Conducting a thorough Azure security build review or Azure security assessment can be difficult. Clicking through the Azure Ibiza [1] portal to review the details on many of its services, including, but not limited to, Azure Active Directory (Azure AD), resource groups, virtual machines, storage accounts, databases, database servers and other services isn’t always feasible. Despite Microsoft Azure having a well-designed dashboard panel, some important information isn’t visible.
There are several amazing tools for extracting information from Azure subscriptions but they have some limitations, including:
- Most of the tools have strong prerequisites to work successfully, such as installing the Azure PowerShell Cmdlets.
- The majority of tools do not support threading, so requesting data is slow when dealing with large Azure deployments.
- The vast majority of these tools cannot export to multiple formats, and if they do they tend to only support JavaScript Object Notation (JSON) formats or plain-text report-based files.
Beyond the Microsoft Azure portal, Microsoft also provides information and full access to some well-designed tenant-scoped Application Programming Interface (API) endpoints to manage Azure subscriptions. With that in mind, I have decided to create my own PowerShell tool that wouldn’t have these limitations.
Currently, Azucar supports resources deployed with both the Azure Resource Manager and the Azure Service Manager. Therefore, security researchers only have to use Azucar to obtain all data, and they will also be able to export the data to several formats.
Azucar is a multi-threaded plugin-based tool to help assess the security of Azure Cloud environment subscriptions. By leveraging the Azure API [2], Azucar automatically gathers a variety of configuration data and analyses all data relating to a particular subscription in order to determine security risks.
Features
Azucar offers a large number of features that will allow further security build reviews or security assessments. The following features are supported by the tool:
- Extracting information about Azure AD, including a number of attributes on computers, groups, users, contacts, etc.
- Searching for high-level accounts in Azure subscription, including Azure AD, Classic Administrators, Directory Roles and Role-Based Access Control (RBAC) roles.
The following assets are also supported by Azucar:
- Azure SQL Databases
- Azure AD
- Storage accounts
- Classic virtual machines
- Virtual machines v2
- Security status
- Security policies
- Role Assignments (Including RBAC)
- Missing security patches
- Missing security baseline
- Web application firewall
- Network security groups
- Classic endpoints
- Azure security alerts
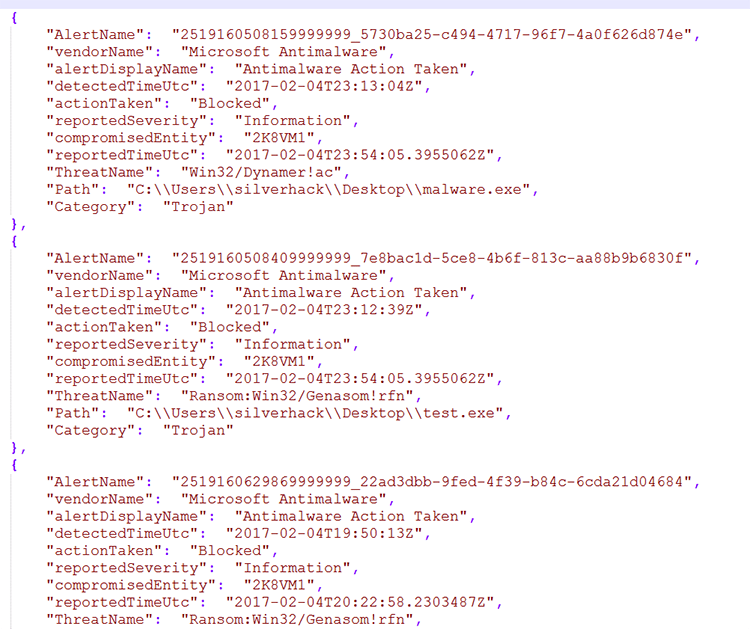
I have also created several internal functions that generate output to multiple formats such as Comma Separated Values (CSV), Extensible Markup Language (XML), Excel or JSON.
