TL;DR
Checkout here!
Motivations
It has become challenging to follow when certain mitigations are added in an update and/or backported to some older versions of various software and hardware.
Sometimes, online content becomes deprecated due to mitigation changes and it can be hard to keep up. Also, it is easy to forget after a short time if you don’t work on a specific software/hardware.
We have been filling this gap by tracking all the mitigations in summary tables that hold the mitigations names and linking to online references to get technical information about them.
The shared information has demonstrated to be useful for several years to exploit developers.
Summary tables
An example is the following:
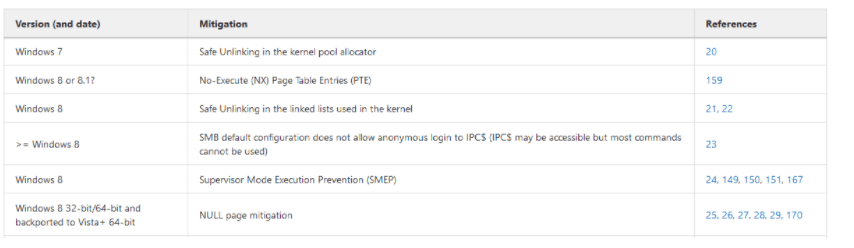
Does my current environment have mitigation X?
This is a common question any exploit developer may have when trying to develop an exploit for a given target.
E.g. let’s say you want to exploit a Windows kernel driver on Windows 7 x64 containing a kernel NULL pointer dereference bug. Is it exploitable?
Checking our table, we read the “NULL page mitigation” was introduced in “Windows 8 32-bit/64-bit and backported to Vista+ 64-bit“. Now we know it depends if our target Windows 7 x64 is up-to-date or not, more precisely, we can focus on figuring out which KB introduces this mitigation and check our target against that KB!
Community-driven knowledge
Today we have decided to give back to the community and share our mitigations tables. Go check them out here! The most complete one is the Windows mitigation table but we have created a template with partial information for many other targets.
Feel free to submit any pull request!
