One of the most frustrating issues that Digital Forensics and Incident Response (DFIR) consultants encounter is a lack of forensic data available for analysis. This article aims to mitigate such situations by providing key considerations for improving forensic readiness.
To conduct a forensically sound investigation, several prerequisites must be met. These requirements can vary, but the most common requirements are the following:
- Operating System Logs: Relevant logs from systems such as Windows, Linux, or macOS, covering the time period of interest.
- Network Device Logs: Logs from firewalls, proxies, VPN servers, and other network devices that can help reconstruct the timeline of events.
Cloud computing offers significant advantages, including scalability to adjust resources based on demand, cost efficiency by paying only for what you use, and accessibility from anywhere with an internet connection. It also ensures systems are always up to date with automatic updates and provides robust disaster recovery options to protect data.
However, there are some inherent challenges. Security concerns arise from storing data off-premises, and reliance on internet connectivity can lead to disruptions during outages. Users often have limited control over the infrastructure and face potential hidden costs from data transfer fees and additional services. Cloud computing offers specific capabilities related to the log retention period, and many decisions must be made about log customisation. If the availability and quality of the logs are not driven from a forensic perspective, security incident investigations may be severely hampered.
Logging Considerations:
1.Timestamps: Accurate, synchronised timestamps for each log entry to establish a reliable event timeline.
2. User Activity: Details of user logins, logouts, and any changes to user accounts or permissions.
3. System Events: Records of system start-ups, shutdowns, and any system errors or crashes.
4. Network Activity: Logs of network connections, including IP addresses, ports, and protocols used.
5. File Access: Information regarding file creation, modification, deletion, and access, including the identity of the user performing each action.
6. Application Logs: Logs from critical applications, such as web servers and databases, to track their operation.
7. Security Events: Logs of security-related incidents, such as failed login attempts, changes to security settings, and detected threats.
8. Audit Logs: Records of administrative actions and system configuration changes.
Cloud container-based architectures may amplify this lack of forensic readiness, because logs from systems might only be available locally during the container's runtime. The cloud computing's ephemeral nature offers significant benefits that must be considered during the design phase. Containers provide functions that process, store or forward data of a sensitive nature (financial, intellectual property or privacy related) must be configured to retain appropriate forensic data for post-incident investigations.
Forensic Investigation in Cloud Environments:
The forensic investigation typically starts after receiving a full disk image containing the operating system hosting the containers infrastructure, which might be a Linux server.
The Docker containers are created dynamically, and all the content is deleted after each container lifecycle. The method to give persistence to the logs within the Docker is by creating a log volume that will persist after the container's lifecycle. Otherwise, anything not contained within the containers running within /var/log/docker/ containers will be lost.
Furthermore, during a security incident, application logging can provide the ability to identify if and how the application was impacted by whom, and what specific actions occurred. This information will help determine the overall application activity of a threat actor and what the potential impact to the organisation may be from a data loss standpoint.
Below there is an example of the YAML code used with Docker Compose for a server:
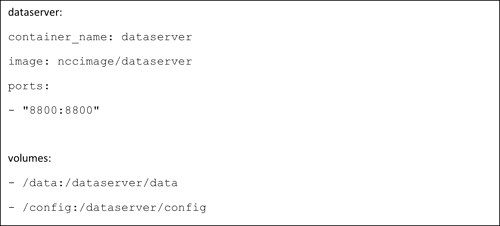
While the configuration above defines two volumes, none of them are mapped to affect the system log's location, i.e. /var/log/.
In the same way, application logs were not preserved either. The application supported by a container architecture should store specific logs as well, just in case are required for the incident investigation. These logs should be exported properly following the guidelines provided by the specific application.
Both system and application logging locations should be preserved by creating a log volume, hence mapping them in the hosting operating system.
Recommendations for Forensic Readiness in Cloud Environments:
1. Design for Forensic Needs: Organisations should consider the sensitivity of the data processed by their systems during the design phase and ensure that telemetry necessary for forensics and security compliance is retained post-runtime.
2. Persistent Storage for Logs: Logs must be forwarded to persistent storage, where appropriate security and retention policies are applied. This ensures that crucial telemetry is available for investigations and compliance audits.
3. Use of Compliance Standards: The Payment Card Industry Data Security Standard (PCI DSS) offers a robust baseline for log retention and can be adapted to fit the specific data and security needs of an organisation.
4. Log Volume Creation: Both system and application logs should be preserved by mapping logging directories to a persistent volume within the host operating system, ensuring their survival beyond the container lifecycle.
5. Deploy SIEM Solutions: Implement a Security Information and Event Management (SIEM) solution that captures logs from various sources, such as Windows event logs, antivirus detections, proxy logs, and firewall logs. The logs from containerised environments and associated applications should be aggregated in the SIEM for real-time monitoring and post-incident investigations. A SIEM solution also provides extended log retention and protection from log tampering by threat actors.
6. Evaluate Cloud Provider Tools: Organisations should assess the telemetry and log retention tools offered by their cloud providers to ensure they meet investigative requirements. Examples include Amazon CloudWatch, Microsoft Azure Monitor, and Google Cloud Operations Suite.
7. Endpoint Detection and Response (EDR): Deploy EDR solutions to hosts, including containers, to enhance visibility and monitor processes, network connections, and other host activities. EDR tools designed for container environments, such as those offered by Sysdig, Microsoft, CrowdStrike, and VMware, should be considered.
8. Install Sysmon for Enhanced Logging: Sysmon, available for both Windows and Linux, provides comprehensive logging of system events. For Windows systems, Sysmon logs command-line execution, driver/DLL loading, network connections, and file creation time modifications. A baseline Sysmon configuration template is available for use. On Linux, Sysmon monitors process lifetimes, network connections, and file system modifications, making it particularly useful for detecting malicious activity.
By following these recommendations, organisations can significantly improve their forensic readiness, particularly within cloud and containerised environments, ensuring that critical forensic data is available when needed for security incident investigations.