[Editor’s note: This post is a part of our blog series from our NCC Group summer interns! You can see more posts from consultants in our internship program here.]
When testing APIs with short-lived authentication tokens, it can be frustrating to login every few minutes, taking up a consultant’s time with an unnecessary cut+paste task — As well as introducing the possibility for human error in copying across the token, which can further hinder testing.
Today we are releasing JWT-Reauth, a plugin aims to provide a painless solution to this issue. JWT-Reauth provides Burp with a way to authenticate with a given endpoint, parse out the provided token and then attach it as a header on requests going to a given scope.
The latest version of the plugin can be downloaded as a JAR file from the releases page on GitHub: https://github.com/nccgroup/jwt-reauth/releases/
Feature List:
- Caches authentication tokens
- Regex parsing for the token format
- Custom authentication header via the UI
- Functionality accessible via the send-to-extension context menu:
- Setting the authentication request
- Parsing a token from a specific request
- Adding a URL to the scope
- Adjustable token refresh time
- Entire plugin can be configured then enabled to start attaching the header
Example Usage:
This example will cover creating an authentication request in Postman, proxying it through Burp and adding that request to the plugin to be handled automatically.
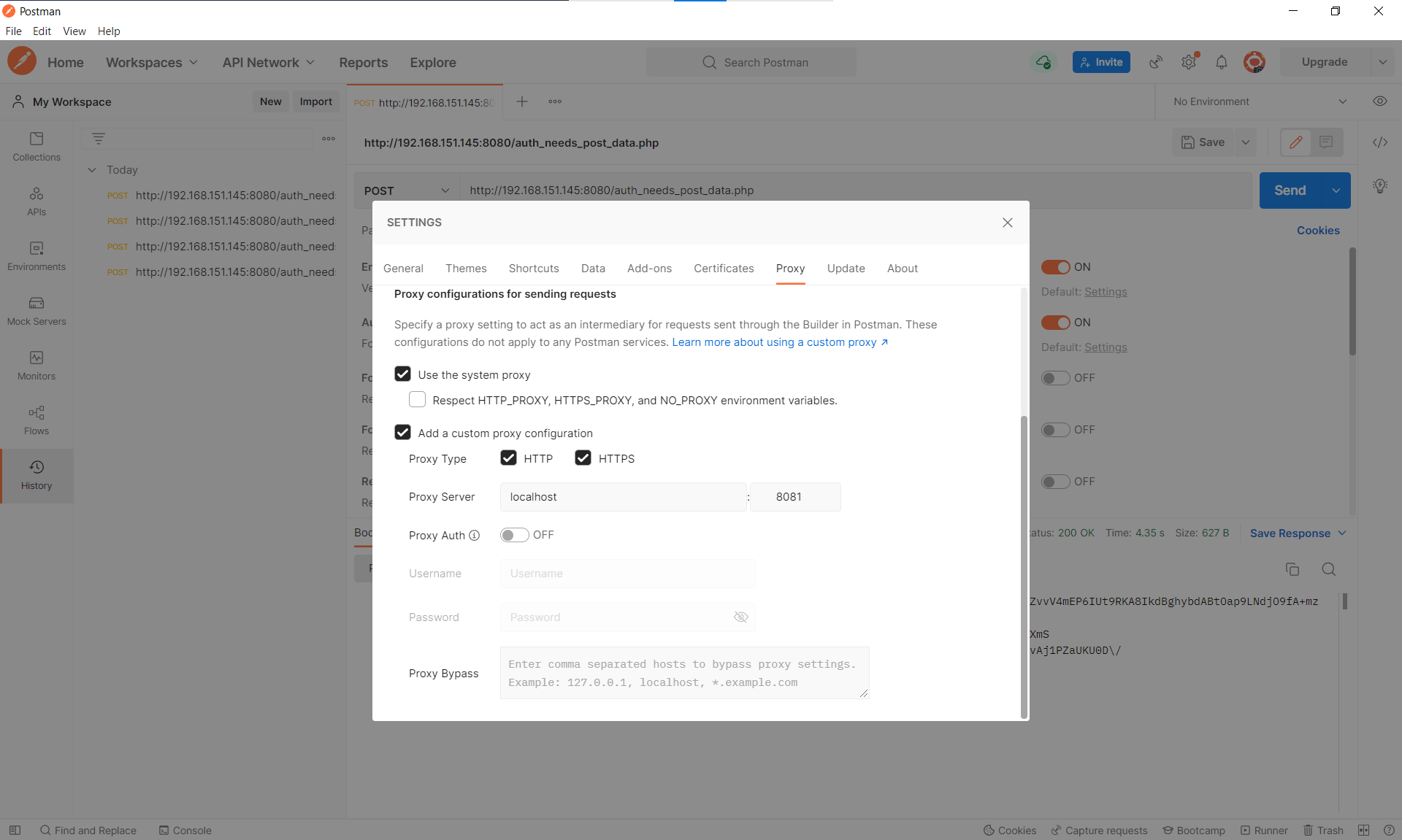
Initially I like to setup my Burp proxy listening on 8081 as personal preference. I can then set Postman to proxy through Burp from the settings tab:
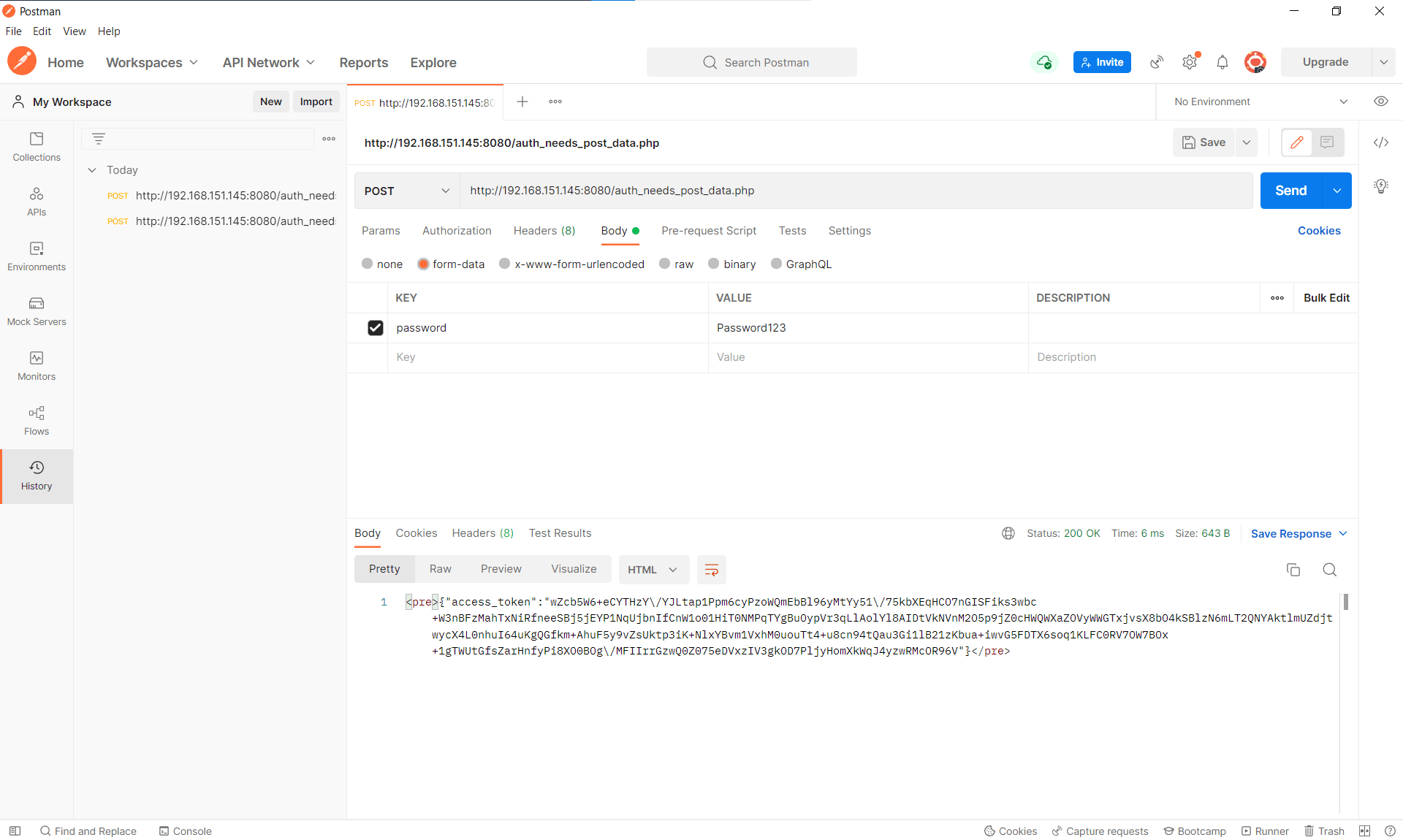
Once everything is going through Burp, we create an authentication request in Postman:
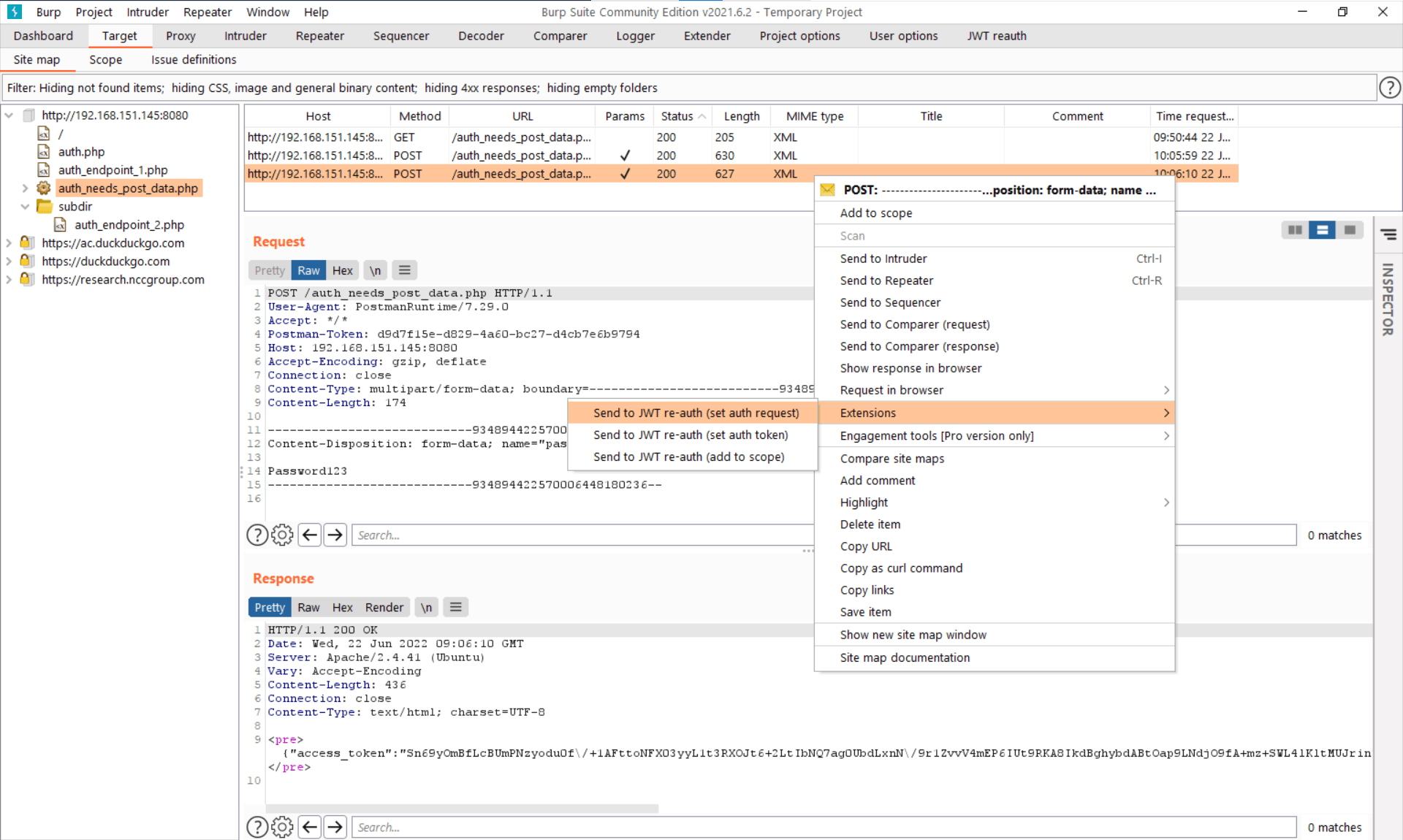
Once you have a working request for getting an access token, you can go to Burp’s target tab, find the site and use the context menu to send it to the plugin as an auth request. Note: requests from the proxy history also have this context menu.
