The healthcare sector and ransomware attacks appear together frequently in the media. Since before the start of the pandemic rarely a week goes by without at least one story about a healthcare organisation falling victim to a ransomware attack. We often hear about the financial impact these attacks have or how they can affect patient safety, but there is little to state what the actual impact on patient outcomes are.
Articles about a ransomware attack that could be found to be the cause of a death, or vulnerabilities in a specific medical device are very important in bringing these issues into the public eye. However, they do not explain or even truly allude to where clinical risk is negatively impacted the most and that is what should ultimately be the priority when discussing cyberattacks in healthcare.
According to statistics obtained from publications produced by the European Union Agency for Cybersecurity (ENISA) and the FBI’s Internet Crime Complaint Center (IC3), ransomware attacks since 2017 have increased in general year on year (apart from 2018, where attacks decreased compared to the previous year). This could be attributed to several reasons such as the growth of ransomware, widespread vulnerabilities affecting a multitude of organisations, and of course the pandemic contributing to a decrease in user vigilance and expanding the security boundaries of organisations. [1] [2] [3] [4] [5] [6] [7] [8] [9]
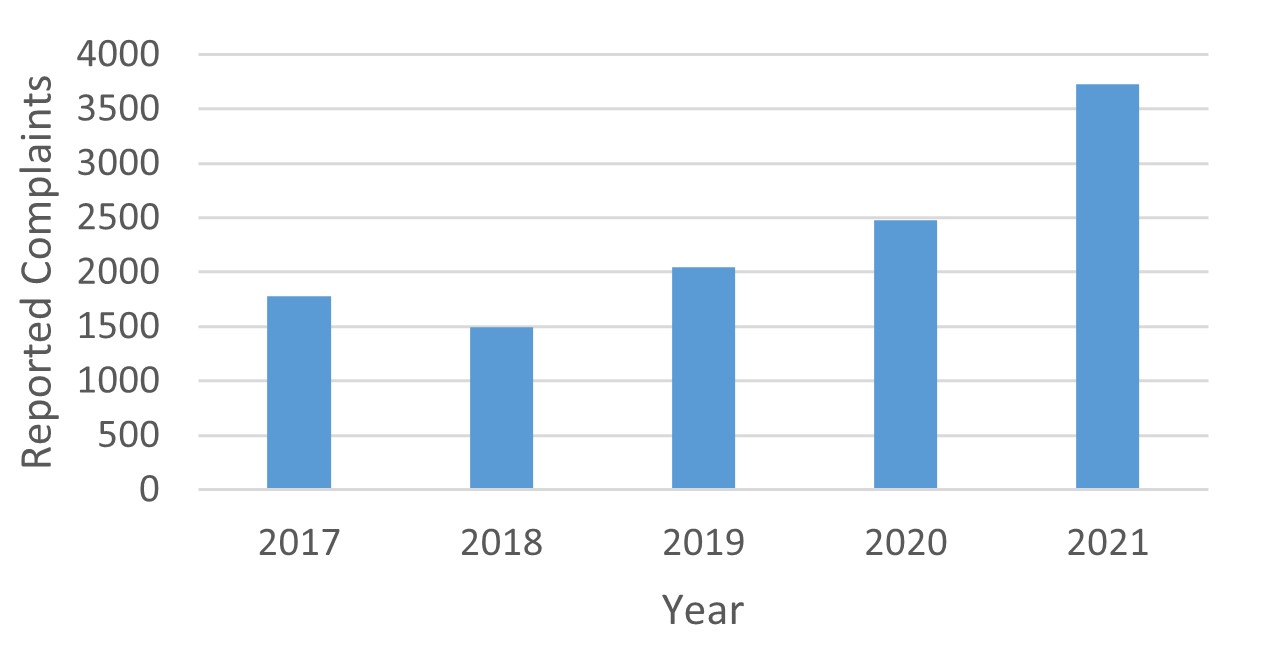
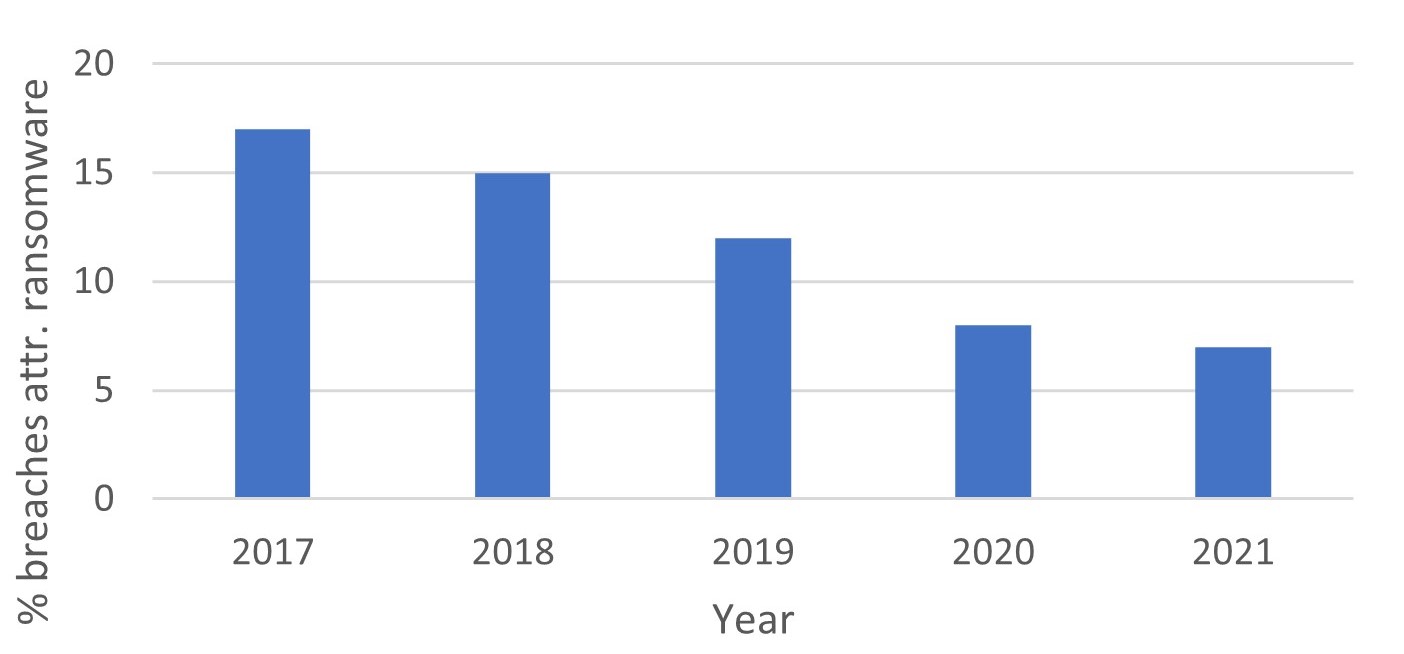
Contradicting the trend is the UK, according to the annual Cyber Security Breaches Surveys the percentage of breaches caused by ransomware attacks across all sectors have been steadily decreasing. However, ransomware remains one of the top three threats to UK businesses and charities. [10] [11] [12] [13] [14]
