Phishing the simple and effective blended attack
Phishing is a common and yet highly successful technique used by adversaries and red teams alike to breach organisations. Phishing is successful as it is a blended attack relying on end-users to be convinced, tricked or otherwise persuaded into performing an action which benefits the attacker.
The actions the end-user might be encouraged to perform include:
- Reading the email.
- Opening attachments.
- Replying with requested information.
- Clinking on web links.
All of which are designed to further the threat actors goal… but how? A common technique is to appear to be an internal, and thus trusted, source of the original email. Be it an internal function/department or a specific employee. This masquerade is often performed by either spoofing the source of the email or registering a legitimate clone of the original looking Internet domain.
Combating phishing through technology and training
To combat the threat of phishing we have seen a range of approaches and technologies developed and employed with variety degrees of success. These countermeasures are today broadly broken down into:
- Education and assessment via services such as NCC Group’s Piranha:
- User awareness training and sensitising.
- Phishing simulation.
- Pro-active countermeasures:
- Re-active response
- Suspect phishing reporting email client plug-ins.
However, even with all of these countermeasures no organisation is impervious… buy why?
The way we are reading is changing
Well one reason is we face not only technical and user awareness challenges but also changes in how we are reading. The fact we stare at screens all day, consume ever increasing amount of information while invariably multitasking appears to be having an impact. In the book Words Onscreen: The Fate of Reading in a Digital World, the American linguist Naomi Baron surveyed the change in reading patterns which The Guardian summarised the impact as:
“Where the impact can be measured, it consists primarily of a propensity to summarise. We read webpages in an “F” pattern: the top line, scroll down a bit, have another read, scroll down. Academics have reacted to the increased volume of digitally published papers by skim-reading them. As for books, both anecdotal and survey evidence suggests that English literature students are skim-reading set works by default.
The attention span has shortened not just because ebooks consist of a continuous, searchable digital text, but because they are being read on devices we use for other things. Baron reports that a large percentage of young people read ebooks on their cellphones – dipping into them in the coffee queue or on public transport, but then checking their work email or their online love life, a thumbswipe away.”
While these changes relate to reading more broadly we have to accept these new habits will have an impact on how carefully people will study emails or other forms of communication before acting upon in one way or other. This change in behaviour is without considering other external stressors, volume challenges and cultural norms.
Raising the bar through clear identification
So we know that people have a key role in reducing the likelihood of successful phishing attacks but we all need help in this task due to various factors. With so many new global top level domains coming onto the market, coupled with typo or similar domain names, the ability for someone to register a domain which appears legitimate to all but the eagle eyed is increasingly challenging. Indeed we’ve documented a recent case where someone registered nccgrouptrust.com (nccgroup.trust being our legitimate domain) and attempting to phish our finance department.
One very simple aid is to clearly identify to people/end-users emails which originate outside of the organisation. This aid can be as a simple nudge to say ‘be aware’ and encourage the individual to be a little more cautious when dealing with it than they might otherwise be. It also has the benefit of not being a usability blocker encouraging workarounds while being ever present.
In order derive the most value from implementing such a countermeasure it needs to be combined with a user awareness program that outlines:
- What EXTERNAL: prefixed to a subject means to them.
- Why it’s important to consider it when dealing with emails and attachments.
- What the individual’s responsibility is in helping ensure the cyber resilience.
- What the individual should do if they suspect something with such emails.
… as we said simple… yet effective!
Implementing external email identification in Microsoft Exchange
To implement the identification of external emails in Microsoft Exchange is actually really simple. But first you have some choices on how this will be done:
- Adjust the title of email to pre-fix with EXTERNAL: or similar identifier.
- Adjust the content of the email to start with a warning or similar identifier.
Microsoft Exchange provides the ability to do either or both of these through transport rules and transport rule actions.
Note: When we implemented this functionality we decided only to modify the subject so as not to break digital signatures on signed email bodies.
The rule we implemented is similar to the below and done so using EAC or EMC depending on your Exchange version (see Microsoft Exchange documentation for Transport rule procedure examples – includes Exchange Online) and the rules conditions:
- Transport Name: External email prepend EXTERNAL:
- Apply this rule if: The sender is located ‘Outside the Organisation’
- Do the following: Prepend the subject of the message with ‘EXTERNAL:’
- Except if: The subject matches ‘^EXTERNAL:.*’
- Mode: Enforce
- Match sender in: Header
You can test the rule before going live and once live the users inbox looks something like this:
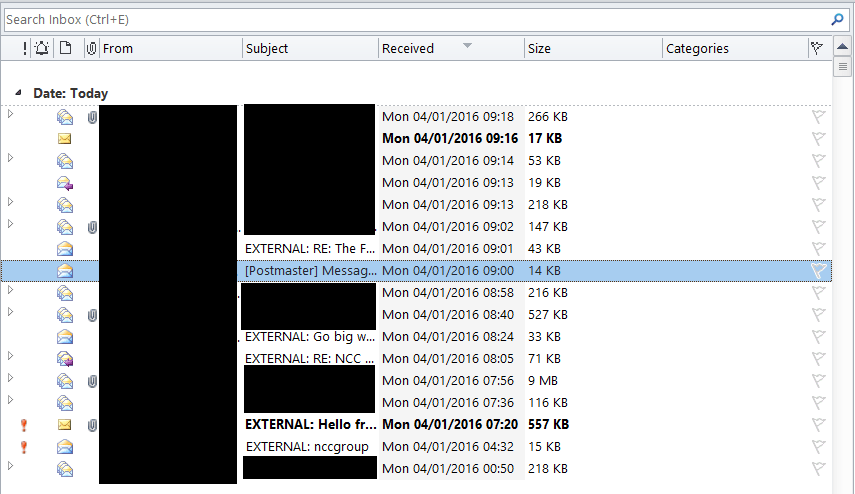
Now if someone registers nccgrouptrust.ninja or similar and emails internally claiming to be an employee it will flagged as EXTERNAL:.
Sometimes simplicity and usability are key to a good nudge
Judging the effectiveness of countermeasures such as this one can be challenging and in this instance we have relied on user feedback. From a small survey we have seen positive with comments along the lines of it isn’t invasive but does cause extra consideration when dealing emails… so we consider a successful nudge!
Published date: 04 January 2016
Written by: Ollie Whitehouse
