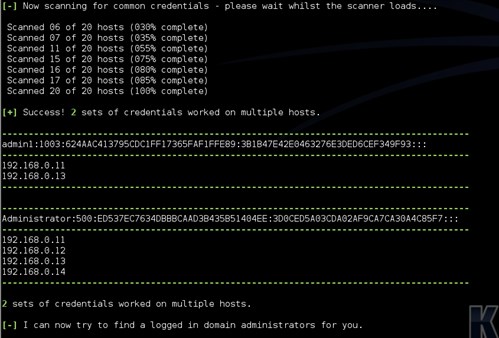
The script can then search for logged in users on the devices where common credentials were found.
To make things easier you can supply the script with a list of domain administrators to compare to and will help you identify which user logged in is a domain administrator. This is required because your test system is not on the domain and can’t look this up for you on the domain controller. Typically, you may have access to a system compromised, or for other testing such as a build review that is on the domain where you can obtain this list.
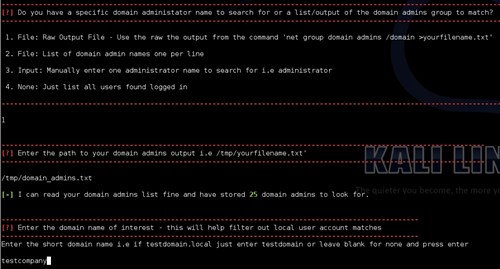
You can pass the script the raw output from the following command in a text file.
net group "domain admins" /domain >domain-admins.txt
Output file it can be given in its raw format.
The request will be processed at a domain controller for domain testcompany.local.
User accounts for testdc.testcompany.local
-------------------------------------------------------------------------------
Administrator bob_adm Exch_adm
Exch2 Exec1 Guest
krbtgt steve_adm SUPPORT_388945a0
test_adm
The command completed successfully.The script will sort the list and read this in automatically for you.
You can also supply a simple list with one user per line like below, or just enter a username manually.
Administrator
Admin
Sysadm
Test_adminIdeally it is best to give the script the domain name of interest. This will help remove any local users being returned and makes the results easier to read. If you do not know this, it does not matter and it will just return all users logged in.
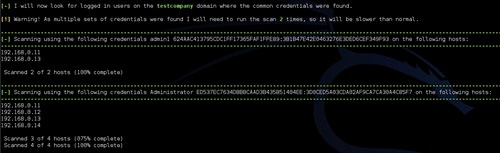
The script will then connect to each IP address with the set of credentials that were valid and list any logged in domain users.
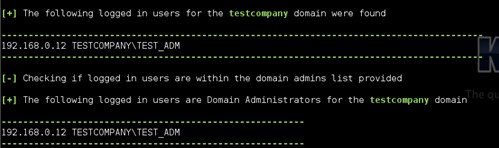
In the above example, the user TEST_ADM from the TESTCOMPANY domain was found logged in. This was then compared to the supplied domain admins list and verified as a domain administrator.
Once you then know where the domain administrator is logged in, it will be as simple as connecting with tools such as Metasploit and impersonating the token with Incognito, stealing any process running, dumping the clear text credentials with Mimikatz. If you should run into Anti-Virus detection, you can always use the Incognito binary itself (not within Metasploit) and directly launch a domain administrator command shell; this does not tend to get picked up as much.
The Script
If you’re interested in the script is can be obtained from the public NCC Github repository here:
https://github.com/nccgroup/easyda
Published date: 30 May 2013
Written by: Daniel Compton