Although these statistics are not just about ransomware in the healthcare sector, the IC3 report from 2021 [11] shows that the healthcare and public health sector reported the most ransomware attacks. The number of healthcare organisations that reported being a victim of a ransomware attack was 148, this was significantly more than the next sector on the list, financial services, this being 89 organisations. A survey conducted by Sophos [15] stated that from 328 respondents 34% of organisations were hit by ransomware in the previous year (2020).
Similarly, the ENISA Threat Landscape 2020 [3] states “Healthcare organisations were the favourite target of ransomware attackers during all of the previous years, and this trend also continued in 2019.”
This would indicate that the healthcare sector remains a viable target as many organisations in this sector are considered soft targets. Furthermore, healthcare organisations are more likely to pay the ransom. [16]
Regardless of the fall or rise in the number of victims of ransomware, the continued attacks on the healthcare sector demonstrate callous behaviour towards patients’ wellbeing, the medical professionals and support staff of the healthcare organisations caring for those patients.
Current research on the impact of ransomware attacks on patient health
Ransomware attacks in healthcare environments can lock medical professionals out of workstations, disrupt access to services, prevent access to patient records, disable medical devices and prevent delivery of urgent care. With so many attacks occurring in the healthcare sector, the impact this has on patient outcomes could be disastrous, and even lead to death in extreme cases.
When discussing the impact that ransomware has on patient outcomes it is important to consider all circumstances and not just the most critical cases, although these should clearly be prioritised. A search using phrases such as “ransomware impact patient” and “ransomware impact health” was used on Google scholar, PubMed, ProQuest, and general searches using Google and Bing to try and find any related research that had already been conducted and could shed some light on how ransomware impacts patient outcomes.