While we’re in the target tab, it would be nice to add the request to JWT-Reauth’s own scope, so we do that using the “Send to JWT-Reauth (add to scope)” option in the context menu:
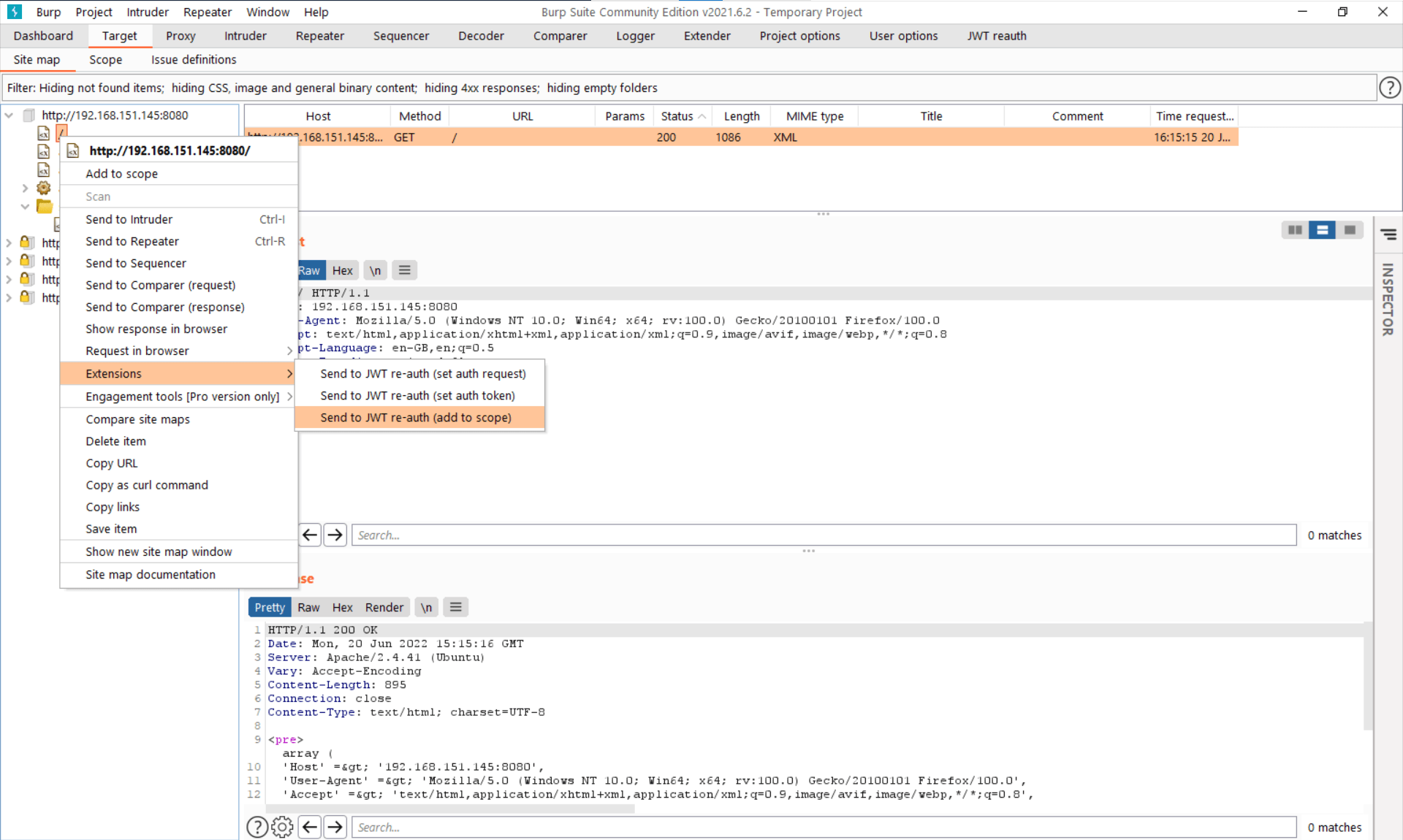
This will then appear in the JWT-Reauth’s own scope tab. I have also enabled the “Prefix” mode, meaning it will match any request whose URL has this as a prefix. This is useful for just including an entire site / subdirectory in the scope.
