TL;DR;
Ransomware has grown into a significant industry for criminal enterprises due to its relatively low sophistication and the ability for it to be performed remotely, and the fact that it is supported by the existence of crypto currencies which facilitate remuneration. As a result, the likelihood of the perpetrators getting caught is currently extremely low for well executed campaigns.
The malicious code which powers ransomware campaigns denies a user, or enterprise, access to their data with the hope that backups don’t exist, presenting the target with the dilemma of ‘pay and support criminal enterprise while getting the data back’ or ‘writing off the data’.
In this blog post we will introduce two tools that we have developed, the first is a Ransomware Simulator and the second is a Ransomware Emulator. We also shed some light on how this class of malicious code achieves its goals on a victim’s system.
As an added bonus we have decided to release the Simulator as open source.
Introduction background
Over the past few years there have been several examples of ransomware, the most interesting ones include:
- CryptoLocker
- CryptoWall
- Yonathan Klijnsma from our Fox-IT division maintains a tracker
https://cryptowalltracker.org
- Yonathan Klijnsma from our Fox-IT division maintains a tracker
- Radaman
- Rokku
- TeslaCrypt (4.x)
- Its master key was recently released by the developers
https://en.wikipedia.org/wiki/TeslaCrypt
- Its master key was recently released by the developers
Due to the ever growing problem of ransomware NCC Group had a number of clients interested in understanding the potential impact. In response to this interest we created a simulator and emulator which our consultants use to help support client understanding in their scenario-based assessments.
The purpose of the simulator is to allow clients to understand the impact of ransomware on a given system in simulation mode i.e. no data loss. In the closed-source emulation mode it can be used by NCC Group within its laboratories or in controlled client environments to assess defensive anti-ransomware solutions by proof-testing their effectiveness. By virtue of this we developed two versions, simulator – which we have open sourced and emulator – which we have kept closed source to minimise harm from reuse by malicious threat actors.