Although the literary search was not exhaustive it appears this topic has not been thoroughly researched. Only a few contained conclusions as to whether a ransomware attack did in fact have a negative effect on patient outcomes. Furthermore, the results were inconsistent which in likelihood reflects the complex nature of healthcare environments but could also indicate more detailed research and analysis is required.
Direct impact
One of the most notorious incidents in recent years is that of the ransomware attack on a university hospital in Düsseldorf, Germany. Whilst enroute with a 78-year-old woman in a deteriorating state, paramedics were redirected to an alternative hospital 32 kilometres away due to systems being unavailable from the attack. The delay in treatment caused by the additional transfer time was initially suspected to have contributed to the patient’s death. However, the investigation later found that the patient’s condition was so severe at the time she was picked up that “The delay was of no relevance to the final outcome,” as reported by Wired [17].
Another incident occurred in 2019, in which an infant died at a hospital that was in the midst of a ransomware attack. The lawsuit states “Because numerous electronic systems were compromised by the cyberattack, fetal tracing information was not accessible at the nurses’ station or by any physician or other healthcare provider who was not physically present in Teiranni’s labor and delivery room. As a result, the number of healthcare providers who would normally monitor her labor and delivery was substantially reduced and important safety-critical layers of redundancy were eliminated.” [18].
Whilst the tragedy of these cases should not be understated, they only account for a small part of the overall effect that ransomware or any IT/OT outage could have in a healthcare environment.
Rerouting
A retrospective analysis was conducted after a successful ransomware attack on a health system in Southern California sent a large influx of patients to two emergency departments at the University of California San Diego. The increase in demand for care was above any expected increase from other situations such as flu season however, the analysis did not involve determining the impact on patient outcomes. [19] [20]
Whilst this is not linked to ransomware it highlights that delay in care can have a negative impact on patient outcomes. Analysis of Medicare data [21] relating to patients suffering from a heart attack concluded that delays in ambulance journeys due to road closures (in this instance because of a marathon taking place) increased the 30-day mortality rate (a death occurring within 30 days of a defined event).
Remediation effects
A research paper on the effect a data breach has on patient outcomes determined that “Hospital data breaches significantly increased the 30-day mortality rate for AMI” (AMI – Acute Myocardial Infarction, also known as a heart attack). The researchers also stated that “Ransomware attacks are considered to be more disruptive to hospital operations than the breaches considered in this study… If disruption to information technology used by providers is driving the breach effect, the findings from our study suggest that ransomware attacks may have an even stronger negative impact on patients than the breaches studied in this paper.” [22]. The researchers suggest that the changes to health information technology (HIT) as well as new policies and procedures following a data breach contribute to the increase in 30-day mortality and the longevity of the impact.
The CyberPeace Institute released a report [23] in March 2021 that references research conducted at Vanderbilt University. Similar to the previous paper, this research discovered that remediation efforts following a data breach caused an increase in the 30-day mortality rate of patients suffering from a heart attack up to 3 years after the initial breach.
Large scale attacks
An article published in Nature.com [24] analysed data from the WannaCry attack on the NHS. Interestingly, the research found “no significant effect demonstrated on mortality across all hospitals.”. However, the article also details “The NAO stated that there were no reports of patient harm from NHS organisations.1 This is difficult to quantify, and as discussed, mortality is a crude measure of patient harm. While the attack may not have led to a direct impact on mortality, we are unable to ascertain the true impact on complications, patient morbidity, or changes in care processes that resulted from the attack.”
This is a key point as a negative outcome that does not lead to death can still have a significant impact on a patient’s life. For example, a delay in care that leads to paralysis, or organ failure that then requires the patient to have a transplant. Situations like this affect the patients’ quality of life as well as medical staff time and resources.
Many respondents from a recent survey conducted by the Ponemon Institute [25] reported that a ransomware attack caused longer stays in hospital and delays that resulted in poor outcomes.
The most convincing study [26] to date is one conducted by the Cybersecurity and Infrastructure Security Agency (CISA). This study was primarily concerned with the impact of COVID-19 on the Provide Medical Care National Critical Function in the US. The study was also able to gain insights into the impact that ransomware has on hospitals which found that “Although there are no deaths directly attributed to hospital cyberattacks, statistical analysis of an affected hospital’s relative performance indicates reduced capacity and worsened health outcomes”.