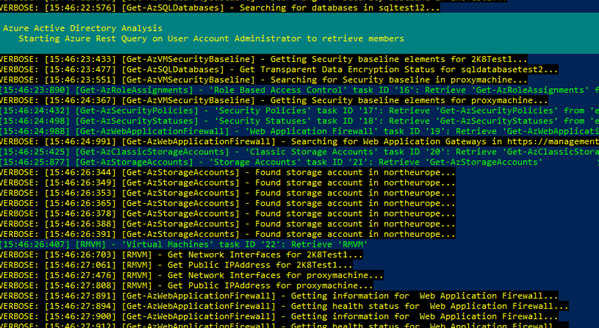
The following screenshot shows an example of a report in JSON format:
Getting started
Azucar works out of the box with PowerShell version 3.x and .NET 4.5. You can check your Windows PowerShell version by executing the command $PsVersionTable:
PS C:Userssilverhack> $PSVersionTable
Name Value
---- -----
PSVersion 5.1.16299.251
PSEdition Desktop
PSCompatibleVersions {1.0, 2.0, 3.0, 4.0...}
BuildVersion 10.0.16299.251
CLRVersion 4.0.30319.42000
WSManStackVersion 3.0
PSRemotingProtocolVersion 2.3
SerializationVersion 1.1.0.1
You can download Azucar by cloning the repository. You can achieve this by using the following git command:
git clone https://github.com/nccgroup/azucar.git
Before starting, you need to unblock all files. Once you have unzipped the zip file, you can use the fantastic PowerShell V3 Unblock-File cmdlet that will do this task for you:
Get-ChildItem -Recurse c:Azucar_V10 | Unblock-File
After unblocking all files, you can get a list of basic options and switches by using the following command:
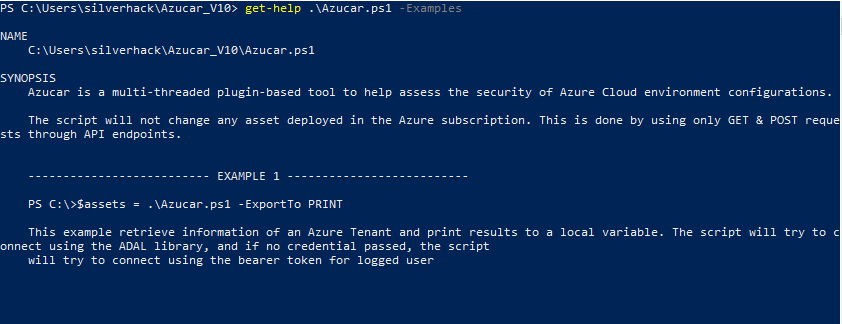
get-help .azucar.ps1
If you need key use-case examples or a list of all options and examples with some additional information, you can use the parameters -Examples and -Detailed, as shown below:
Now let’s look at some fancy real-life situations:
In the Active Directory world, the domain admins group is a very powerful group and is a great target for attackers. Attackers will most likely target users who are members of any of high privilege groups within Active Directory, because they possess the necessary privileges and permissions to perform administrative operations. Access to these accounts will provide an attacker with the flexibility and freedom to attack an entire organisation in many ways.
Azure AD is very similar, so it is best practice to limit admin rights to trusted individuals who are highly skilled. Azure offers pre-defined RBAC [3] roles, so a company administrator can define access for all users, groups and service principals by assigning roles to a particular scope.
Another useful (yet potentially dangerous) feature of Azure AD, which is present in Active Directory, is that Azure AD groups can be nested. If an Azure administrator does not take care to configure these properly and safely, members of groups within groups which are members of subgroups could potentially be automatically granted membership into another super-group.
Consider the following example:
- In the Stark Industries Azure tenant, there is a user called Bernard who has a “User role” and is a member of the group “Sales Users”. That means that Bernard can access assigned resources but cannot manage directory resources.
- The Sales Users group has five members and a group membership for that group called “Fake Group”.
- The Fake Group has zero members and a group membership for that group called “IT Administrators”.
- The IT Administrators group has the owner role, which has full access to all deployed resources.