NCC Group Ransomware Simulator
The simulator can be used to assess the status of the current system by enumerating the files that could be potential victims of a ransomware attack:
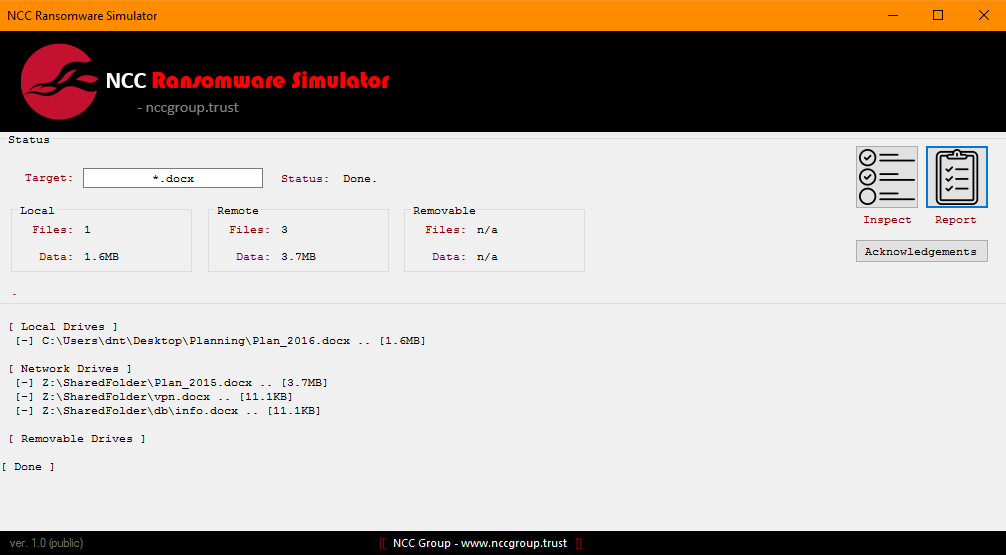
The simulator uses approaches used by an actual case of ransomware by scanning the following storage for files:
- Local
- Removable
- Network
For each of these locations, the simulator will look for content accessible to the current user i.e. the ability to read plus delete and/or overwrite. After scanning, the simulator will produce a detailed Microsoft Word-based report showing detailed information about the data that could be stolen from the current system:
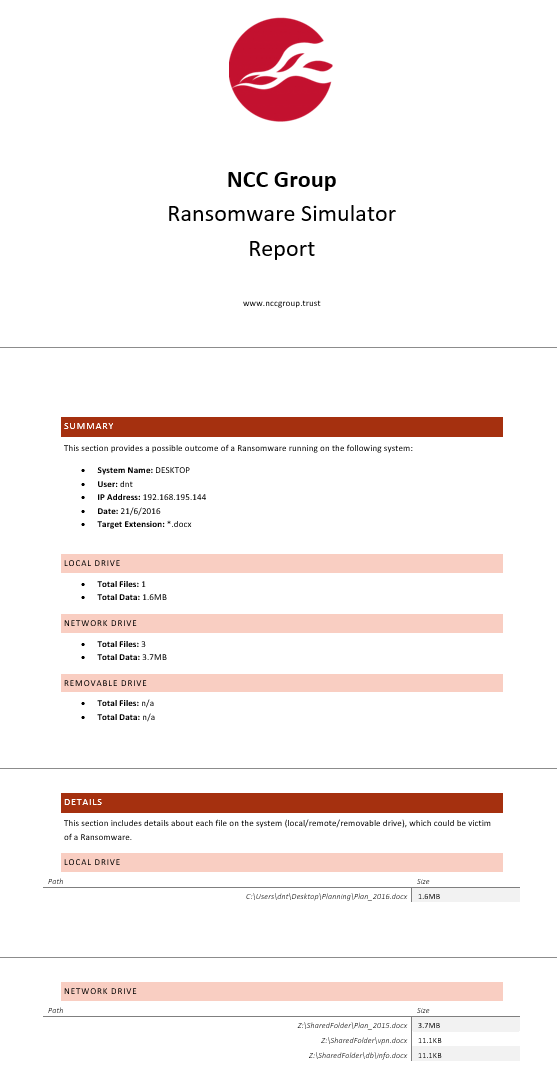
This report can be used to understand the impact that ransomware would have in a given environment when run by a given user. This can be extremely useful for organisations wishing to understand the scale of a ransomware attack running on their systems.
Note: in cases where Microsoft Word (used for the template generation) is not installed, the tool will produce a text-based report.
NCC Group Ransomware Emulator
WARNING: This mode may result in data loss and should only be used by experienced professionals thus why it is being kept as a closed-source tool by NCC Group.
This second mode can be used to test anti-ransomware solutions, which could be deployed on a system by emulating behavior seen by ransomware.
To perform such an assessment the user needs to manually enable the “Ransomware mode” in the emulator. Please note that this has been done on purpose to prevent people from running this mode by mistake.
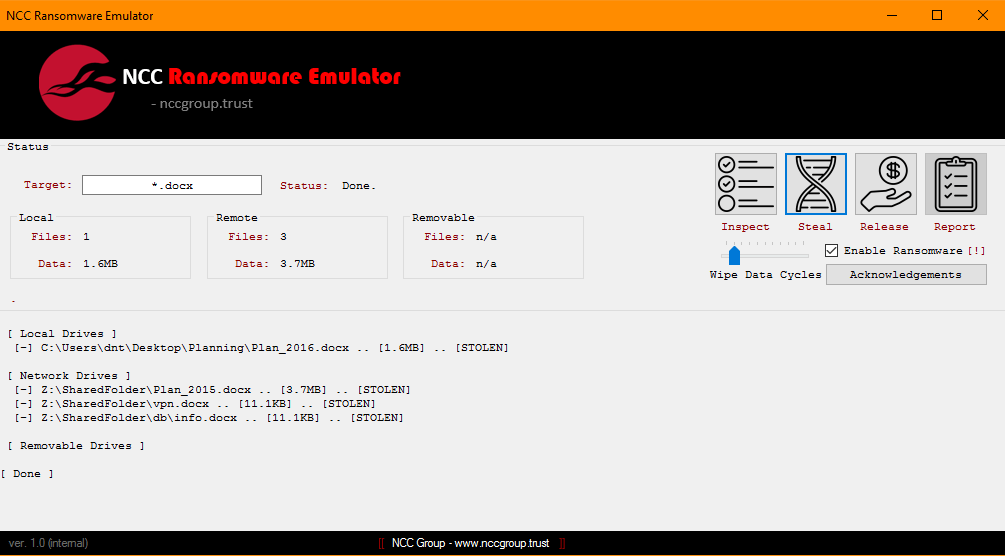
Once this flag is enabled, the tool will imitate a real ransomware attack by actually stealing targeted files from the system and replacing them with a “locked” version.
