Vendor: Ivanti Pulse Secure
Vendor URL: https://www.pulsesecure.net/
Versions affected: Pulse Connect Secure (PCS) 9.11R11.5 or below
Systems Affected: Pulse Connect Secure (PCS) Appliances
Author: Richard Warren
Advisory URL: https://kb.pulsesecure.net/articles/Pulse_Security_Advisories/SA44858
CVE Identifier: CVE-2021-22937
Risk: 7.2 CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H Summary
The Pulse Connect Secure appliance suffers from an uncontrolled archive extraction vulnerability which allows an attacker to overwrite arbitrary files, resulting in Remote Code Execution as root.
This vulnerability is a bypass of the patch for CVE-2020-8260.
Impact
Successful exploitation of this issue results in Remote Code Execution on the underlying Operating System with root privileges. An attacker with such access will be able to circumvent any restrictions enforced via the web application, as well as remount the filesystem, allowing them to create a persistent backdoor, extract and decrypt credentials, compromise VPN clients, or pivot into the internal network.
Details
The Pulse Connect Secure appliance suffers from an uncontrolled archive extraction vulnerability which allows an attacker to write executable files within the /home/runtime/tmp/tt/ directory, resulting in Remote Code Execution. PCS allows administrative users to import archived configurations. These configurations are compressed using GZIP and encrypted using a hardcoded key, allowing the attacker to encrypt and decrypt their own crafted archive files. When these archives are imported via the administrative GUI, extraction takes place in an unsafe manner, leading to arbitrary file (over)write.
Whilst this issue was patched by adding validation to extracted files, this validation does not apply to archives with the “profiler” type. Therefore, by simply modifying the original CVE-2020-8260 exploit to change the archive type to “profiler”, the patch can be bypassed, and code execution achieved.
Root Cause Analysis
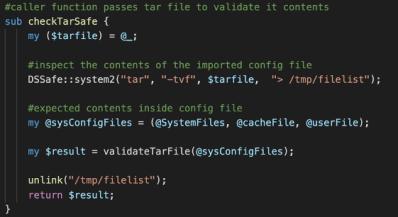
In October 2020, Pulse Secure released PCS version 9.1R9, which patched the CVE-2020-8260 vulnerability. The patch added a new function named DSConfig::validateTarFile. When archives are imported via the DSConfig::importConfigImpl, the contents of the uploaded config archive are listed using the tar -tvf command, and placed into a file named /tmp/filelist. The function validateTarFile is then called, providing a list of safe files, which should be expected inside an uploaded archive.
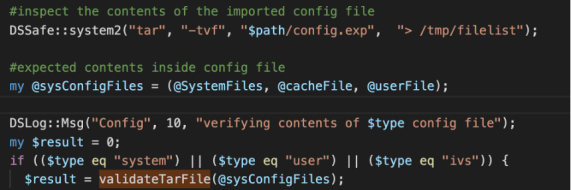
The validateTarFile function parses the output in /tmp/filelist, and ensures:
- The archive does not contain any symlinks or hardlinks.
- The archive contains only the expected files
- No files contain
../in their name.
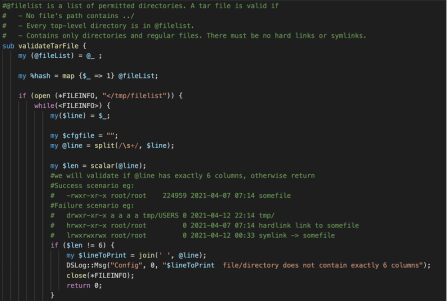
This added check prevented exploitation of CVE-2020-8260.