- This means that Bernard is a super-hero-user within the subscription.
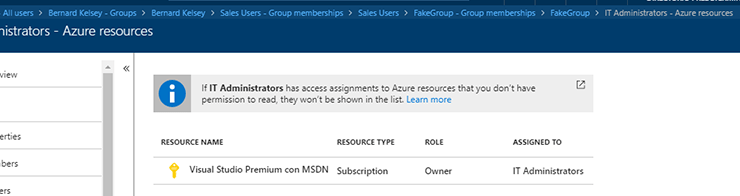
Azucar will recursively enumerate members of all groups along with nesting level and parent group information in order to get the effective permissions over the subscription in scope, as shown below:
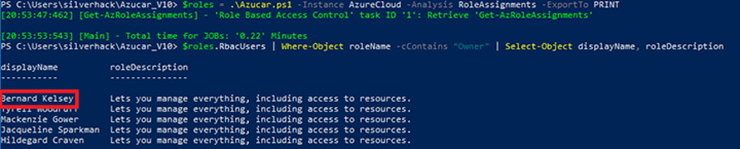
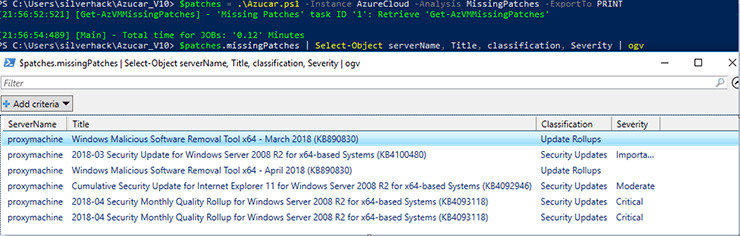
Another useful example that comes to mind is related to virtual machines and the patch status. With Azure Automation [4] an administrator can manage updates and patches for virtual machines deployed in Azure. The bad news is that you cannot directly get this information by using the Azure PowerShell Cmdlets.
With Azucar it’s very easy to get information about missing patches, by using the MissingPatches flag, as shown below:
Writing a plugin/parser
The plugin mechanism included in Azucar provides an easy method for PowerShell developers to dynamically add functionality, so if you want to extend the functionality of Azucar, you can do so by writing your own plugin in PowerShell.
To create a custom plugin, add it to the pluginscustom folder. The plugin code is simple; a script plugin is essentially any valid PowerShell script saved in a .ps1 extension, and each is a self-contained PowerShell that will be passed as a scriptblock class. The variable names and return values are the same throughout all plugins, so they can be generically loaded. The following sample shows a basic structure of an Azucar PowerShell plugin:
#Sample skeleton PowerShell plugin code
[cmdletbinding()]
Param (
[Parameter(HelpMessage="Background Runspace ID")]
[int]
$bgRunspaceID,
[Parameter(HelpMessage="Not used in this version")
[HashTable]
$SyncServer,
[Parameter(HelpMessage="Azure Object with valuable data")]
[Object]
$AzureObject,
[Parameter(HelpMessage="Object to return data")]
[Object]
$ReturnPluginObject,
[Parameter(HelpMessage="Verbosity Options")]
[System.Collections.Hashtable]
$Verbosity,
[Parameter(Mandatory=$false, HelpMessage="Save message in log file")]
[Bool] $WriteLog
)
Begin{
#Import Azure API
$LocalPath = $AzureObject.LocalPath
$API = $AzureObject.AzureAPI
$Utils = $AzureObject.Utils
. $API
. $Utils
#Import Localized data
$LocalizedDataParams = $AzureObject.LocalizedDataParams
Import-LocalizedData @LocalizedDataParams;
$Section = $AzureObject.AzureSection
}
Process{
#Do things here
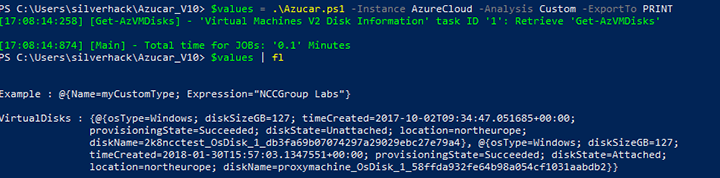
$ReturnValue =
