Current Vendor: Belkin Vendor URL: https://www.linksys.com/sg/p/P-WRT160NL/ Versions affected: Latest FW version - 1.0.04 build 2 (FW_WRT160NL_1.0.04.002_US_20130619_code.bin) Systems Affected: Linksys WRT160NL (maybe others) Authors: Diego Gómez Marañón – Diego.GomezMaranon[at]nccgroup[dot]com CVE Identifier: CVE-2020-26561 Risk: 8.8 (High) – AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Summary
The Linksys WRT160NL is a switch device initially owned by Cisco and, after the sale of its respective technology branch, by Belkin. In the latest version of the official firmware, the web server binary contained a buffer overflow vulnerability that could be remotely triggered by requesting an authenticated endpoint.
Impact
Successful exploitation of this vulnerability can lead to remote code execution on the affected device.
Details
The mini_httpd binary in the firmware version 1.0.04 build 2 of the Linksys WRT160NL uses the insecure function sprintf when a specific and authenticated POST request is sent.
The vulnerable function is called create_dir and its decompiled code can be checked below.
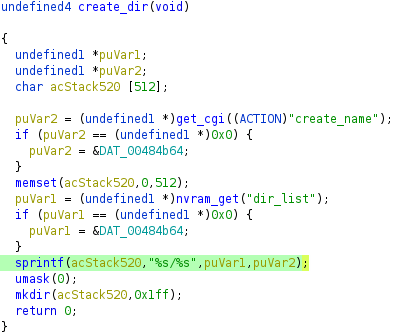
The following request was used to trigger this functionality:
POST /apply.cgi;session_id=42ef7c31a24121c858d670e84d0350d9 HTTP/1.1 Host: 192.168.1.1 User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:79.0) Gecko/20100101 Firefox/79.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,/;q=0.8 Accept-Language: en-GB,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 1197 Origin: http://192.168.1.1 Connection: close Referer: http://192.168.1.1/apply.cgi;session_id=d55bad29cf2ca864be41836aa71a3e46 Upgrade-Insecure-Requests: 1 submit_button=Disk_Properties change_action=gozila_cgi submit_type=create_dir next_page=Share_Properties.asp create_name=AAAA...AAAA share_name=
Recommendation
Due to the fact that the product is no longer supported, the best option is to update its firmware with an open-source alternative like OpenWRT.
Vendor Communication
- 23 Sep 2020 – NCC Group contacted Belkin to make them aware of the found vulnerability.
- 27 Sep 2020 – A new case is created to look into the issue.
- 05 Oct 2020 – Answer from Belkin explaining that the device is not actively supported.
- 20 Oct 2020 – Advisory published.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published date: 20/10/2020
Written by: Diego Gómez Marañón