If we now navigate to the main plugin tab we will see the following:
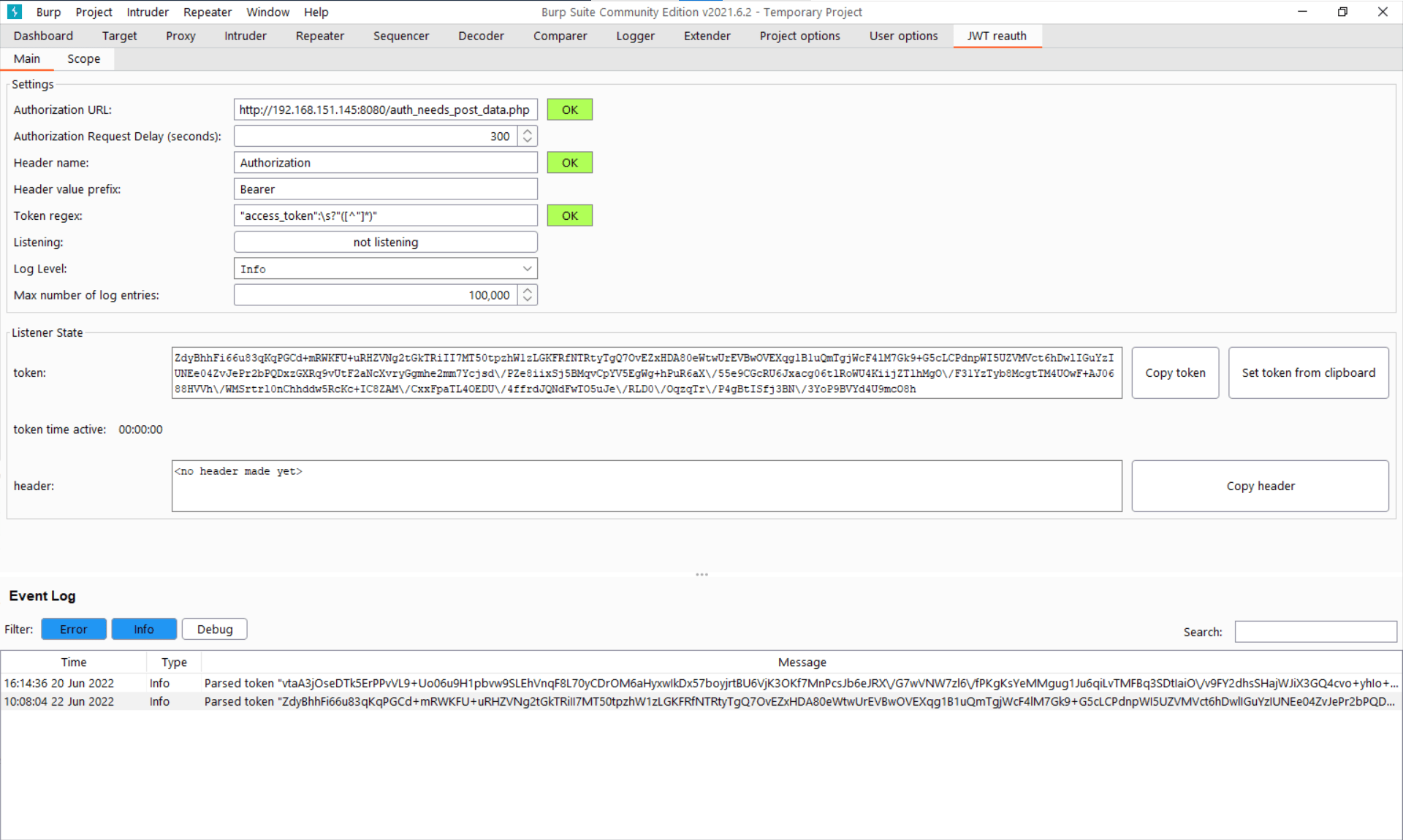
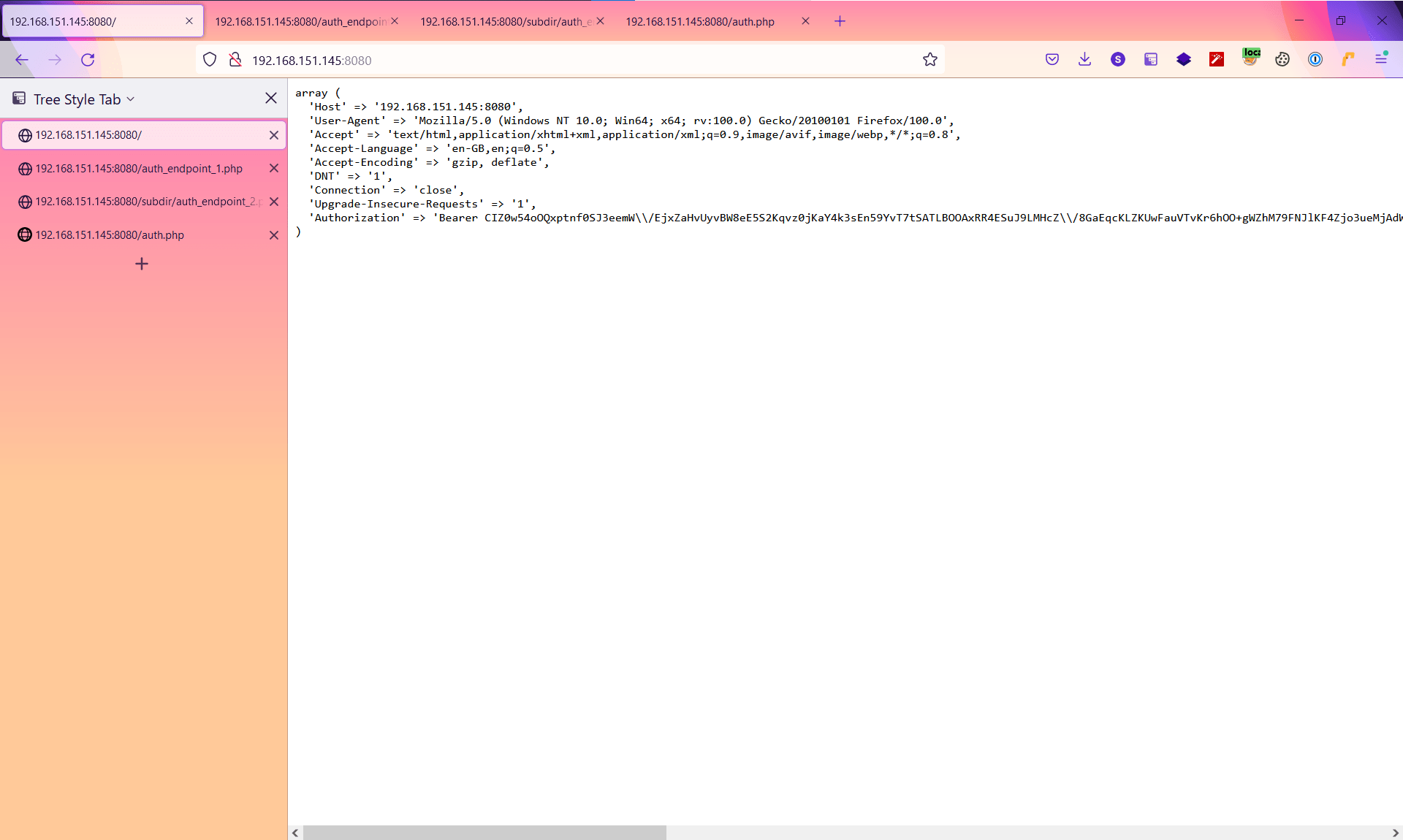
JWT-Reauth has successfully used the authentication request to send a request of its own and parse