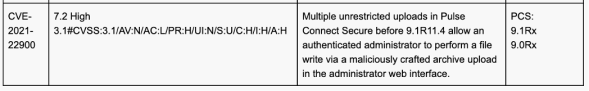
In May 2021, Ivanti released PCS version 9.1R11.4, which addressed a number of vulnerabilities which had been exploited in-the-wild. According to the release notes, a vulnerability which sounded very similar to CVE-2020-8260 was also addressed:
Diffing PCS versions 9.1R10 and 9.1R11.4 we could see that calls to DSConfig::checkTarSafe had been added to a number of CGI files:
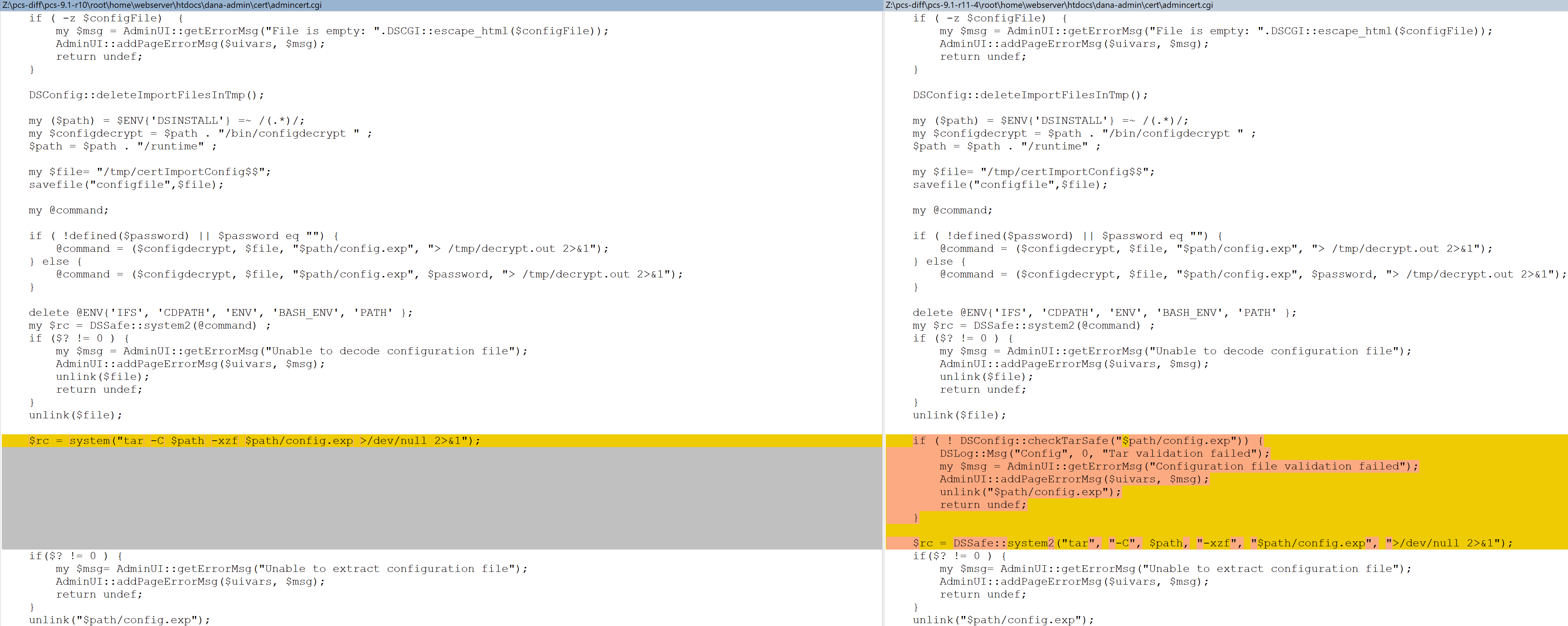
This additional validation was added to the following CGIs:
- /dana-admin/cert/clientauthcert.cgi
- /dana-admin/cert/admincert.cgi
- /dana-admin/mobile/smimeCert.cgi
Just like the check in DSConfig::importConfigImpl, the checkTarSafe function first lists the files within the uploaded archive, before calling validateTarFile
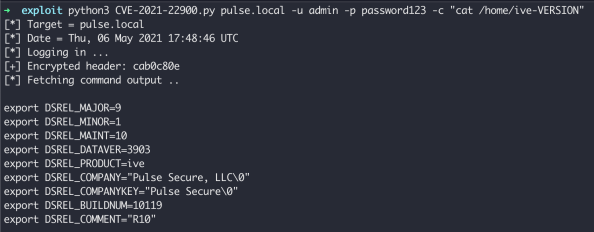
From this we could identify that CVE-2020-22900 was a variant of CVE-2020-8260. By changing the original exploit to POST to these CGI files instead, we could achieve code execution on PCS < 9.1R11.4.