What data is missing about the impact of ransomware attacks on patient health?
What does all this mean? Currently we do not know enough about the effects that ransomware has on patient outcomes. Delays in care can cause negative outcomes, the average amount of downtime caused by ransomware reached 26 days according to Coveware [27]. It stands to reason then that a ransomware attack would incur negative outcomes as well.
Furthermore, this is only considering the immediate downtime caused by the event. What about continued delays due to any backlogs that have occurred? Ransomware attacks, or any prolonged cyberattack or IT/OT outage, could result in long-term effects of a wide variety of medical conditions as well as the psychological effect on patients including a lack of trust whereby patients do not disclose information that might be key to diagnosis. Not to mention the effect that the resultant fatigue can have on medical staff [28].
The Department of Health and Social Care (DHSC) in the UK recently outlined the new cyber security strategy for health and social care, this included “calling for input from around the sector to improve the understanding of how cyber relates to patient outcomes and identify the important elements.” [29].
Attack vectors and targeted systems
Few details exist on root cause of successful attacks and depending on what resource you find the order of common attack vectors differ. A quarterly report from Coveware [27] lists the top 3 ransomware attack vectors across all industries over the past 3 years as RDP, email phishing, software vulnerability. Whilst the most common attack vendor according to respondents from the Ponemon study [25] was through cloud applications. Analysis in 2020 conducted by researchers at Tenable found a key method for gaining access to hospital networks was through a pair of Citrix vulnerabilities [30].
Electronic Patient/Health/Medical Records (EPR, EHR, EMR) are also prime targets for attackers. Medical records contain a lot of valuable data so this can be used for several fraudulent reasons, especially in countries where healthcare is not paid for by the state. Preventing access to these systems will disrupt the delivery of care. Vital information becomes unavailable to help treat patients and therefore exerts overwhelming pressure on healthcare organisations to pay the ransom.
The attack on the Health Service Executive (HSE), Ireland’s public health service, prevented access to all the IT systems and took four months to decrypt all the servers [31]. This meant access to patient records and scans were not available for extended periods of time.
Downtime in laboratory’s also cause significant issues as Laboratory Information Systems (LIS) and clinical labs are very reliant on interconnectivity between systems [32]. Delays in ordering tests and receiving results can have an impact on clinical decision making.
How to better understand the impact of ransomware events?
Given the complexity of the healthcare industry it would be beneficial to understand not just the immediate impact of ransomware attacks but also the medium and long-term effects as well. Knowing what could happen in the first few hours, 5 years, and key points in between would help develop preventative actions. It would also help prepare for potential consequences and care requirements in the event of a successful attack.
Metrics could include:
- The effects on individual and/or groups of illnesses
- The short/medium/long-term resources required to facilitate the effects on patients
- A breakdown of what systems and departments are affected
- The percentage of movement in clinical risk – for example, how many low-risk cases escalate to medium-risk due to a delay in care
- Number of cases referred to neighbouring facilities
A more in-depth retrospective analysis of the WannaCry attack on the NHS as well as ongoing analysis of the HSE attack would be extremely useful in shaping how healthcare organisations prepare for, respond to, and recover from ransomware attacks.
What do we need to know to be able to address this problem?
Being able to analyse current or previous events more thoroughly is one way to understand the true impact that ransomware attacks have on healthcare organisations. However, data gathered from a previous or current attack may not be accurate or complete as a result of the incresae in stress and load on staff and resources.
Another option could be to use simulations and AI/ML to predict how ransomware attacks affect patient outcomes. A recent paper [33] detailing the results from adapting an established simulation model, used for evaluating operational strategies [34], to assess the resilience of hospitals to cyberattacks. In conjunction with a simulation of this type it might be possible to apply AI/ML to predict specific medical issues [35] [36] [37] [38] or patient outcomes in general [39].
Imagine a healthcare organisation being able to understand with some confidence what the impact would be on any or all their patients, based on what systems were down, for how long those systems were down and if services were available at a neighbouring facility.
It is important to understand what the real impact is, prolonged cyberattacks have the potential to have a significant effect but are unlike other disaster situations. Power outages can be protected against by using backup generators that will kick in quickly, weather patterns can, to a certain extent, be predicted and planned for. Ransomware can strike at any moment, take out an unpredictable number of systems, affect multiple organisations simultaneously over large geographic distances, and recur at the whim of attackers if remediation efforts are insufficient or non-existent. More importantly, ransomware can be, to an extent, prevented by following security best practices such as hardening systems and devices, properly segregating networks, installing security patches and updates.
