USB hosts are everywhere – laptops, TVs, tablets, car infotainment systems, even aeroplane seat-backs. All of these hosts need to understand the capabilities of devices that are connected to them – a process is known as enumeration. It is basically a conversation between the device and the host upon insertion to agree on what functionality within the device should be used, how much power is required by the device and how much can be provided by host etc. The information is provided by a USB device in data structures called “descriptors”, which contain a number of specific fields containing data; an example is shown below:
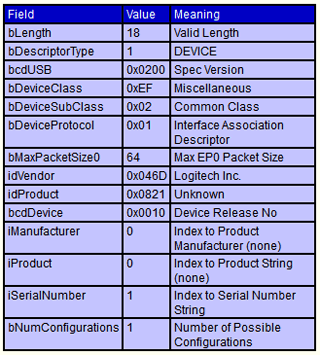
All of this data needs to be parsed and processed by the host and this is where problems can occur. As with any data interpretation incorrect assumptions, misunderstandings of the protocol standard or just plain insecure programming can result in security vulnerabilities that can be triggered by malicious entries within USB descriptors. At Black Hat 2011 I presented a cross-platform technique that enabled the identification of vulnerabilities within USB host driver software. More than a year later, using the technique at NCC Group we have identified over fifty USB driver bugs covering all of the major operating systems and as a result have learned a great deal about where the bugs are commonly found and which are most likely to be exploitable. You can find out more by reading the whitepaper Lesson learned from 50 bugs: Common USB driver vulnerabilities
Published date: 04 January 2013
Written by: Andy Davis
