Vendor: SonicWall
Vendor URL: https://www.sonicwall.com/
Versions affected: 10.2.0.8-37sv, 10.2.1.1-19sv
Systems Affected: SMA 100 Series (SMA 200, 210, 400, 410, 500v)
Author: Richard Warren
Advisory URL: https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2021-0026
CVE Identifier: CVE-2021-20043
Risk: CVSS 8.8 (High) Summary
SonicWall SMA 100 Series appliances running firmware versions 10.2.0.8-37sv, 10.2.1.1-19sv and below suffer from a heap-based buffer overflow vulnerability in the sonicfiles RAC_GET_BOOKMARKS_HTML5 API. This vulnerability arises due to the unchecked use of the strcat function on a fixed size buffer, when displaying user bookmarks. This vulnerability requires authentication as a low privileged user.
Impact
An authenticated low-privileged user could exploit this vulnerability to achieve code execution as the nobody user.
Details
The sonicfiles RAC_GET_BOOKMARKS_HTML5 (RacNumber 35) method allows users list their bookmarks. This method is vulnerable to heap-based buffer-overflow, due to unchecked use of strcat.
The RAC_GET_BOOKMARKS sonicfiles method maps to the Python method get_bookmarks. This simply calls into sonicapp.api.getBookmarks:
getBookmarks is a swig wrapper into libSys.so!getFileShareBookmarks. The following screenshot shows decompilation of the getFileShareBookmarks function:
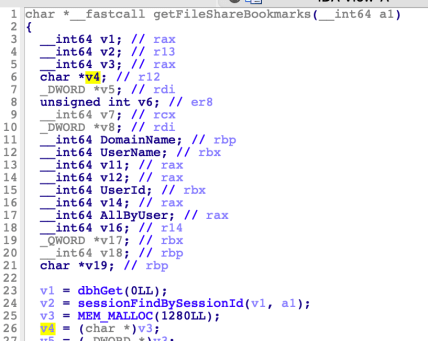
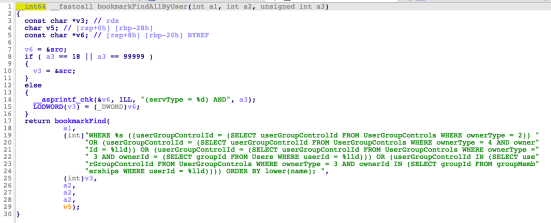
As shown above, a fixed buffer of size 1280 bytes is allocated. Later, all bookmarks for the current user (specified in the swap ID cookie) are retrieved from the database via a call to bookmarkFindAllByUser.
The following screenshot shows the SQLite query used to retrieve the list of user’s bookmarks in bookmarkFindAllByUser:
The list of bookmarks is then copied (in 128-byte chunks) into the fixed size buffer using strcat:
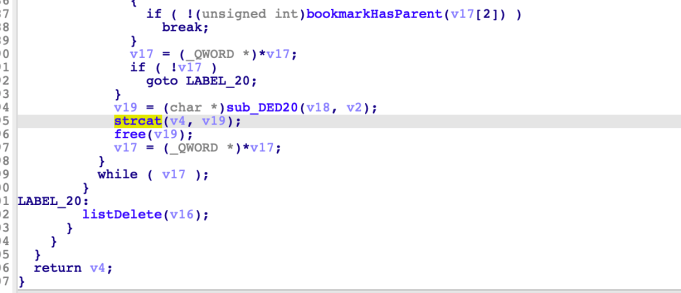
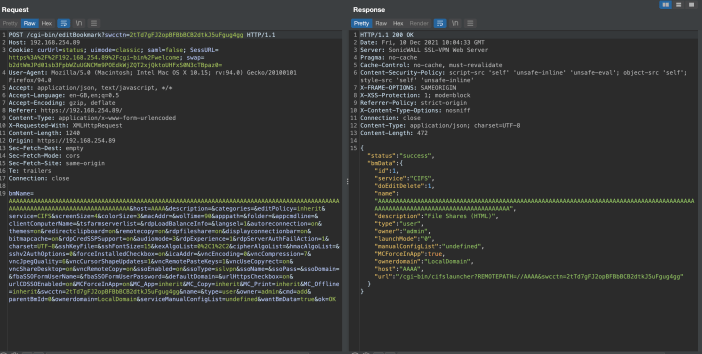
An attacker could trigger a heap-based buffer overflow by creating 11 bookmarks with a name length of 127 characters, as per the following screenshot:
Once the bookmarks are placed, the attacker could then call the sonicfiles RAC_GET_BOOKMARKS_HTML5 (RacNumber 35) method, to list the bookmarks. This results in a heap-based buffer-overflow in libSys.so!getFileShareBookmarks->strcat
This vulnerability requires a low-privileged user-level session and could result in code execution as the nobody user.
The following POST request shows the creation of a CIFS server bookmark:
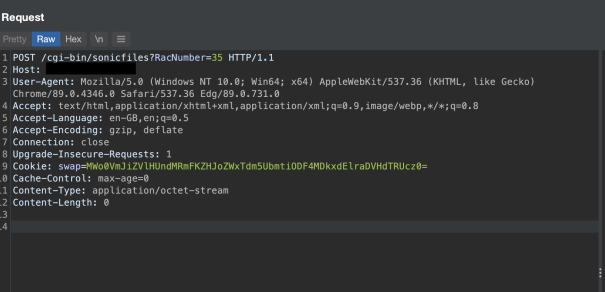
Example POST request to trigger the overflow (after creating the 11 bookmarks):
Recommendation
Upgrade to SMA version 10.2.0.9-41sv, 10.2.1.3-27sv or above.
Vendor Communication
2021-10-29 - Vulnerability reported to SonicWall PSIRT.
2021-11-02 - Acknowledgement from SonicWall PSIRT.
2021-12-01 - SonicWall request that NCC Group withhold technical details until 2022-01-11, releasing high-level advisories on 2021-12-09.
2021-12-03 - NCC Group agrees to suggested disclosure timeline.
2021-12-07 - Patch released and SonicWall publish KB article and security advisory.
2021-12-09 - NCC Group advisory released.Thanks to
Jennifer Fernick and Aaron Haymore from NCC Group for their assistance with disclosure.
About NCC Group
NCC Group is a global expert in cybersecurity and risk mitigation, working with businesses to protect their brand, value and reputation against the ever-evolving threat landscape. With our knowledge, experience and global footprint, we are best placed to help businesses identify, assess, mitigate respond to the risks they face. We are passionate about making the Internet safer and revolutionizing the way in which organizations think about cybersecurity.
Published Date: 2021-12-09
Written By: Richard Warren