From a financial perspective the ability for a healthcare organisation to get back to a functioning state and implement remediation objectives could be hampered by additional strain from lawsuits. A worrying statistic, reported by Healthcare Finance News [40], shows an increase in lawsuits filed against healthcare organisations over data breaches.
As such disaster recovery plans should include recovery from ransomware attacks as part of the strategy, arguably as a priority. The HSE report [31] and simulation research [33] note, respectively, the absence of preparation for relevant scenarios, “In addition, as is the case with many other organisations, the scenario of sustained loss of IT across the entire health service has not been planned for, with specific considerations and playbooks,” and no consideration for a cyberattack as a hazardous event, “while the impact of a wide variety of hazard event types on hospital capability and capacity were studied, cyberattack was not previously considered in these models.”
Cyberattacks targeting the healthcare sector, as with any other industry, do not have borders so international collaboration around research information-sharing is important. If we have more diverse input about impact on different communities, populations, economies, and geographic areas we can build better solutions to the problem. Therefore helping to ease the burden on healthcare professionals, resources and contribute to preventing poor patient outcomes.
Next steps
It would be beneficial to expand on previous research and take a deep dive into hospital data from just prior and up to today from the WannaCry attack. Concentrating on a small but varied number of health issues that have the potential to demonstrate if and how delays in care caused by ransomware affect patient morbidity. Using examples of hospitals that were able to transfer patients to neighbouring facilities as well as hospitals that were not able to is important to understand the immediate and the cascading effects.
This would hopefully lay the foundations for creating configurable ransomware simulations for a more proactive approach to help prevent attacks but also to better understand where clinical resources should be prioritised.
References
[1] https://www.enisa.europa.eu/publications/enisa-threat-landscape-report-2017
[2] https://www.enisa.europa.eu/publications/enisa-threat-landscape-report-2018
[3] https://www.enisa.europa.eu/publications/ransomware
[4] https://www.enisa.europa.eu/publications/enisa-threat-landscape-2021
[5] https://www.ic3.gov/Media/PDF/AnnualReport/2017_IC3Report.pdf
[6] https://www.ic3.gov/Media/PDF/AnnualReport/2018_IC3Report.pdf
[7] https://www.ic3.gov/Media/PDF/AnnualReport/2019_IC3Report.pdf
[8] https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf
[9] https://www.ic3.gov/Media/PDF/AnnualReport/2021_IC3Report.pdf
[16] https://news.sophos.com/en-us/2022/06/01/the-state-of-ransomware-in-healthcare-2022/
[17] https://www.wired.co.uk/article/ransomware-hospital-death-germany
[18] https://www.documentcloud.org/documents/21072978-kidd-amended-complaint
[19] https://www.medpagetoday.com/meetingcoverage/acep/95357
[21] https://www.nejm.org/doi/full/10.1056/NEJMsa1614073
[22] https://arxiv.org/pdf/1904.02058.pdf
[23] https://cyberpeaceinstitute.org/report/2021-03-CyberPeaceInstitute-SAR001-Healthcare.pdf
[24] https://www.nature.com/articles/s41746-019-0161-6
[25] https://www.censinet.com/ponemon-report-covid-impact-ransomware
[26] https://www.cisa.gov/sites/default/files/publications/CISA_Insight_Provide_Medical_Care_Sep2021.pdf
[29] https://www.ukauthority.com/articles/five-pillars-in-cyber-strategy-for-health-and-social-care/
[30] https://www.zdnet.com/article/ransomware-attacks-now-to-blame-for-half-of-healthcare-data-breaches/
[31] https://www.hse.ie/eng/services/publications/conti-cyber-attack-on-the-hse-full-report.pdf
[32] https://academic.oup.com/ajcp/article/157/4/482/6533636
[33] https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8638073/
[34] https://www.tandfonline.com/doi/abs/10.1080/24725579.2019.1584132
[36] https://www.scientificamerican.com/article/ai-can-predict-kidney-failure-days-in-advance/
[37] https://www.nbcnews.com/mach/science/ai-predicts-heart-attacks-better-doctors-n752011
[38] https://www.futuremedicine.com/doi/full/10.2217/fon-2021-0302
[39] https://www.nature.com/articles/s41746-018-0029-1
[40] https://www.healthcarefinancenews.com/news/patients-increasingly-suing-hospitals-over-data-breaches