the token out. To enable the substitution for proxied requests, we toggle the ‘not listening’ button to ‘listening’. If we now navigate to an in-scope URL we can see that the Authorization header is added:
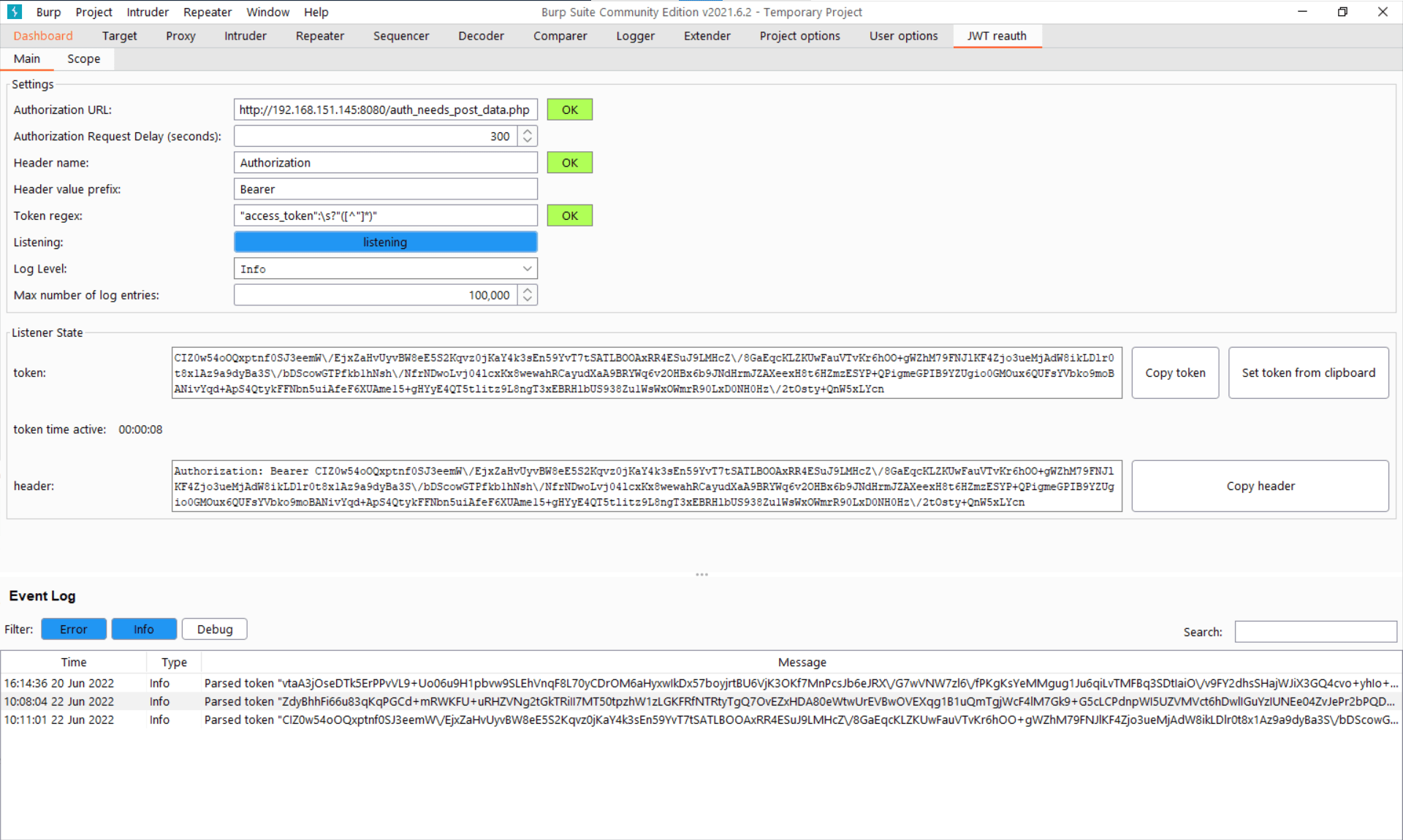
Finally navigating back to the plugin we can see that it has cached the Authorization header for later use:
Alternative Uses
JWT-Reauth is also useful when using cURL, as it helps to avoid having to embed and update long token credentials in the commands.
