Vendor: SonicWall
Vendor URL: https://www.sonicwall.com/
Versions affected: 10.2.0.8-37sv, 10.2.1.1-19sv
Systems Affected: SMA 100 Series (SMA 200, 210, 400, 410, 500v)
Author: Richard Warren
Risk: CVSS 8.2 (High) Summary
SonicWall SMA 100 Series appliances running firmware versions 10.2.0.8-37sv, 10.2.1.1-19sv and below suffer from a Stored Cross-Site Scripting (XSS) vulnerability within the management interface. This vulnerability arises due to lack of sufficient output encoding when displaying postscript file names within the management interface.
Due to CVE-2021-20040, this issue can be exploited by a remote, unauthenticated attacker.
Impact
When combined with CVE-2021-20040, this vulnerability may allow a remote unauthenticated attacker to inject arbitrary JavaScript into a page within the management interface. When an authenticated administrator visits this page within the management interface, arbitrary JavaScript could be executed within the administrators authenticated session.
An attacker with access to an administrative session could later exploit CVE-2021-20044 to achieve Remote Code Execution.
Details
SonicWall SMA SSL VPN suffers from stored XSS vulnerability within the admin panel. Normally this would result in a not very exploitable self-XSS, however due to CVE-2021-20040 and CVE-2021- 20044 this could be chained to achieve RCE from an unauthenticated perspective.
The admin application displays a list of “postscripts” which can be configured to execute on a user’s endpoint whenever they connect to the VPN. These are displayed on the /cgi- bin/extensionsetting page:
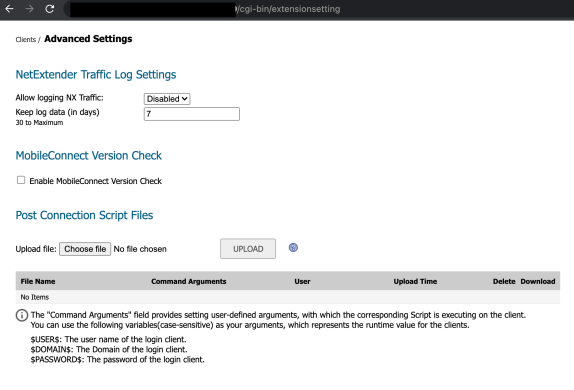
Any files contained within the /etc/EasyAccess/var/conf/postscripts/directory will be listed here.
The usual process to configure a postscript is to upload it via the admin application, at which point it will be available in the list of postscript files and displayed on this page.
When displaying file names on the extensionsetting page, no output filtering is carried out. This means that if a file containing an XSS string is written to the postscripts folder, it will result in Stored-XSS being triggered whenever a logged-in admin user visits the page.
In addition, CVE-2021-20040 allows an unauthenticated attacker to write files with semi-controlled file names to arbitrary locations on disk. By using a directory traversal attack to write a file containing an XSS string to the /etc/EasyAccess/var/conf/postscripts/ directory, an unauthenticated attacker can store an XSS payload in the admin interface. This payload will be triggered whenever a logged-in admin visits the extensionsetting page.
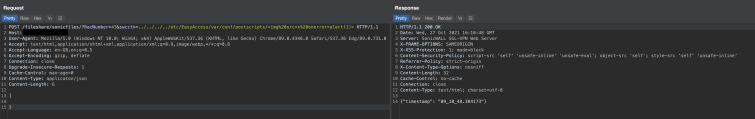
Unauthenticated request sample (exploiting CVE-2021-20040) to store the XSS payload:
Example XSS payload triggered when visiting the extensionsetting page:
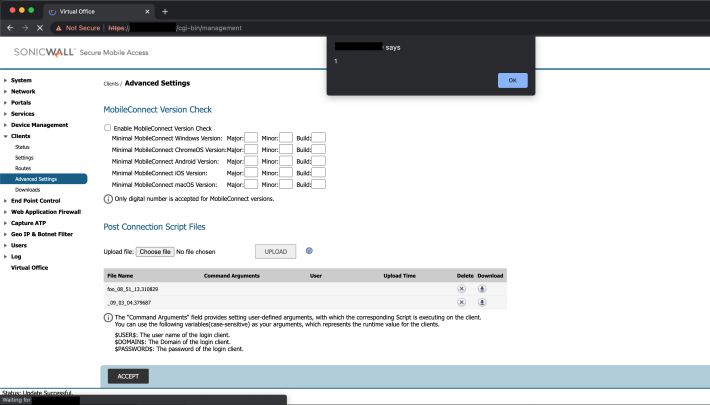
Any JavaScript executed as part of an XSS payload would run under the context of the admin’s logged-in session. Therefore, the attacker could leverage this to exploit post-authenticated command-injection, such as that described in CVE-2021-20044.
Note that CVE-2021-20040 can also be used to bypass CSP by hosting the JavaScript payload on the device.
The following video shows how these vulnerabilities can be chained to reset the administrator password and execute arbitrary commands as root:
Recommendation
Upgrade to SMA version 10.2.0.9-41sv, 10.2.1.3-27sv or above.
Vendor Communication
2021-10-29 - Vulnerability reported to SonicWall PSIRT.
2021-11-02 - Reply from SonicWall PSIRT stating that the vulnerability has been "rejected" as a duplicate/known issue.
2021-11-06 - SonicWall confirm they have addressed the other reported issues and shared a draft KB article, which omits details of arbitrary file-deletion and XSS issues. NCC Group requests clarification around this - providing evidence of successful exploitation on latest firmware versions (10.2.0.8-37v and 10.2.1.2-24sv).
2021-11-06 - SonicWall PSIRT respond stating that these issues were rejected, referencing the original triage response.
2021-12-07 - Patch released and SonicWall publish KB article.
2021-12-07 - NCC Group request further clarification on missing vulnerabilities.
2021-12-08 - NCC Group confirms that the arbitrary file-deletion vulnerability was fixed on firmware versions 10.2.0.9-41sv and 10.2.1.3-27sv.
2021-12-08 - SonicWall PSIRT responds stating that the issue was found by internal review prior to NCC Group's report, and for this reason was omitted from the advisory notes.
2021-12-09 - NCC Group advisory released.Thanks to
Jennifer Fernick and Aaron Haymore from NCC Group for their assistance with disclosure.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 2021-12-09
Written By: Richard Warren