To mimic a real ransomware, the software will also use its own file extension:
The ransomware will install a custom extension handler via the Windows Registry to control file open events on locked files. This handler allows the tool to be instantiated when requests to access locked files are made and will prompt the user for a key to unlock the requested file:
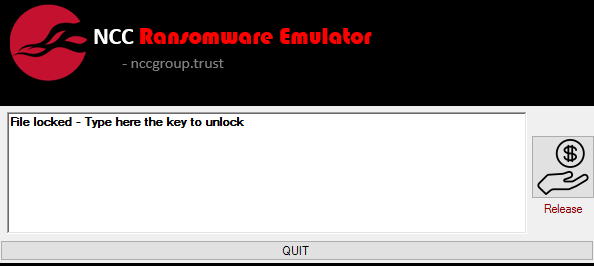
The purpose of the emulator is threefold:
- Assess protective monitoring capabilities of the organisation
- Assess the effectiveness of ransomware blocking solutions
- Assess data recovery solutions post-ransomware attack
Technical Bits on the Ransomware Emulator
This section describes the internals of the Ransomware Emulator. The emulator uses the .NET runtime and has been written in C#.
Building Blocks
A ransomware attack is usually composed of the following pieces:
- A way to find files on the victim’s system or to which they have access
- Usually obtained by performing a file scan
- A way to cryptographically lock these files denying user access
- Usually based on encrypting file contents
- A way to securely remove the original data from the system
- Usually performed by wiping the original data before removing it from the system
In the following sections we are going to discuss each of the above points in additional detail.
Scanning: locating target data
This is the basic step for most ransomware. Some ransomware in order to be even stealthier, may avoid scanning and opt instead to just await in the background for file open events to trace interesting files to steal.
For our purposes we used the scanning-based approach, which for each accessible drive (local/removable / network) on the system will locate all the files having the targeted extension and it will flag all the ones R+W (readable and writable) to the current user.
Stealing: the purpose of a Ransomware
This phase is probably the most interesting one, in which the emulator needs to actually steal the data from the system. To do so the following steps are performed:
- Create a new file container
- Read the target file data:
a. Content
b. Timestamps
c. Size
d. Path - Produce a new encrypted container (described in the next section)
- Remove the target file:
a. Wipe its content
b. Reset timestamps
c. Delete the target file
Encrypted File Container: securing the stolen data
The encrypted file container is at the core of every ransomware attack, and it is the most crucial point while dealing with this kind of malware, as usually most of the defensive efforts focus on breaking the container to get back the original data.
In our case, we use serialisation to produce a sequence of bytes representing our custom file container object instantiated on the target file data.
Serialisation is a powerful process that allows us to freeze the status (/context) of a given object in order to reuse it later on during the same, or even a completely different, programme execution.
Once the data has been serialised an encryption method will take care of producing an encrypted stream ready to be saved on the disk. This encrypted stream will replace the original file after its original data has been securely removed.
Removing Files: confusing recovery tools
There are several approaches to perform the file removal step. One of the most effective approaches consists of overriding the target data with zero multiple times before actually deleting the target file. Additionally, in order to confuse recovery tools the timestamps of the original files are scrambled.
Encryption: symmetric or asymmetric?
This is probably the rule of thumb to understand how good a ransomware is, and for how long it will survive (refer to the next session for additional info). In general the better the encryption, the better the ransomware. For our emulator we did not use anything special, we simply used a symmetric encryption algorithm using a hardcoded password, which would be a big no-no for a real counterpart.
In general, ransomware based on asymmetric algorithms tend to be usually much harder to defeat than their counterpart based on symmetric algorithms.
Survival: catching the Ransomware won’t give you back the data
If you’re interested in what you can do to survive ransomware attacks NCC Group published a guide earlier this year which can be found here – https://www.nccgroup.trust/uk/our-research/ransomware-what-organisations-can-do-to-survive/
Conclusions
Hope you have enjoyed this journey in the ransomware world. If you are curious to know what kind of information a ransomware could get out of your system, please take a look at our Ransomware Simulator which can be obtained from our Github repository here – https://github.com/nccgroup/ransomware-simulator.
Related articles
Ransomware: what organisations can do to survivehttps://www.nccgroup.trust/uk/our-research/ransomware-what-organisations-can-do-to-survive/
Written by Donato Ferrante
First published on 05/07/16