[PSCustomObject]@{Name='myCustomType';Expression={"NCCGroup Labs"}}
}
End{
if($ReturnValue){
#Work with SyncHash
$SyncServer.$($PluginName)=$ReturnValue
$ReturnValue.PSObject.TypeNames.Insert(0,'AzureRM.NCCGroup.myDecoratedObject')
#Create custom object for store data
$MyVar = New-Object -TypeName PSCustomObject
$MyVar | Add-Member -type NoteProperty -name Section -value $Section
$MyVar | Add-Member -type NoteProperty -name Data -value $ReturnValue
#Add data to object
if($MyVar){
$ReturnPluginObject | Add-Member -type NoteProperty -name Example
-value $MyVar
}
}
else{
Write-AzucarMessage -WriteLog $WriteLog -Message
($message.AzureADGeneralQueryEmptyMessage -f "My Super Plugin",
$AzureObject.TenantID) `
-Plugin $PluginName -Verbosity $Verbosity -
IsWarning
}
}
Once you have your plugin prepared and located into the pluginscustom directory, your plugin should be ready to be loaded by using the -Custom flag, as shown below:
Fancy reports
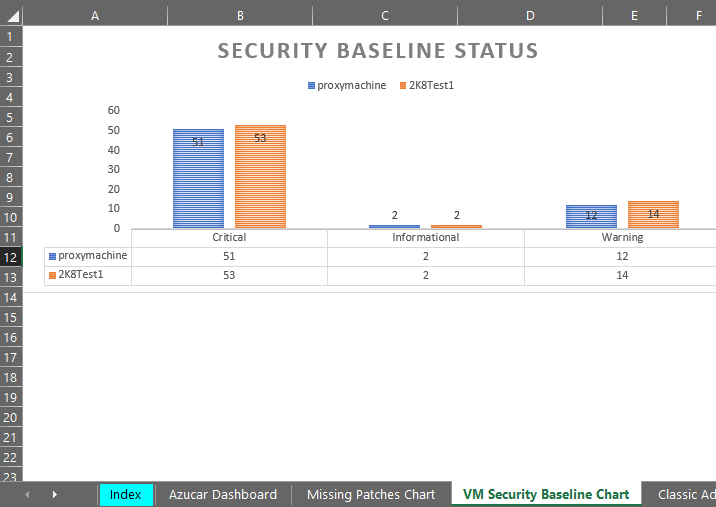
As discussed, there is support in Azucar for a variety of file formats (CSV, XML or JSON) and there is also support for exporting data driven to Excel format. Currently, Azucar supports style modification, chart creation, company logo or independent language support. At the moment, Office Excel 2010/2013/2016 are supported by the tool.
Therefore, if you need to export all data from your Azure subscription to a dedicated Excel spreadsheet…. You can do it with Azucar!
Azucar is open source
Azucar is free to use but please note that it still a work in progress, and potentially needs some heavy code refactoring. So, if you find a bug or want to request a new feature then please feel free to submit issues directly through Azucar GitHub site here: https://github.com/nccgroup/azucar/ or get in touch with me on Twitter – @tr1ana.
Final words
Because Azúcar is the Spanish word for sugar, I would like to quote from Mary Poppins and the great song Spoonful of Sugar, which says the following:
“In every job that must be done, there is an element of fun. You find the fun and snap! The job is a game”
I hope you enjoyed the post.
References
[1] https://azure.microsoft.com/es-es/blog/announcing-azure-portal-general-availability/
[2] https://docs.microsoft.com/en-us/rest/api/
[3] https://docs.microsoft.com/en-us/azure/role-based-access-control/overview
[4] https://docs.microsoft.com/en-us/azure/automation/automation-tutorial-update-management
Published date: 24 April 2018
Written by: Juan Garrido