The example cURL command below sends an authentication request through Burp using the –proxy option, enabling JWT-Reauth to reuse the request.
curl --request POST
--proxy 127.0.0.1:8081
192.168.151.145:8080/auth_needs_post_data.php
--data "password=Password123"{"access_token":"rVgzEQ9pAMU2vaDe5JBJtF3EhX9cVlhc0XGtUeElkGqSjsy7fC2XnHrS23vdULA41XlSY8McclN5dDXyO8Qh5yQv40RS3+2QDHrHVqqtT5mj4h261i/WJQ89hn87V1im3AiubBsc4n8jTVa5qZq5tmXw9GXqaCx8jqkq21+UvqaGYInFrQA3sc8GLRfTVAHa+benVnZOGfqp/ur6hOb79S4wTfoL8VoDT5OL+mkkIVxRebgEk6Cv+HkI5Uix7KgMA+MEH1IMfbdTPtVlHG1BOwuxrXmi1X00NRXXwwGfR6YCfwS9pXCLeegBj9M3dd+tEFyU4IROtk31Z48r4TfTpc3N70hcUKWvuzciNToIaTtN8qx78KSP9gGxgkzLHqlIjlHMSa6XZPrYkwN9"}After JWT-Reauth has been configured, we can keep using cURL’s –proxy option instead of having to pass in the entire authentication header, and JWT-Reauth will handle the rest.
curl --request GET
--proxy 127.0.0.1:8081
192.168.151.145:8080/array (
'Host' =>; '192.168.151.145:8080',
'User-Agent' => 'curl/7.79.1',
'Accept' => '*/*',
'Connection' => 'close',
'Authorization' => 'Bearer +7mXfg4WkDyu8ajEyZQCOPgDaH4N4UQgNF0puZzmEnwJI8pPKuJlL/AtWrUQqyPYXDKme4iFrFAq0woonGHrhcXh/cdeLK5G3GCmj6mj7pSn7dPJ+JqGugLouCgYAeLsN+E/88zPnPaIIls38tgUQ9sQxbFjb/nYcvRqFkJigQqwpXRcriGv1VKDT/fU8iCeoGbrlpJSl2hy7C+ReeZYQi1WMrBulCCzxyhGq0rVwQ1Ix1zxwt/wgN3DuXT7N6USiuZFMHWfzBvOj/Eo095zQ7sU4byMJB/YLFfxjzMOfaHmhHFWH4hoI9hOOEkJdXT/IUtRatWomya2F3ydWRd0vnNgrw1ZKh64ebWKxz+I2mUctXxmgQIE+gUqOnn5Y40azYt2V9P7g9rPeW89',
)Summary
Overall I hope this plugin can be useful and save people some hassle. If you have any ideas for how to improve the plugin / features you would like to see, Issues and Pull Requests over on GitHub are very much appreciated!
https://github.com/nccgroup/jwt-reauth/issues