Due to the existence of these variants within the import feature(s), we thought it would be a good idea to carry out further variant and patch analysis see if it was still possible to exploit the extraction vulnerability elsewhere.
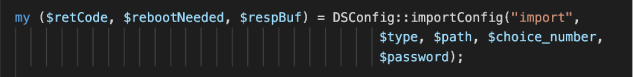
Reviewing the code within import.cgi, we could see that config imports are processed via DSConfig::importConfig, which is passed the uploaded file-path and some other options, including the archive type:
Within importConfig, we could see that it either calls importConfigImpl, or importProfilerDatabase, depending on the archive type supplied by the user:
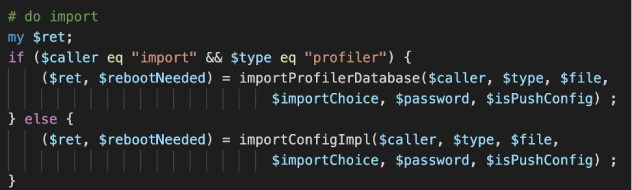
As demonstrated earlier, importConfigImpl contains a call to validateTarFile, however importProfilerDatabase did not contain this check before the tar -C command is executed:

Therefore, by changing the uploaded archive type to “profiler”, the patch for CVE-2020-8260 could be bypassed.
Proof of Concept
A Proof of Concept was developed to achieve Remote Code Execution as the root user, simply by changing a single POST parameter variable in the original CVE-2020-8260 exploit.
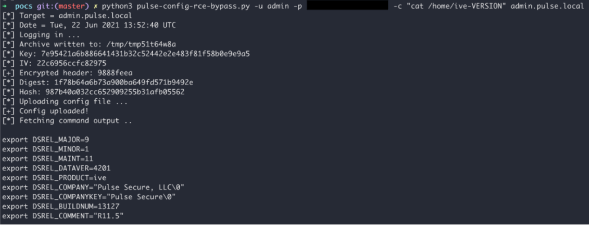
Recommendation
Upgrade to Pulse Connect Secure (PCS) 9.1R12, or later.
Vendor Communication
2021-05-12 – Reported to Pulse Secure via HackerOne.
2021-05-13 – Acknowledgement of submission from HackerOne received - awaiting triage.
2021-05-25 – Requested an update via HackerOne - no response.
2021-06-22 – Confirmed that the exploit still works on newly released PCS 9.1R11.5 version. Shared a screenshot via HackerOne ticket and requested a further update - no response.
2021-07-15 – Emailed Ivanti/Pulse Secure PSIRT updated HackerOne ticket informing them that the vulnerability will be publicly disclosed on 2021-07-23, as per our disclosure policy (if a vendor is unresponsive).
2021-07-15 – Reply received from Ivanti PSIRT via email. Requested that we hold off disclosure and requested further details of the vulnerability (due to lack of access to HackerOne).
2021-07-15 – Vulnerability details shared with Ivanti PSIRT via PGP email.
2021-07-20 – Ivanti PSIRT confirm they were able to verify the report and plan to release a fix by August 2nd.
2021-07-20 – We agree to hold off disclosure until after the updated version is released.
2021-07-31 – Ivanti confirm the fix will be released in PCS 9.1R12, which is scheduled for August 2nd, and request that we don’t publish the advisory until August 5th.
2021-08-02 – Pulse Connect Secure 9.1R12 released.
2021-08-05 – Advisory published.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published date: 2021-08-05
Written by: Richard Warren
